Hi @UIDAI 👋! Do I have to explain you how real #Android developers are working?
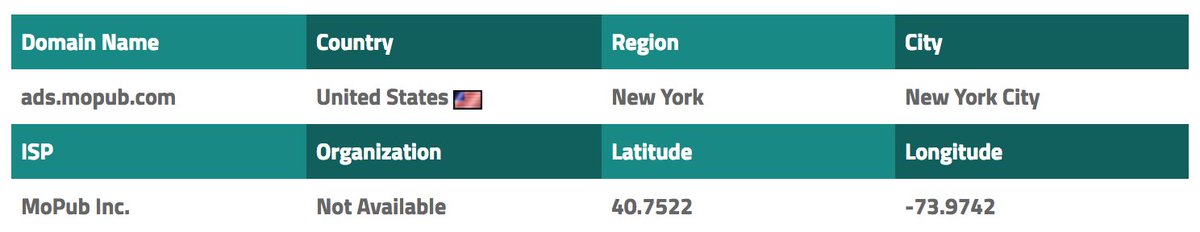
On his official #Playstore account. @UDAI published today an app called "NewTest" with blank screenshot and testingtestingtesting[...] as description 🤦♂️
#AadhaarFail
On his official #Playstore account. @UDAI published today an app called "NewTest" with blank screenshot and testingtestingtesting[...] as description 🤦♂️
#AadhaarFail
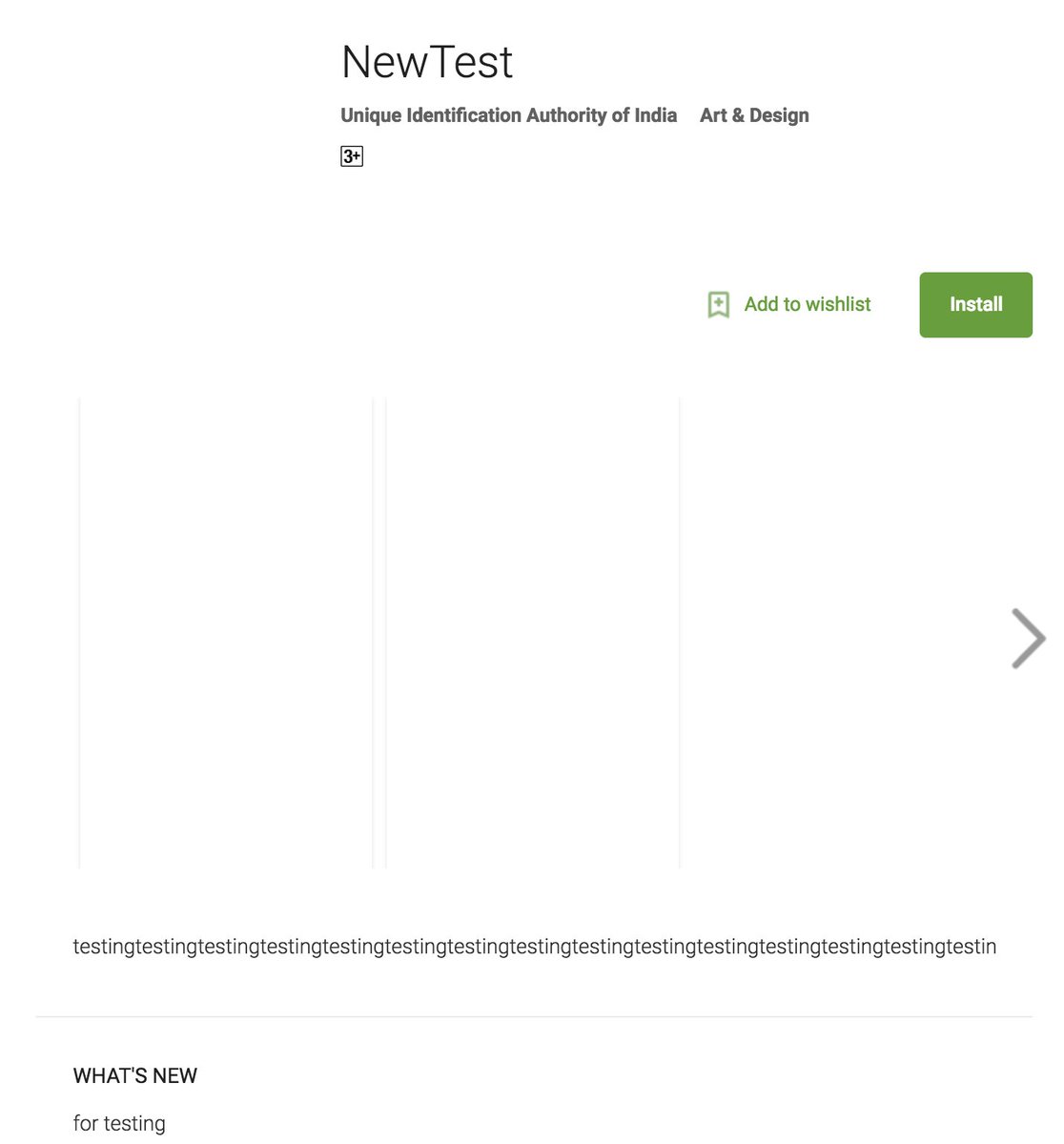
They also have a 3rd app called "testBeta (Unreleased)" 🤦♂️. Yes, they called an "Unreleased" an app released on the PlayStore 🤦♂️...
@UIDAI maybe your interns can read this link support.google.com/googleplay/and… to know how to set up an alpha/beta tests...
@UIDAI maybe your interns can read this link support.google.com/googleplay/and… to know how to set up an alpha/beta tests...
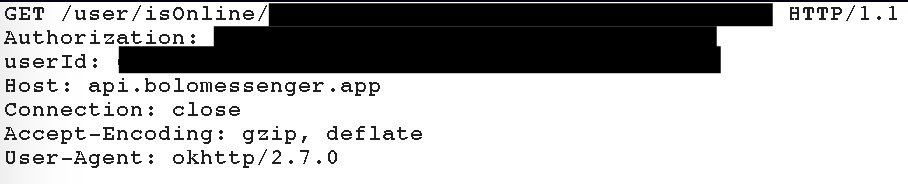
Regarding how they used their #PlayStore account, I'm pretty sure they are unable to update the official #Aadhaar #android app because they lost the release key. Please @UIDAI, show me I'm wrong
.@UIDAI shame on you, you don't even have the level for a school project
My #Indian friends, good luck, these guys have no idea of what they are doing...
My #Indian friends, good luck, these guys have no idea of what they are doing...
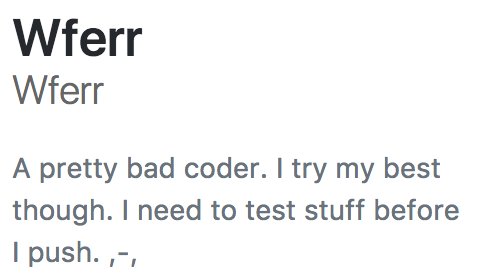
The developer section of the "NewTest" app refers to wferr.com. @rrefw you have a very good description on your #github
"A pretty bad coder. I try my best though. I need to test stuff before I push. ,-,"

"A pretty bad coder. I try my best though. I need to test stuff before I push. ,-,"
unroll
• • •
Missing some Tweet in this thread? You can try to
force a refresh