1. I'm tweeting a lot these last days, let make a quick recap
2. @Gioneeglobal, a Chinese phone maker who sell his phone in the US under the name @BLU_Product, made a phone for #NorthKorea. Afaik, they didn't make a public statement.
External Tweet loading...
If nothing shows, it may have been deleted
by @fs0c131y view original on Twitter
3. @OnePlus removed the #angela backdoor I found last November from his products
External Tweet loading...
If nothing shows, it may have been deleted
by @fs0c131y view original on Twitter
4. I published the decompiled source code of the #DPRK's RedFlag #android app.
External Tweet loading...
If nothing shows, it may have been deleted
by @fs0c131y view original on Twitter
External Tweet loading...
If nothing shows, it may have been deleted
by @fs0c131y view original on Twitter
5. I found hundreds of infected #android apps with a #Coinhive miner: cdn.androidapk.world/downloads. The site is still up.
External Tweet loading...
If nothing shows, it may have been deleted
by @fs0c131y view original on Twitter
6. @makemytrip is tracking his users without their consent. 8 days after this tweet, they didn't make a public statement or contact me.
External Tweet loading...
If nothing shows, it may have been deleted
by @fs0c131y view original on Twitter
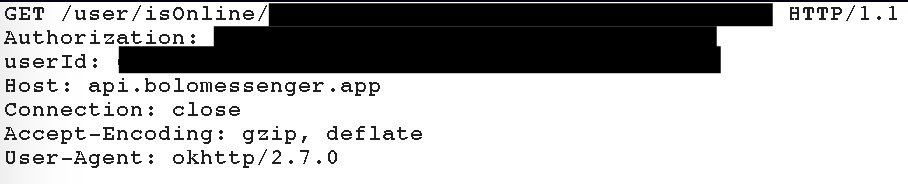
7. The password of local database in the official #Aadhaar #android app is always the same. 7 days after, @UIDAI didn't make a public statement or contact me.
External Tweet loading...
If nothing shows, it may have been deleted
by @fs0c131y view original on Twitter
External Tweet loading...
If nothing shows, it may have been deleted
by @fs0c131y view original on Twitter
8. @UIDAI don't know how to sign an app correctly. They didn't make a public statement or contact me.
External Tweet loading...
If nothing shows, it may have been deleted
by @fs0c131y view original on Twitter
9. I found 2 "test apps" on the official @UIDAI #playstore account. They didn't contact me but removed the apps few minutes after my tweets.
External Tweet loading...
If nothing shows, it may have been deleted
by @fs0c131y view original on Twitter
10. Found 2 ways to bypass the password protection in the official #Aadhaar #android app. @UIDAI didn't make a public statement or contact me.
External Tweet loading...
If nothing shows, it may have been deleted
by @fs0c131y view original on Twitter
External Tweet loading...
If nothing shows, it may have been deleted
by @fs0c131y view original on Twitter
11. After caught a basic Git error made by @aadhaar_bridge (@KhoslaLabs). They removed their entire aadhaar-bridge repo on #Github. We had a discussion but they didn't explain why they removed it.
External Tweet loading...
If nothing shows, it may have been deleted
by @fs0c131y view original on Twitter
12. Found a security issue in the @aadhaarapi's website. They contact me and fixed the issue. I will disclose the details soon.
External Tweet loading...
If nothing shows, it may have been deleted
by @fs0c131y view original on Twitter
13. Another bug in the #Aadhaar app. @UIDAI didn't make a public statement or contact me.
External Tweet loading...
If nothing shows, it may have been deleted
by @fs0c131y view original on Twitter
14. I found 100 malwares signed with the private key of @lorensiuswlt. He contacted me and denied to be the author. He said he uploaded his private key on the web few years ago.
External Tweet loading...
If nothing shows, it may have been deleted
by @fs0c131y view original on Twitter
15. I found a #coinhive script on the @lorensiuswlt's website. He contacted me and took his website offline.
External Tweet loading...
If nothing shows, it may have been deleted
by @fs0c131y view original on Twitter
16. @safelyfiled which keep sensitive docs, records, assets and directives digitally #secure is vulnerable to a basic #XSS. They didn't make a public statement or contact me.
External Tweet loading...
If nothing shows, it may have been deleted
by @fs0c131y view original on Twitter
17. @NewIndianXpress, an #Indian newspaper is vulnerable to a basic #XSS. They did not make a public statement or contact me.
External Tweet loading...
If nothing shows, it may have been deleted
by @fs0c131y view original on Twitter
All this work had been done for free (am I stupid 🤔?), if you want to support my research and pay me the coffee, feel free to send me BTC to this address 382rGcim5vDpztHyy9EDnvtLuAAasJHrEi
• • •
Missing some Tweet in this thread? You can try to
force a refresh