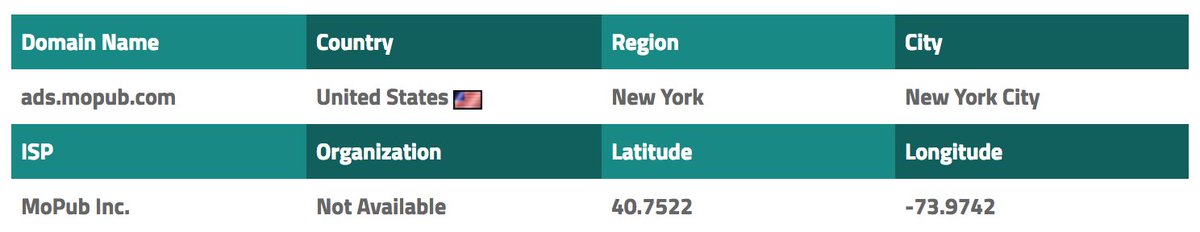
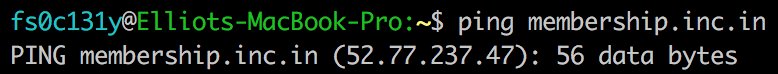
When you apply for membership in the official @INCIndia #android #app, your personal data are send encoded through a HTTP request to membership.inc.in. 
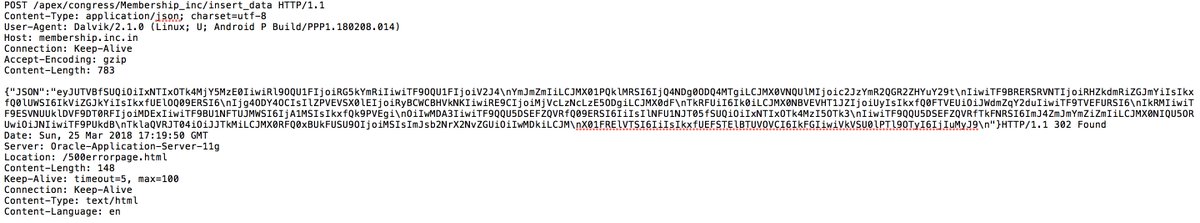
Come on! HTTP?! I'm sure you are able to rectify this and use HTTPS instead.
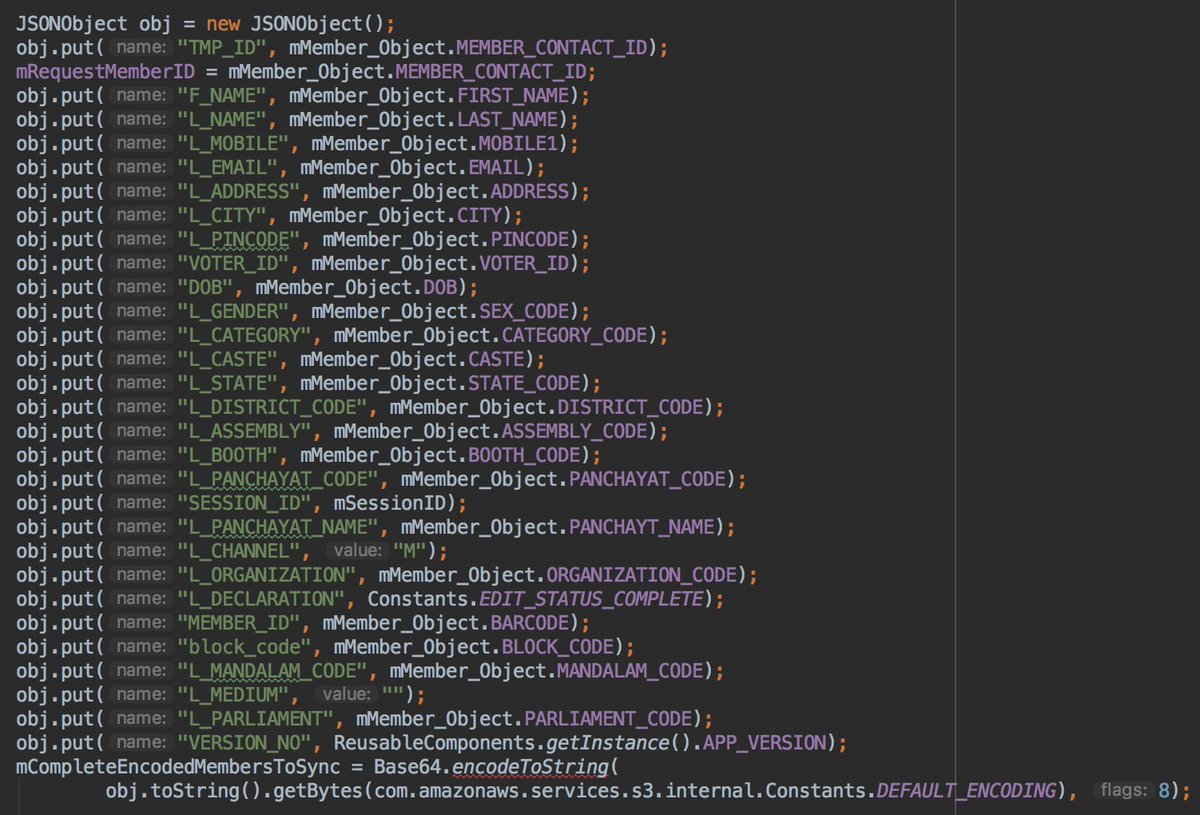
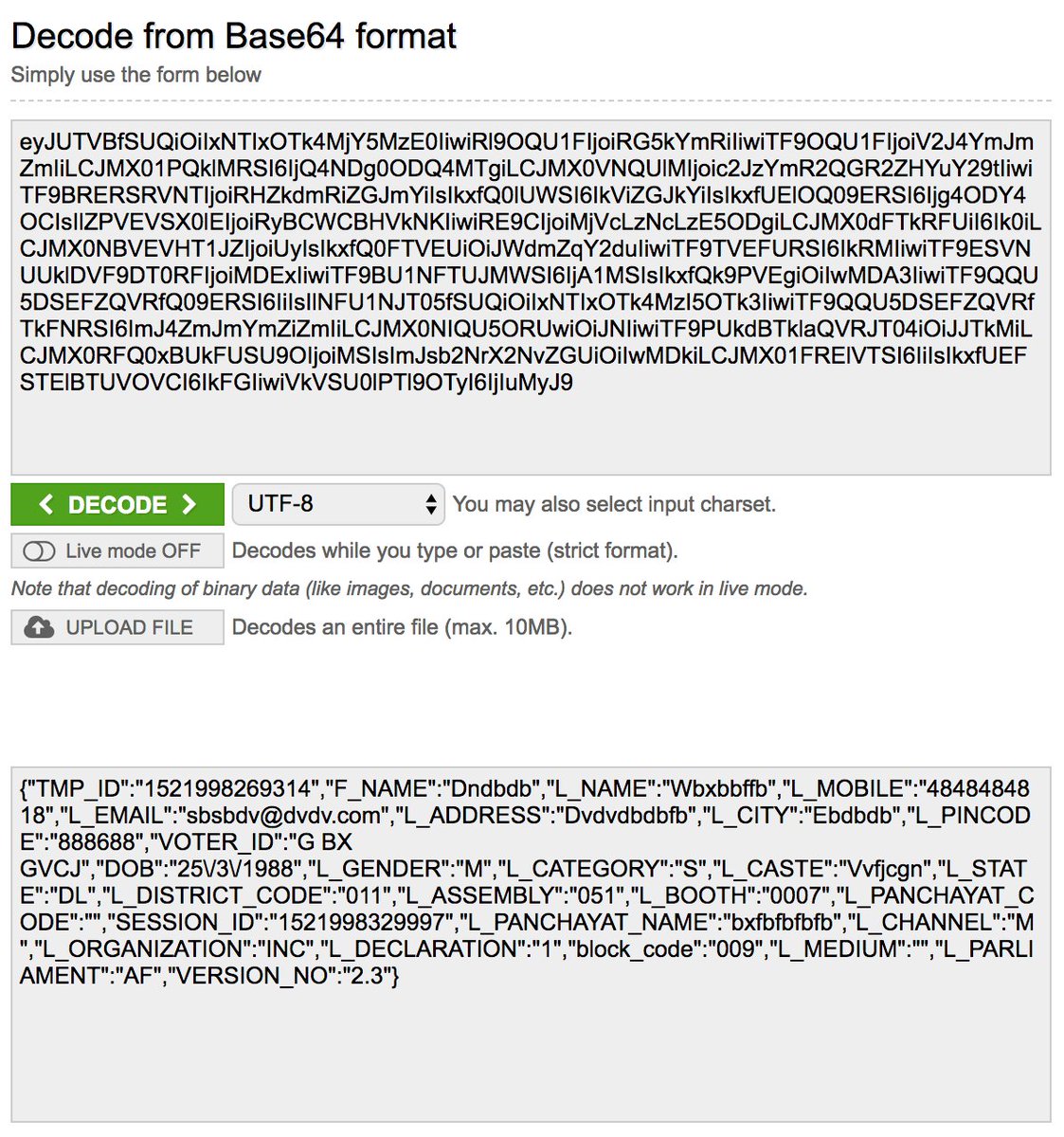
Moreover, the personal data are encoding with base 64. This is not encryption! Decode this data is very easy as shown in the example. 

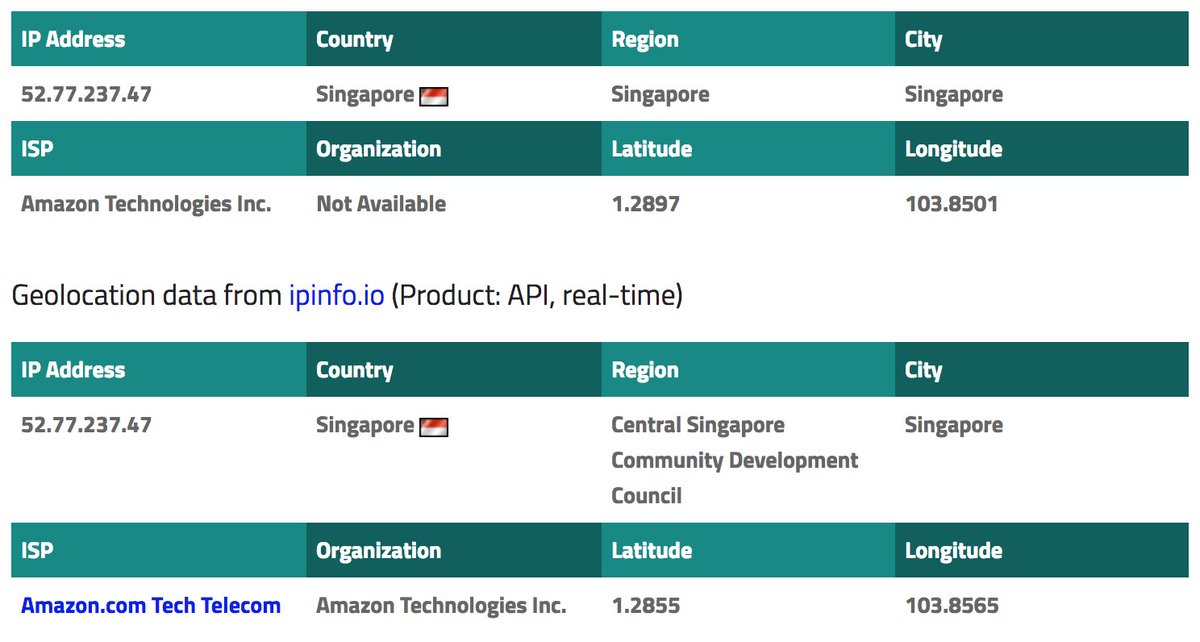
The IP address of membership.inc.in is 52.77.237.47. This server is located in Singapore. As you are an #Indian political party, having your server in #India is probably a good idea. 

• • •
Missing some Tweet in this thread? You can try to
force a refresh