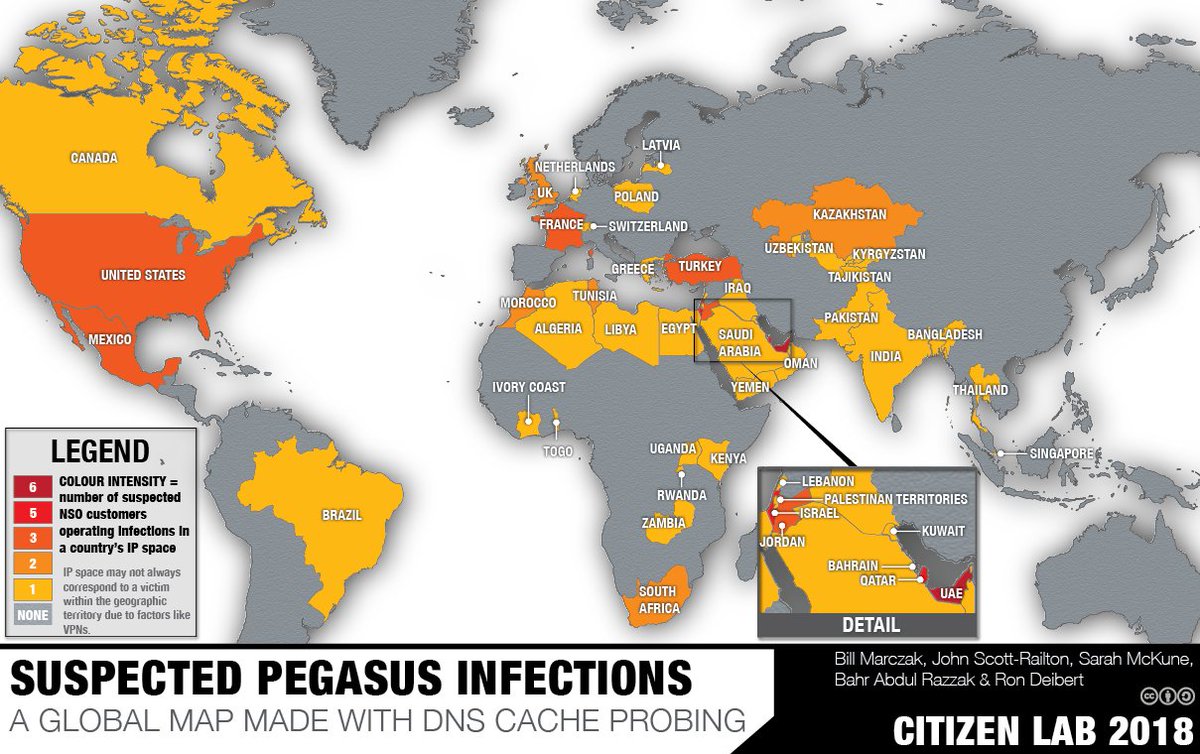
#Pegasus spyware, which transforms a cellphone into a mobile surveillance hub, could have been deployed against a range of journalists and civil society actors in Mexico, KSA, Bahrain, Morocco, Togo, Israel, US, and UAE.
How to protect yourself? [Thread]
cpj.org/2018/10/cpj-sa…
How to protect yourself? [Thread]
cpj.org/2018/10/cpj-sa…
#Pegasus gives the attacker the ability to monitor, record & collect existing & future data from the phone. This includes calls and information from messaging applications and real-time location data. The spyware is able to remotely activate the camera and microphone.
@citizenlab
@citizenlab
Pegasus is designed to be installed on phones running iOS, Android, and BlackBerry OS without alerting the target to its presence. Journalists will likely only know if their phone has been infected if the device is inspected by a tech expert.
cpj.org/2018/10/cpj-sa…
cpj.org/2018/10/cpj-sa…
Attackers create tailor-made messages that are sent to a specific journalist. These messages convey a sense of urgency and contain a link or a document which the journalist is encouraged to click on. The messages come in a variety of forms, including SMS, email, and WhatsApp.
Research by @citizenlab and @amnesty found that #Pegasus messages tend to take the following forms:
- Messages purporting to be from a known organization such as an embassy or a local news organization
- Messages that warn the target may be facing an immediate security threat
- Messages purporting to be from a known organization such as an embassy or a local news organization
- Messages that warn the target may be facing an immediate security threat
-Msgs that raise any work-related issue, such as covering an event that the target usually reports on
-Msgs that make appeals to personal matters, such as those relating to compromising photos of partners
-Financial msgs that reference purchases, credit cards, or banking details
-Msgs that make appeals to personal matters, such as those relating to compromising photos of partners
-Financial msgs that reference purchases, credit cards, or banking details
Attackers can target personal and work phones. To better protect themselves & their sources, journalists should:
- Verify the link with the sender through a different channel of communication. This should preferably be through video or voice
#journosafe
cpj.org/2018/10/cpj-sa…
- Verify the link with the sender through a different channel of communication. This should preferably be through video or voice
#journosafe
cpj.org/2018/10/cpj-sa…
If the sender is not previously known to you, secondary channels may not provide successful verification of the links, as secondary channels may be set up by the adversary as part of an elaborate cover identity.
#digitalsecurity #pegasus #cpjemergencies
cpj.org/2018/10/cpj-sa…
#digitalsecurity #pegasus #cpjemergencies
cpj.org/2018/10/cpj-sa…
If the link utilizes a URL shortener service like TinyURL/Bitly, input the link into a URL expander service. If the expanded link looks suspicious, for instance mimicking a local news website but not being quite the same, do not click the link and forward it to phishtank@cpj.org
If you feel you need to open the link, do not use your primary device. Open the link on a separate, secondary device that does not have any sensitive information or contact details, and is used solely for viewing links. Carry out a factory reset on the device regularly.
#Pegasus spyware can also be installed on your phone if an adversary gains physical access to the device. To reduce risk:
- Do not leave your device unattended and avoid handing over your phone to others
cpj.org/2018/10/cpj-sa…
- Do not leave your device unattended and avoid handing over your phone to others
cpj.org/2018/10/cpj-sa…
When crossing a border or checkpoint ensure that you can see your phone at all times Turn off the phone before arriving at the checkpoint, and have a complex passphrase consisting of both letters and numbers. Be aware that if your phone is taken then the device may be compromised
If you are a freelance journalist or a journalist that does not have access to tech support, contact the @accessnow Helpline: accessnow.org/help/
If you have received a suspicious msg & believe you may have been targeted by Pegasus, please fwd the msg to phishtank@cpj.org
If you have received a suspicious msg & believe you may have been targeted by Pegasus, please fwd the msg to phishtank@cpj.org
For more information on technology security we encourage journalists to review the CPJ's Security Guide's Chapter on Technology Security: cpj.org/reports/2012/0…
And see the digital safety information included in our Resource Center: cpj.org/emergency-resp…
#CPJEmergencies
And see the digital safety information included in our Resource Center: cpj.org/emergency-resp…
#CPJEmergencies
If you believe your phone is infected by #Pegasus immediately stop using that phone and purchase another one. You should leave the suspected device in a place that does not compromise you or your surroundings.
Illustration by @citizenlab
cpj.org/2018/10/cpj-sa…
Illustration by @citizenlab
cpj.org/2018/10/cpj-sa…
• • •
Missing some Tweet in this thread? You can try to
force a refresh




