I wonder if #DEFCON26 just leaves discoverable BlueTooth devices around in order to see how many people try to pair with them 

Hi Marvin. #DEFCON26
(Explanation: this guy trust transmits a zillion random WiFi "beacons" pretending to be an access-point, in order to overflow monitor products like this with data)
(Explanation: this guy trust transmits a zillion random WiFi "beacons" pretending to be an access-point, in order to overflow monitor products like this with data)
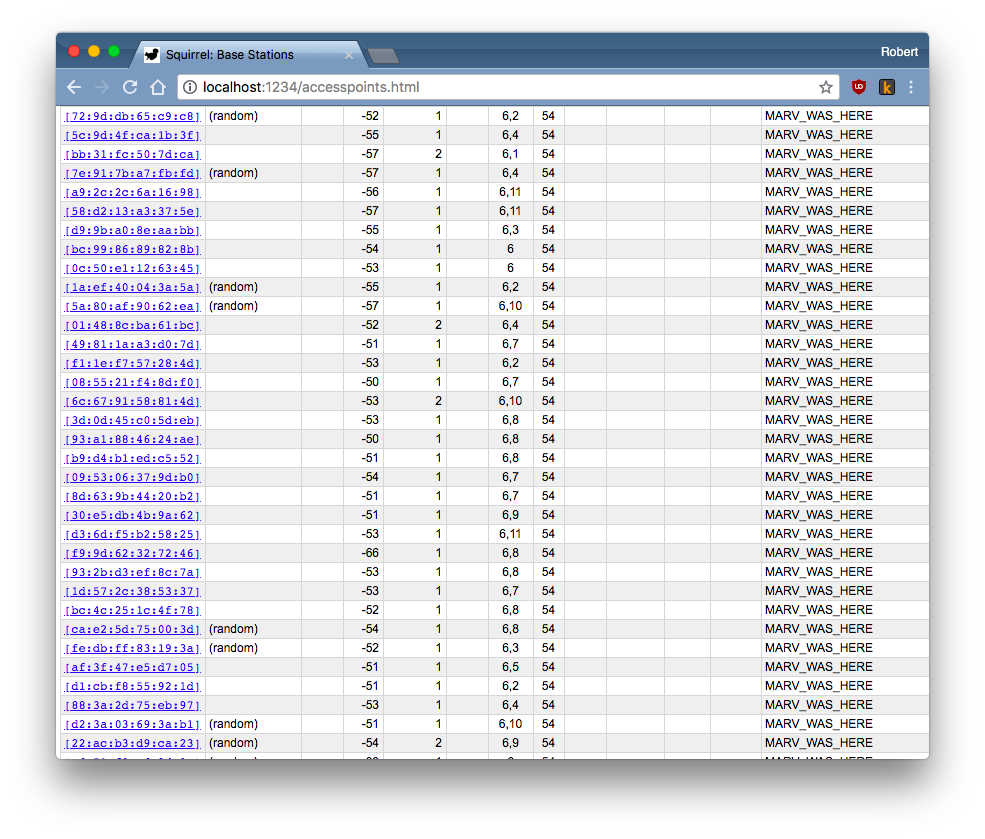
At #DEFCON26, this other guy is doing a brute-force attempt at broadcasting a zillion access-point names, hoping that your phone/laptop is automatically configured to connect to them. 
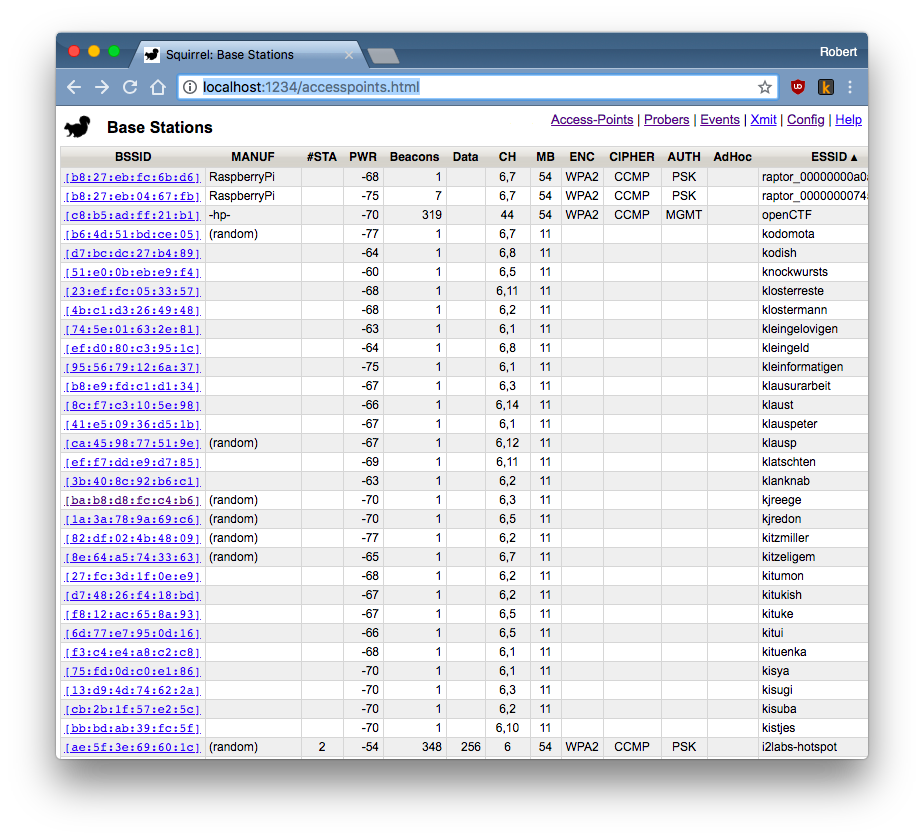
When you do it right, the #DEFCON network is safe to connect to (when you've preregistered an account and downloaded their certificate). But that doesn't mean your WiFi is secure if your machine decides to connect to a spoofed access point instead.
• • •
Missing some Tweet in this thread? You can try to
force a refresh