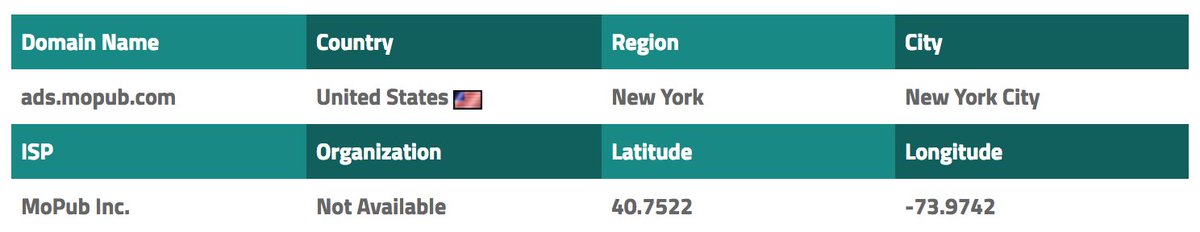
<Thread> CM Browser is a very popular application (50M - 100M downloads) published by @CheetahMobile. 
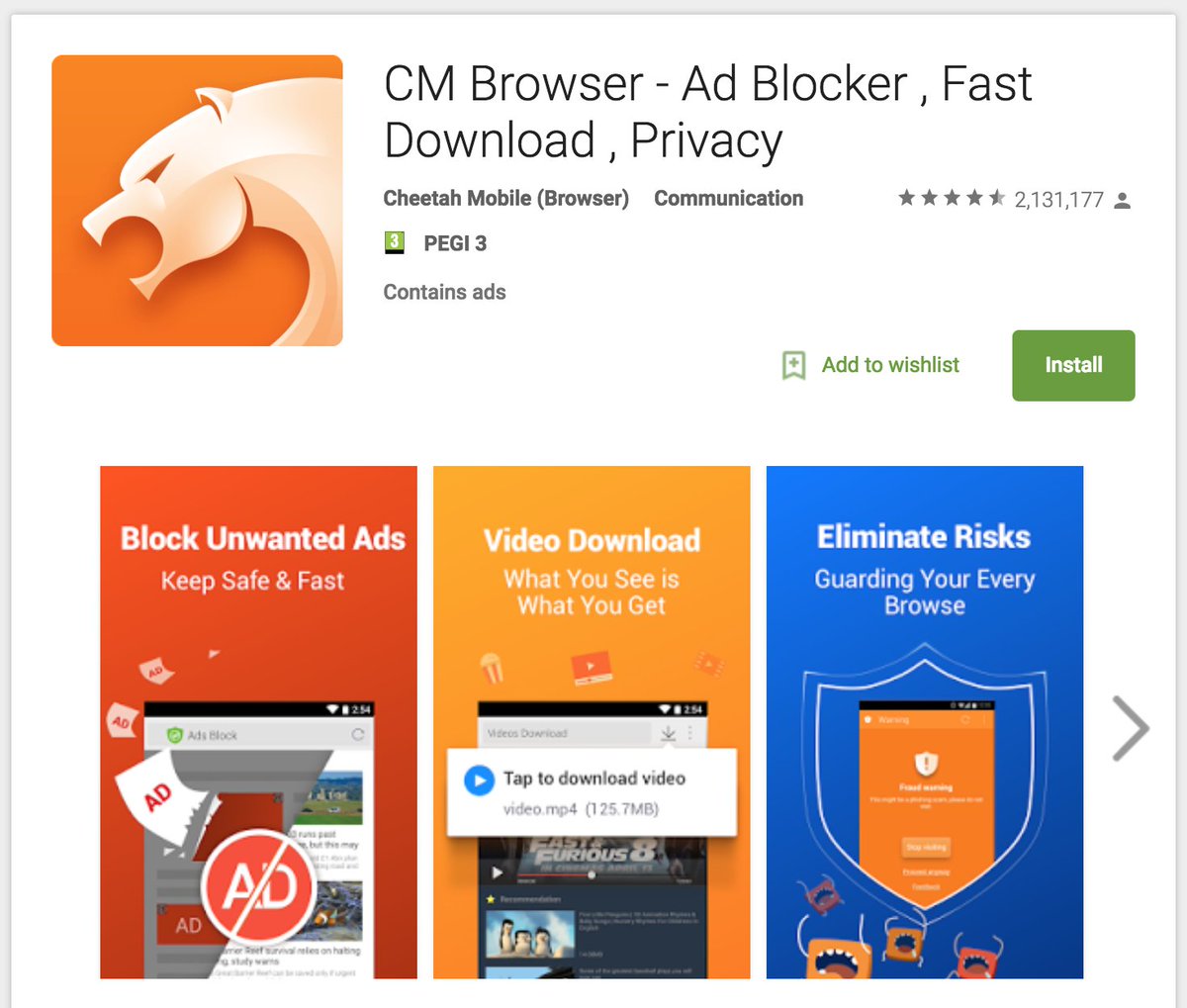
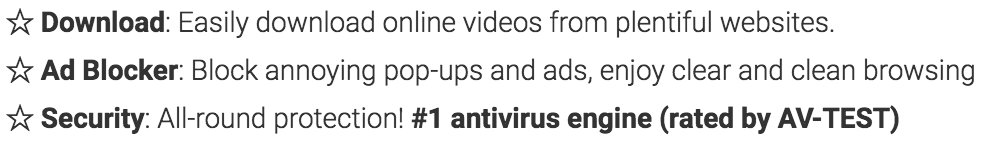
In the description it said "#1 antivirus engine (rated by AV-TEST)" which is a lie. The AV-TEST best android security 2016 award had been given to @Bitdefender and @Sophos. 


• • •
Missing some Tweet in this thread? You can try to
force a refresh