Very nice write-up on the lack of collision resistance in the Curl hash function previously used by the #IOTA cryptocurrency. Includes source code for generating collisions, formal proofs, and will be the final say in this debate. github.com/colavitam/curl… 
The paper is due to Michael Colavita and Garrett Tanzer, both of Harvard University. It appears to be original research performed independently of the paper by Heilman et al. Big thanks to @cybergibbons for bringing this to my attention.
The reddit thread on the #IOTA subreddit has only a handful of comments at the moment, but they are hilarious to read. reddit.com/r/Iota/comment… 
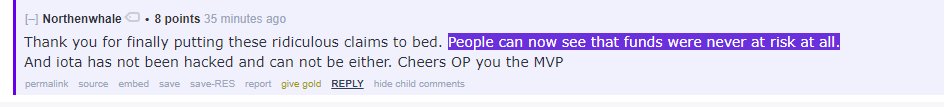
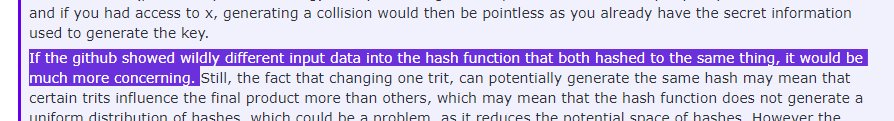
"Nah, it's not an issue because it is not finding collisions using wildly different inputs". u wot m8? 
Short paper summary 



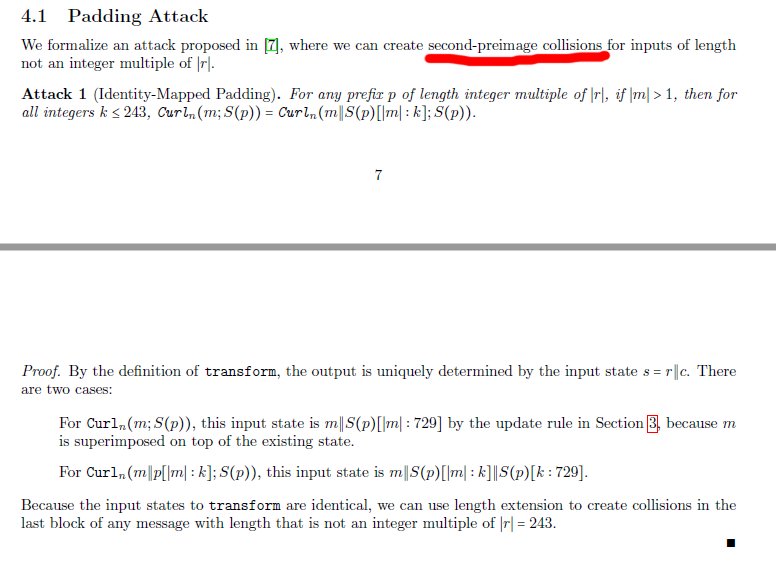
Seems like 2nd preimage resistance is partially broken, too. Since #IOTA still uses the Curl hashing function for milestone verification, could this be used to launch an attack on the network? 
Question now is if the #IOTA folks will continue the legal crusade against critics now that attack code *has* been published. Remember, they were the ones demanding code.
External Tweet loading...
If nothing shows, it may have been deleted
by @c___f___b view original on Twitter
#IOTA supporter or climate change denier? There's just no telling! 
• • •
Missing some Tweet in this thread? You can try to
force a refresh




