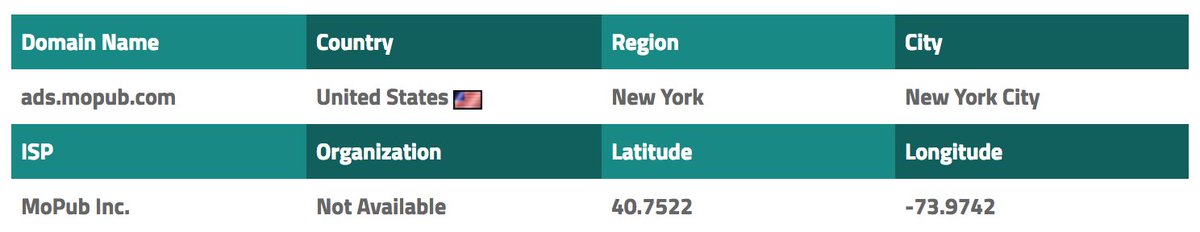
Hi #Aadhaar 👋! Can we talk about the #BenefitsOfAadhaar for the #India population?
I quickly check your #android app on the #playstore and you have some security issues...It's super easy to get the password of the local database for example...🤦♂️
play.google.com/store/apps/det…
I quickly check your #android app on the #playstore and you have some security issues...It's super easy to get the password of the local database for example...🤦♂️
play.google.com/store/apps/det…
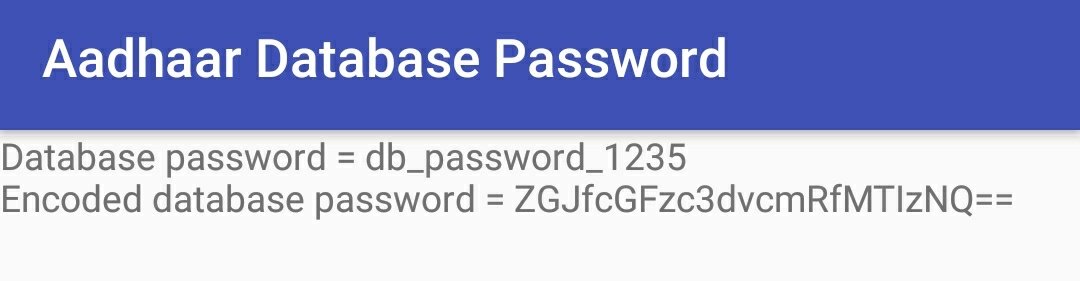
The #Aadhaar #android app is saving your biometric settings in a local database which is protected with a password. To generate the password they used a random number with 123456789 as seed and a hardcoded string db_password_123 🤦♂️ 

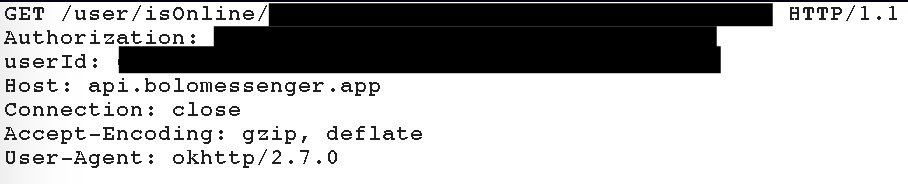
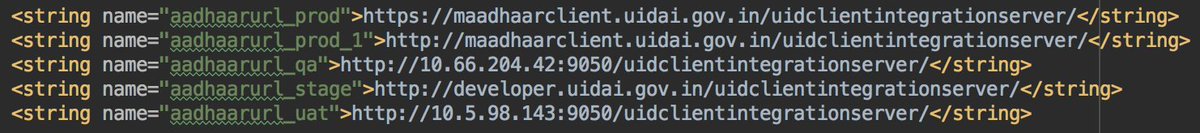
It can be good also to remove the "developer" endpoint from the release apk... 
To be continued 😏
cc @AndroidAuth @AndroidPolice @androidcentral @androidandme @Androidheadline @xdadevelopers @AndroidSPIN @TheHackersNews @verge @CNET @VICE @WIRED @JAMESWT_MHT @malwrhunterteam @hackerfantastic @LukasStefanko @ANDROIDPIT @FigaroTech @virqdroid @twandroid
Woohoo! sounds like a lot of people are interested by #Aadhaar. I know what I will do during my flight now 😁
A lot of people asking me how bad is the generation of the local database password in the #Aadhaar #android #app.
I published a small POC here: github.com/fs0c131y/Aadha…
If you start the application multiple times you will see that the generated password are always the same
I published a small POC here: github.com/fs0c131y/Aadha…
If you start the application multiple times you will see that the generated password are always the same
Storing data in a local database is a common practise in the #Android world.
In the #Aadhaar #android app they store:
- user password data (hash)
- notification
- Ki value
- EKYC Profile Data
- Biometric Prefs
- Bio Lock Timeout
- App Configuration
In the #Aadhaar #android app they store:
- user password data (hash)
- notification
- Ki value
- EKYC Profile Data
- Biometric Prefs
- Bio Lock Timeout
- App Configuration

According to the official documentation, aadhaarapi.com/aadhaar-respon…, EKYC Profile Data contains the following data:
- User_Id
- Aadhar_Id
- Name
- Dob
- Gender
- Address
- Photo
- ...
- User_Id
- Aadhar_Id
- Name
- Dob
- Gender
- Address
- Photo
- ...
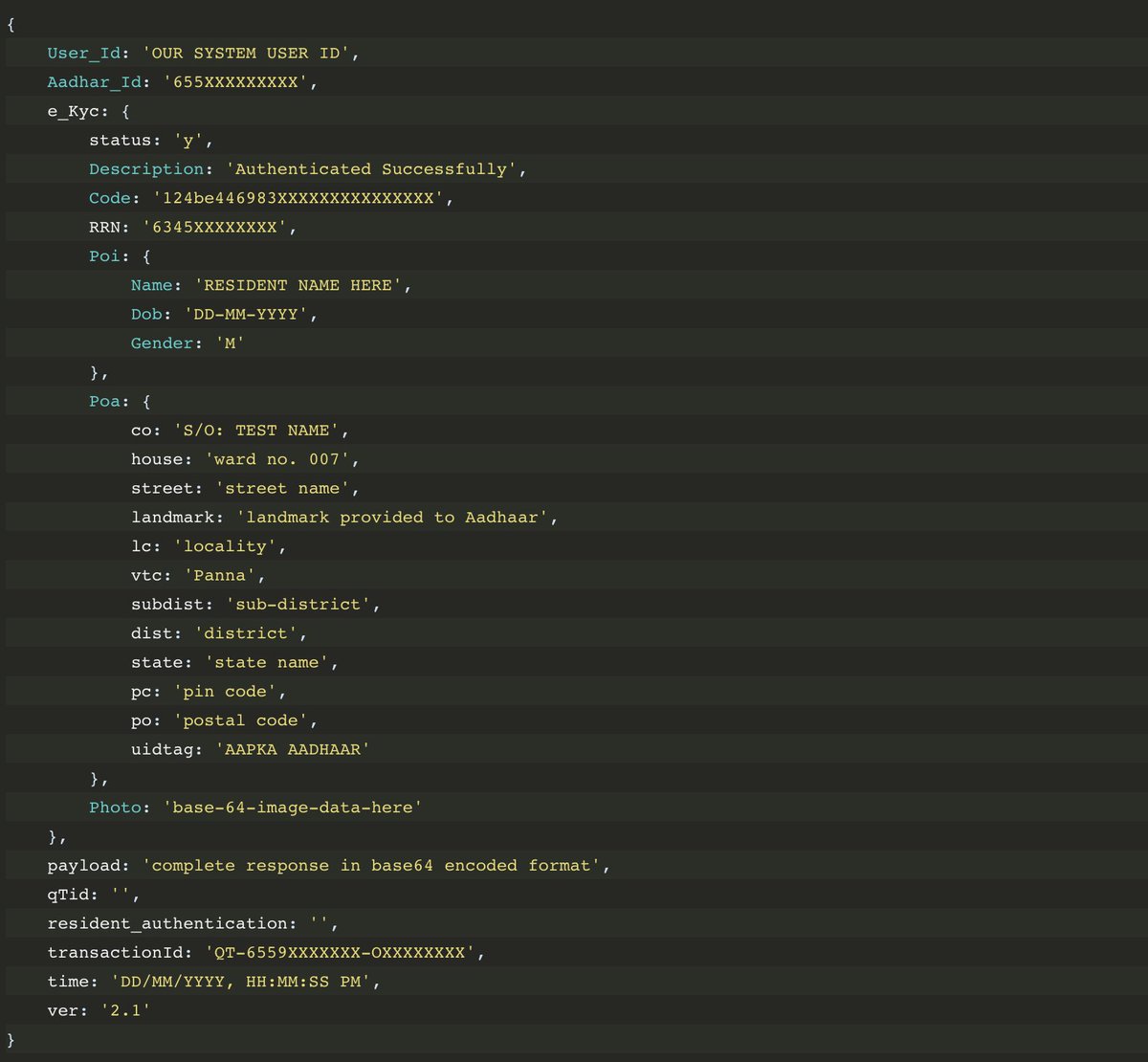
So @UIDAI you are storing a biometric data on the local database: the photo of the user.
unroll
• • •
Missing some Tweet in this thread? You can try to
force a refresh