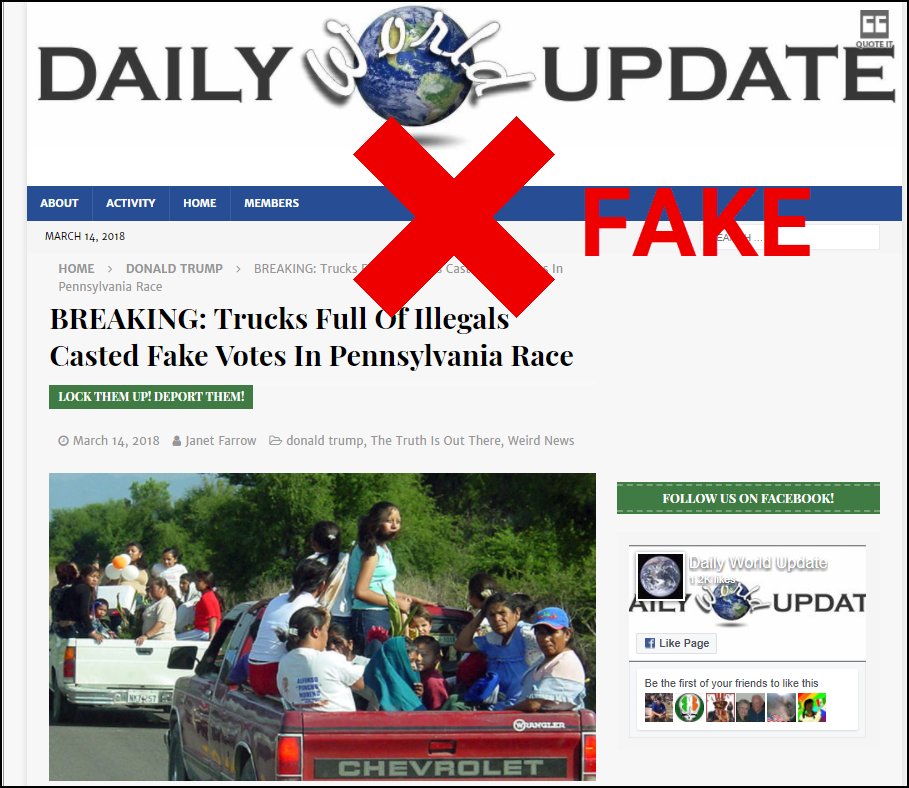
#Teachers: Here's a thread laying out how to create a digital forensics learning pathway using this false quote meme featuring Denzel Washington that recirculated last week: 
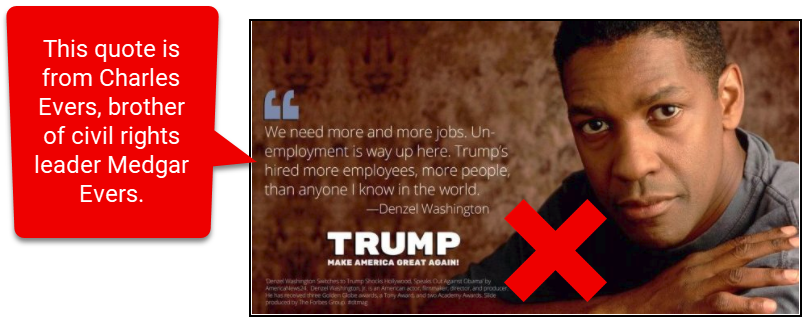
Before you get students started on their digital forensics work, you might point out the misinformation pattern it fits. This rumor has gone viral three separate times: first during the 2016 campaign, then again after Washington was nominated for an Oscar in February 2018, and...
...then again last week when Kanye West's tweeted statement of support for President Trump sparked a broader conversation about the political loyalties of the African American community. So one lesson here is that viral rumors recirculate when new contexts for them emerge.
Okay, so back to our digital forensics and fact checking exercise. Here's one way you might structure that.
1. Share this archived link to an unreliable blog post built around this false quote -- but don't give students any hints as to its accuracy. They have to figure this out on their own.
archive.is/vzFk1
archive.is/vzFk1
2. In groups or individually, challenge students to first figure out if Washington actually said what the graphic at the top attributes to him. [He didn't.] Let the first person/group to get the right answer explain how they found it.
3. Next up: Is this quote entirely made up or did someone else actually say it? [It was Charles Evers, the brother of Medgar Evers, who said it.] Again, let the first person/group with the answer share it.
4. Who do you think runs this website? Can we find out? [Students may suggest looking at the About page. Let them come up empty. A student may know about website registrations and WHOIS, but if not introduce the concept & illustrate using this site as an example.]
4 (cont'd): I get the best results for this particular search from GoDaddy's WHOIS search portal for some reason. godaddy.com/whois But you should also show students others, like the ICANN WHOIS portal (whois.icann.org/en) and whois.net
4 (cont'd): Here's the registration info for usalibertypress.com, the website we started with: goo.gl/zC8BWm 
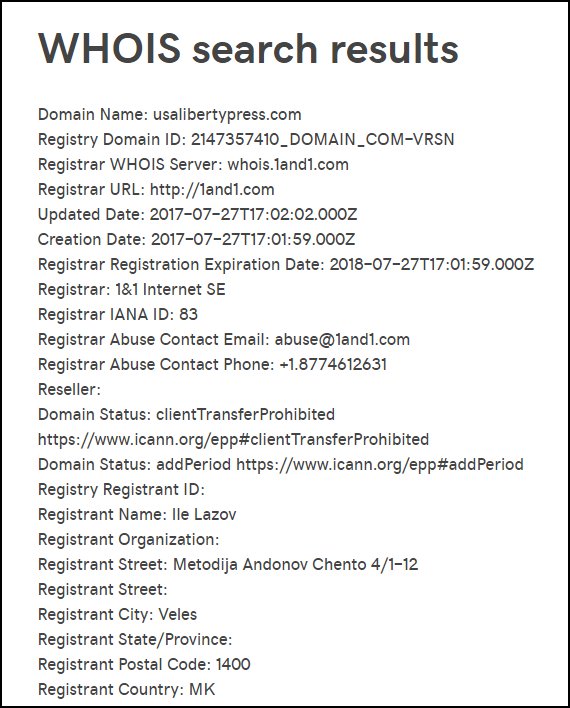
5. Have students reflect on the registration details. What's interesting about this? What questions do they have? [Collect and save those questions.]
6. [Display the false Denzel meme using a projector.] Okay, now use your observational skills on this meme. What else do you notice? Are there any other hints as to where this false quote came from? [Elicit attention to the small text in the bottom left corner.] 

7. This is too small for us to really read. What can we do to remedy that? [If a student has a method, let them share. If not, introduce two tools: using CTRL + to zoom up on a webpage or image in most applications and an image magnifier like Forensically] 29a.ch/photo-forensic…
8. Okay, who can get a clear image and read the text out to the class? 

9. What new questions do you have? [Elicit question about apparent source "AmericaNews24"] 

10. Next challenge on the pathway: What is AmericaNews24's homepage URL? Please try to get this answer without actually loading the page (to avoid giving what is very likely an unreliable site additional web traffic). [Answer:
11. Without actually loading the page, who can get a screenshot of the story on AmericaNews24. [Answer in image here:] 
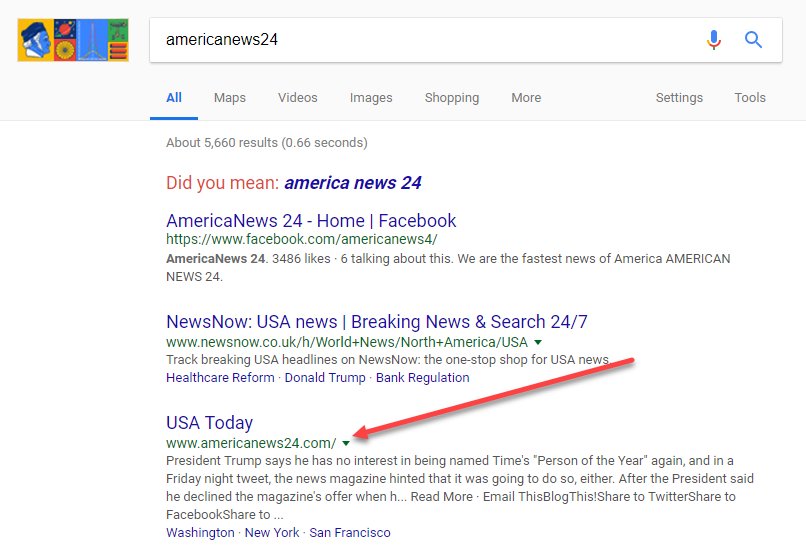
12. Who registered americanews24.com? [Answer from WHOIS query in image and link here: goo.gl/jxh4W7] 
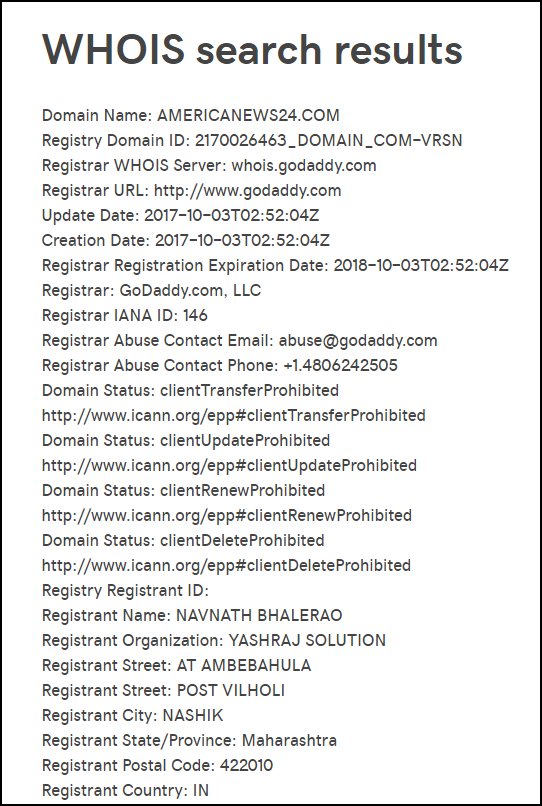
13. Who can use Google Streetview to get a shot of the building at the registrant address for the first site, usalibertypress.com? [Answer in image and here: google.com/maps/@41.71787…] 

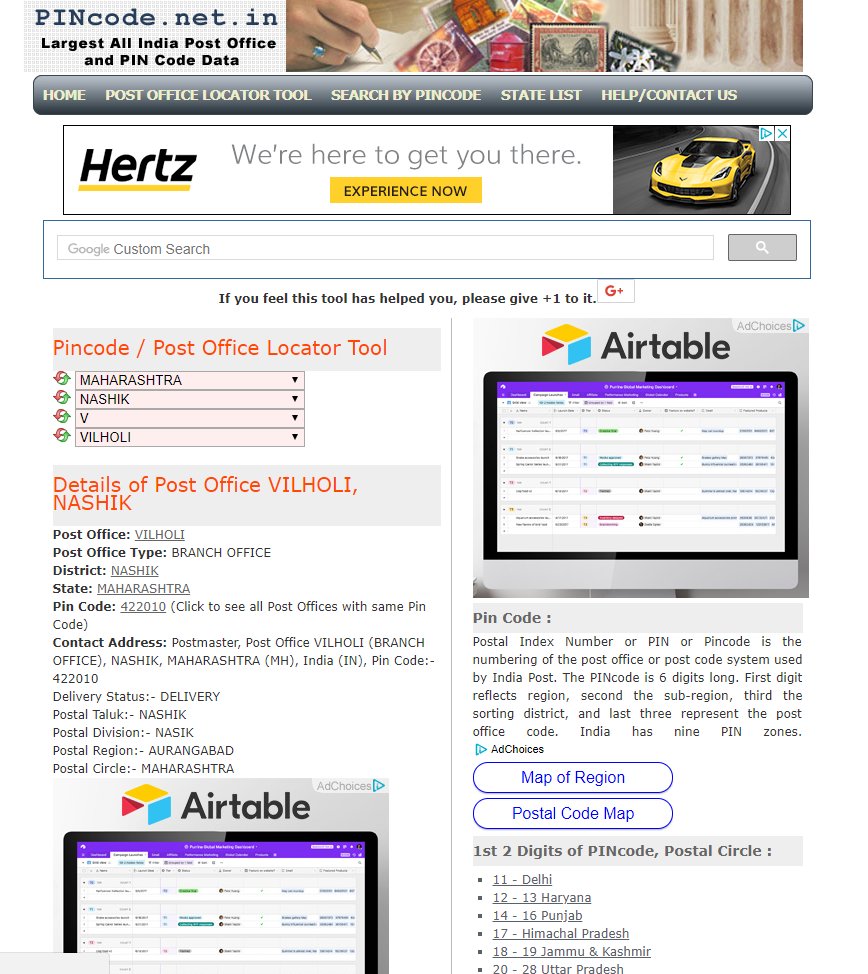
14. What is at the registrant address for the second site, americannews24.com? [Answer: a post office in Nashik, a city in the Maharashtra region in India pincode.net.in/MAHARASHTRA/NA…] 
You could stop here, or let students keep exploring. Either way, constructing these kinds of pathways as active digital forensics learning experiences is a super-engaging & empowering way to make sure students are ready to navigate & verify in the current info landscape. /END
NOTE: There’s a little bit of a mistake on steps 10 and 11. I was going to include copying a URL via right click and then pasting that link into an archiver, but decided the thread was getting long enough & excluded that without getting the thread edited back together correctly.
• • •
Missing some Tweet in this thread? You can try to
force a refresh