The @OnePlus #clipboard app contains a strange file called badword.txt 🤔
In these words, we can find: Chairman, Vice President, Deputy Director, Associate Professor, Deputy Heads, General, Private Message, shipping, Address, email, ...
pastebin.com/kfvJWKJB

In these words, we can find: Chairman, Vice President, Deputy Director, Associate Professor, Deputy Heads, General, Private Message, shipping, Address, email, ...
pastebin.com/kfvJWKJB
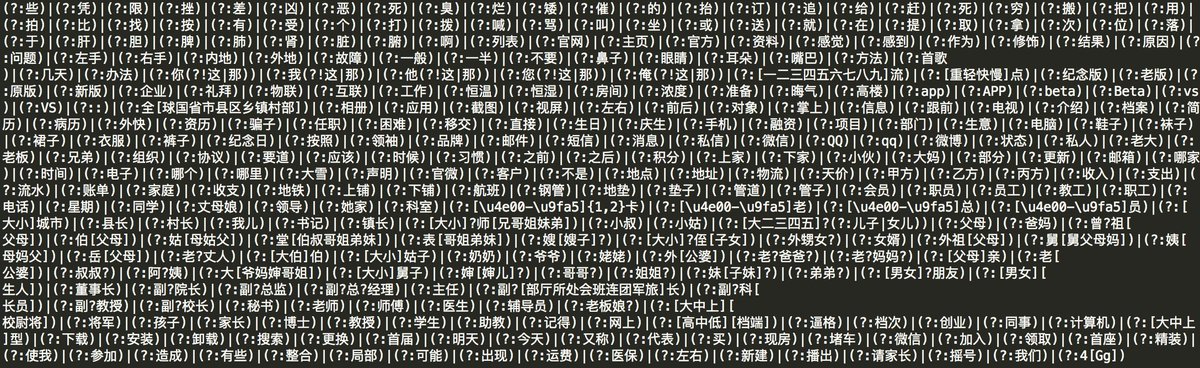
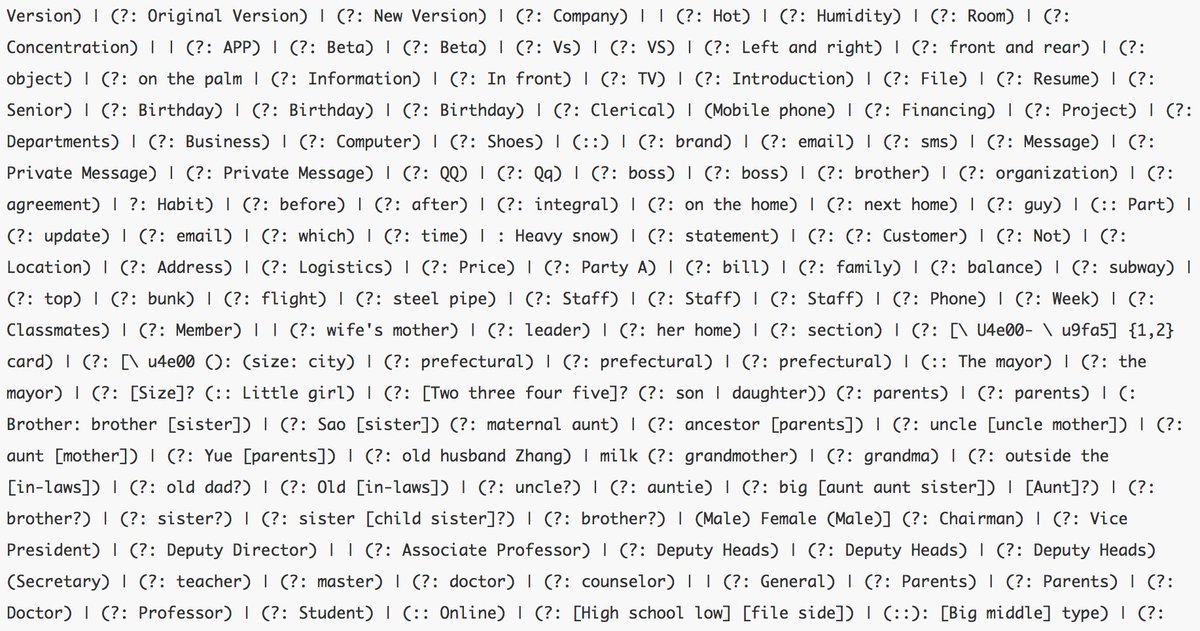
This badword.txt is duplicated in a zip file called pattern. This archive contains 7 files:
- badword.txt
- brackets.txt
- end.txt
- follow.txt
- key.txt
- start.txt
- badword.txt
- brackets.txt
- end.txt
- follow.txt
- key.txt
- start.txt
All these files are used in a obfuscated package which seems to be an #Android library from teddymobile
TeddyMobile is a Chinese company, they worked with a lot of manufacturers including @oppo.
teddymobile.cn
teddymobile.cn

As far as I understand, teddymobile is making number identification in SMS
The picture below can be translated like this:
- Total number of SMS 20M+
- SMS identification accuracy 100%
- Identification number recognition rate of 70%
- recognition accuracy of 95%
The picture below can be translated like this:
- Total number of SMS 20M+
- SMS identification accuracy 100%
- Identification number recognition rate of 70%
- recognition accuracy of 95%

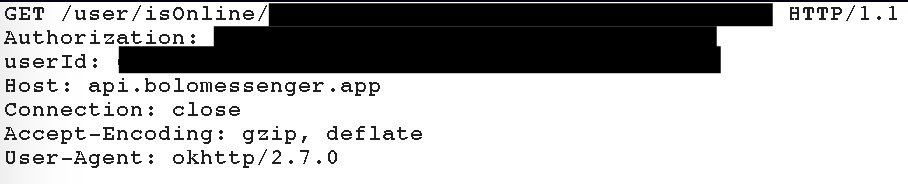
According to the code @OnePlus is sending your IMEI and the phone manufacturer to a Chinese server owned by teddymobile 😡 
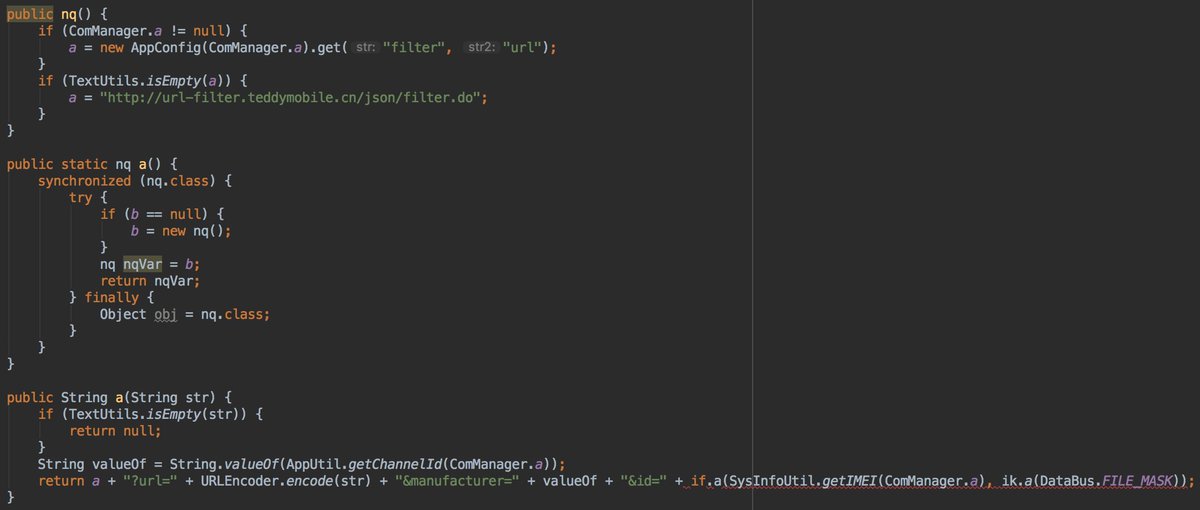
In the TeddyMobile's package com.ted, they have a class called SysInfoUtil. This class contains the following methods:
- getAndroidID
- getCPUSerial
- getDeviceId
- getHardwareSerialNumber
- getIMEI
- getIPAddress
- getMacAddress
- getPhoneNumbe
- getScreenPixels
- getAndroidID
- getCPUSerial
- getDeviceId
- getHardwareSerialNumber
- getIMEI
- getIPAddress
- getMacAddress
- getPhoneNumbe
- getScreenPixels
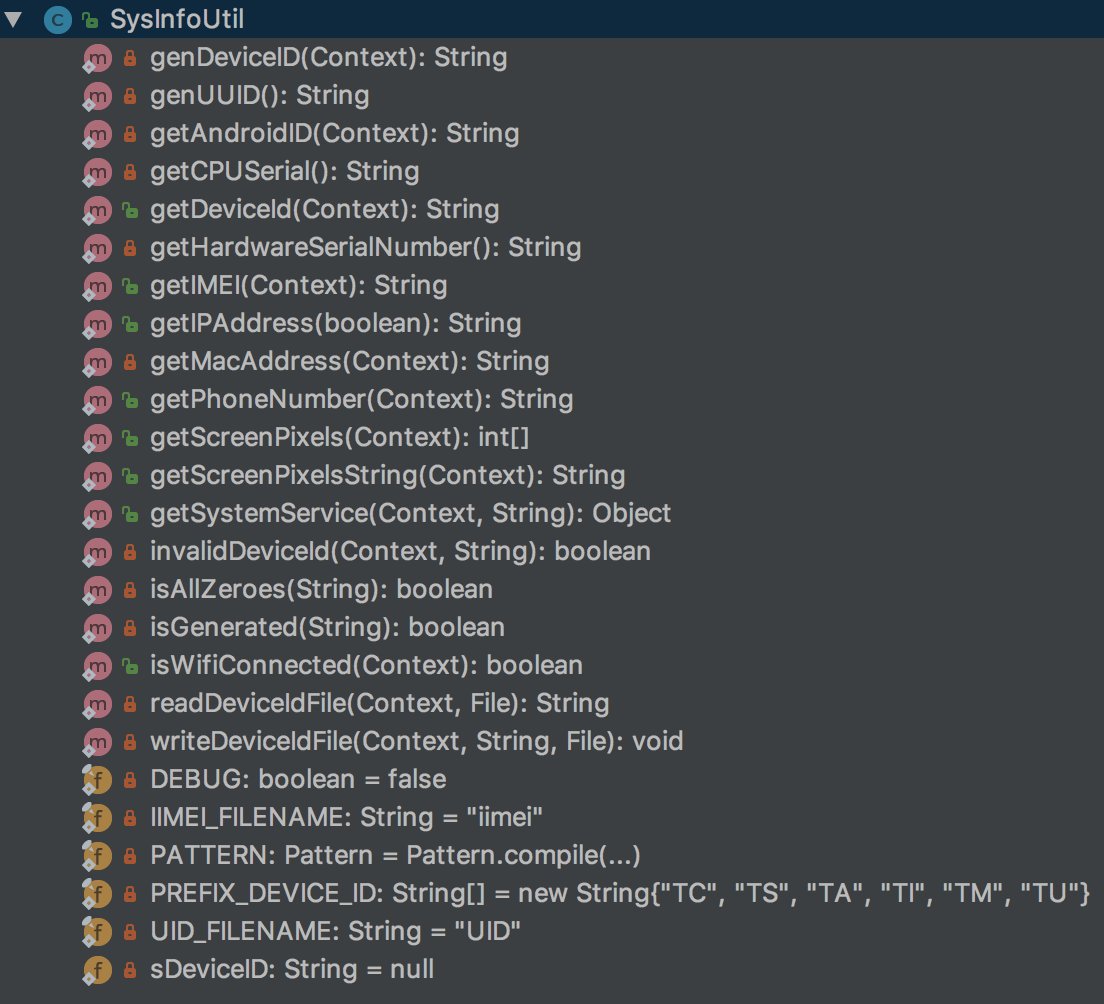
Except getIPAddress and getScreenPixels, all the other methods are used.
They also send JSON messages to their servers with a "telephone" and "messageText" fields...😡
They also send JSON messages to their servers with a "telephone" and "messageText" fields...😡
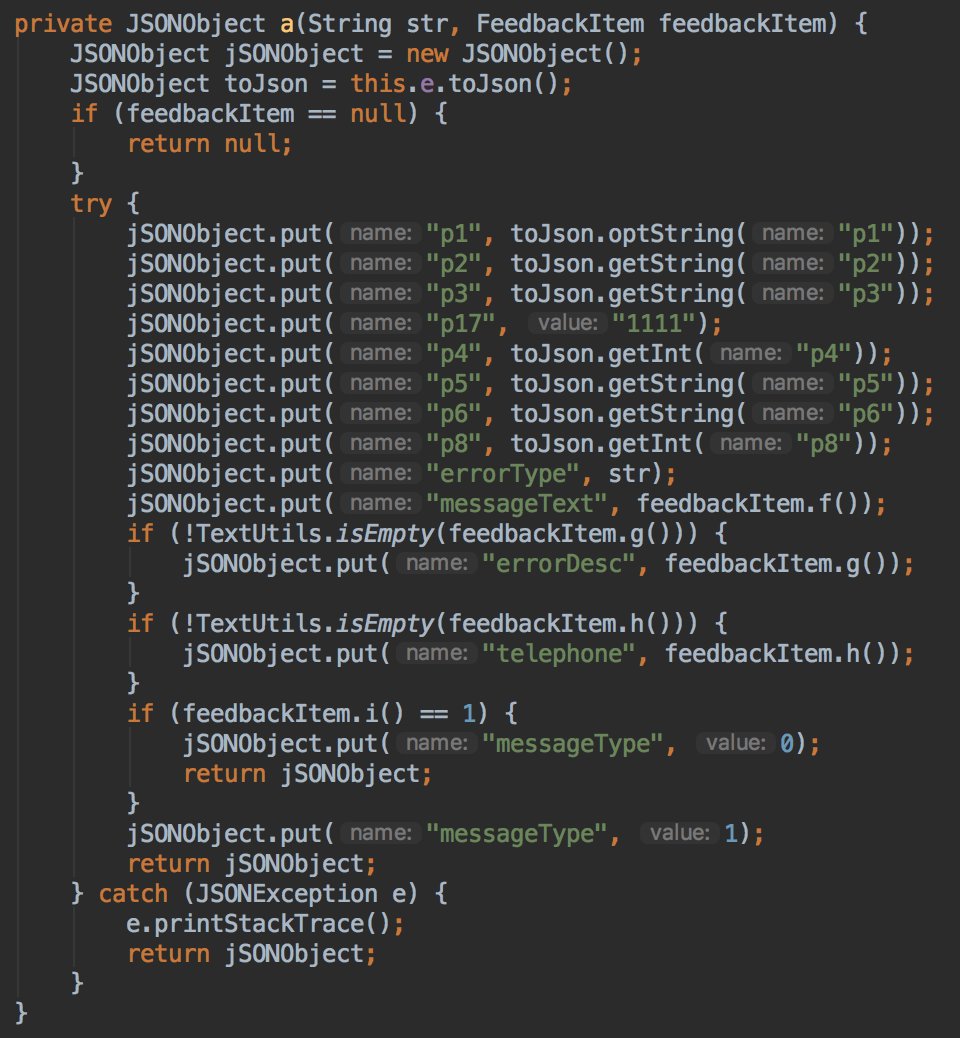
This is a good reminder...Please don't copy paste your bank account number...TeddyMobile has a dedicated method to recognize a bank account...😡 
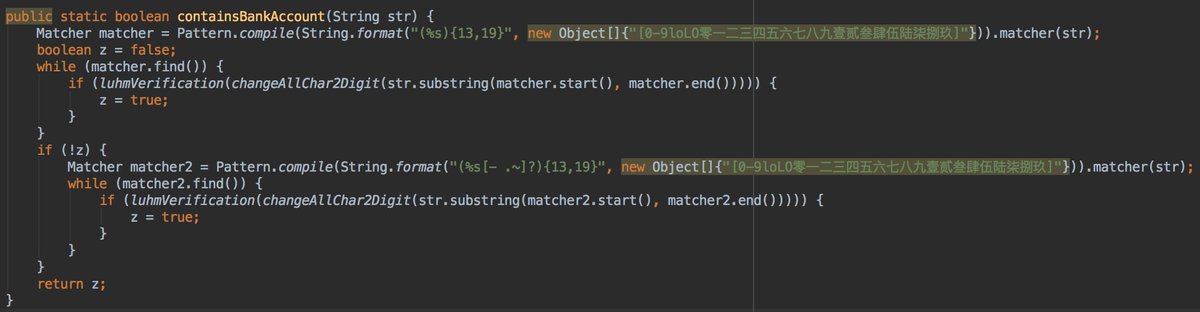
I didn't manage to trigger the network communications to the teddymobile servers but I will continue later. Moreover, I have other ideas in mind regarding this app 😉
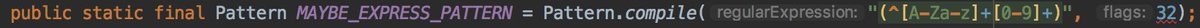
After deeper investigation only a small part of the tedmobile sdk is used. In the ClipboardManager, in the verifyExpress method they used the method parserOnline.

External Tweet loading...
If nothing shows, it may have been deleted
by @fs0c131y view original on Twitter
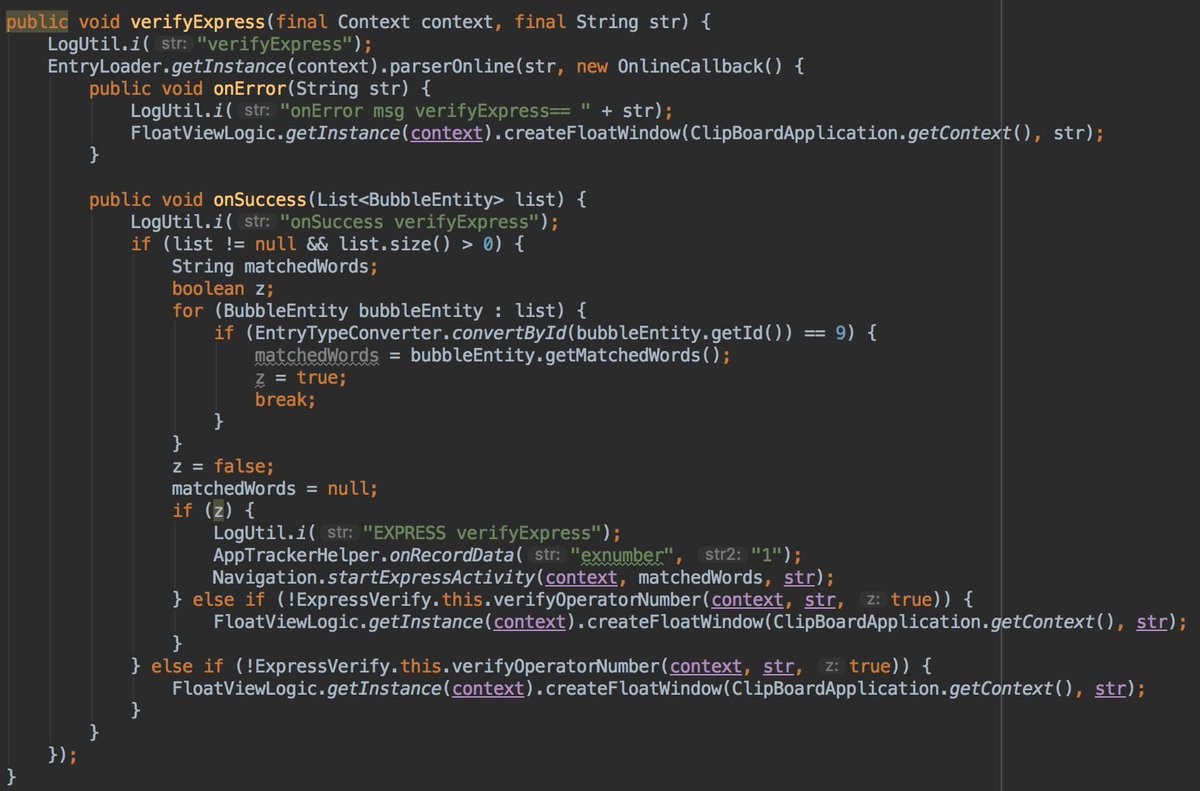
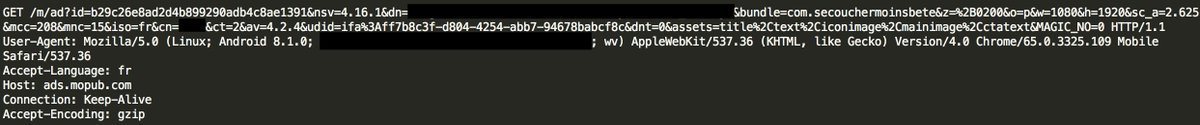
This parserOnline will send what you have in your clipboard to a teddymobile server in order to parse it. It important to say that this method is used only for Chinese users. 


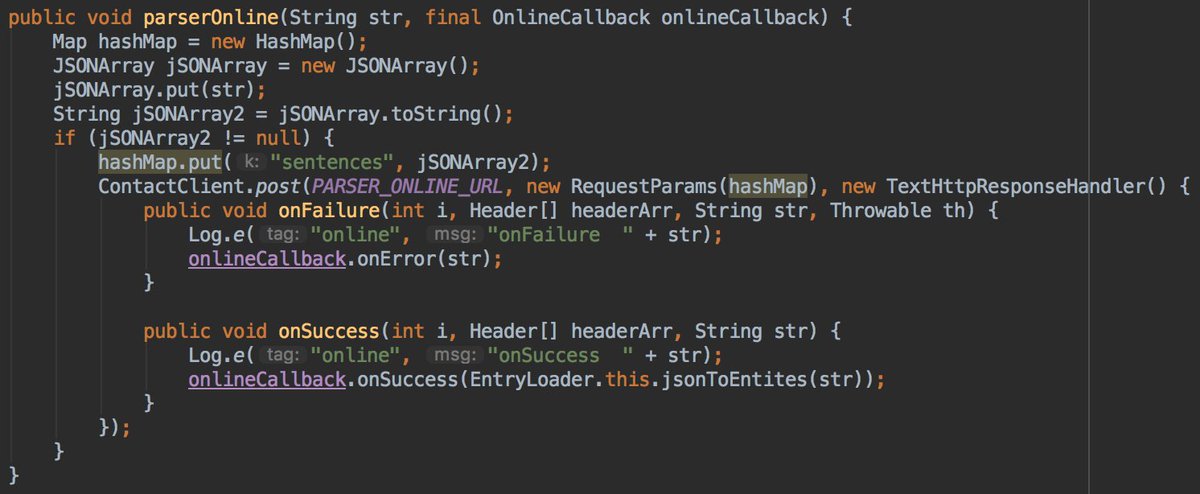
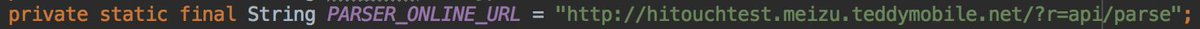
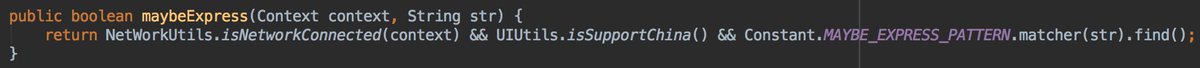
So we can definitively say that clipboard data of @OnePlus Chinese users is send to teddymobile servers without their consent.
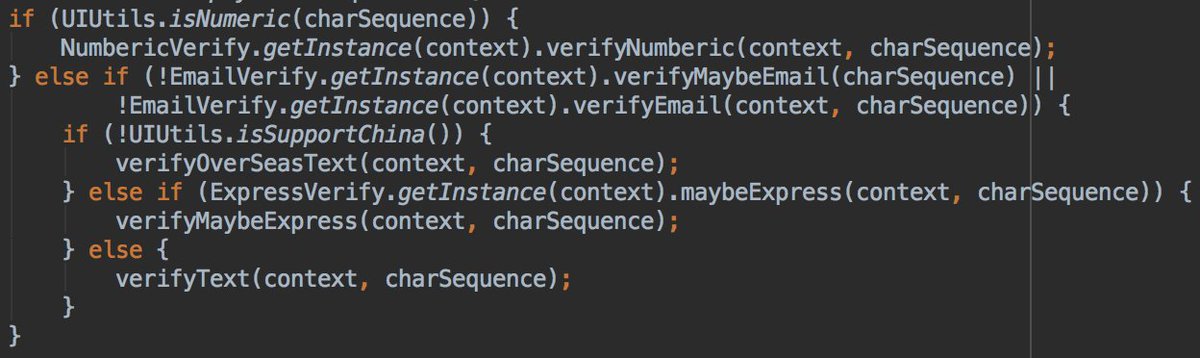
The conditions to send your data to teddymobile server are:
- clip data is not numeric
- not an email
- Chinese @OnePlus phone
- clipboard data matched the express pattern.
It good to say that parserOnline method is used 3 times in the code, so this is only 1 of the 3 usecases

- clip data is not numeric
- not an email
- Chinese @OnePlus phone
- clipboard data matched the express pattern.
It good to say that parserOnline method is used 3 times in the code, so this is only 1 of the 3 usecases
• • •
Missing some Tweet in this thread? You can try to
force a refresh