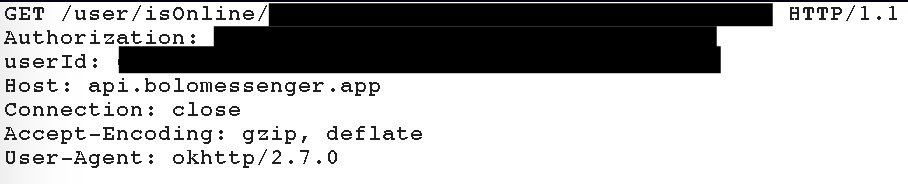
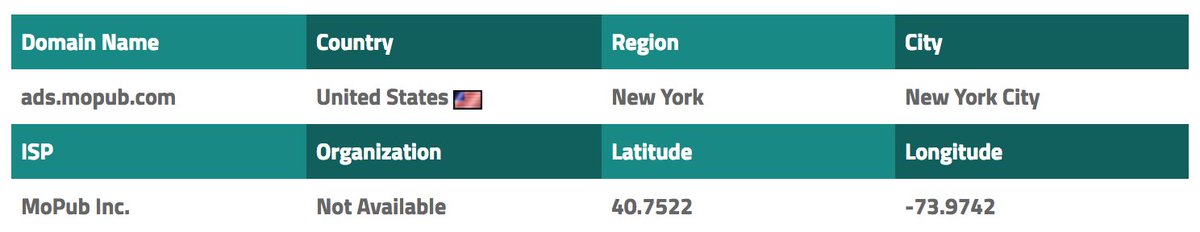
The official #Aadhaar #android app is sending an SMS to authenticate the user. In general, to avoid abuses, you add a sending rate limit. The user has to wait 2 minutes before resend the SMS. @UIDAI did not implement this kind of limit in the app. What are the consequences?
An attacker can extract the authentication HTTPS request made by the official #Aadhaar #android app. After that he just has to write a small script which will try all the possible #Aadhaar numbers.
The attacker will be able to flood the all #India population and @UIDAI will lose a lot of money.
.@UDAI don't be stupid, remove the official #Aadhaar #android app from the PlayStore, this is the best move you have.
.@UDAI don't be stupid, remove the official #Aadhaar #android app from the PlayStore, this is the best move you have.
• • •
Missing some Tweet in this thread? You can try to
force a refresh