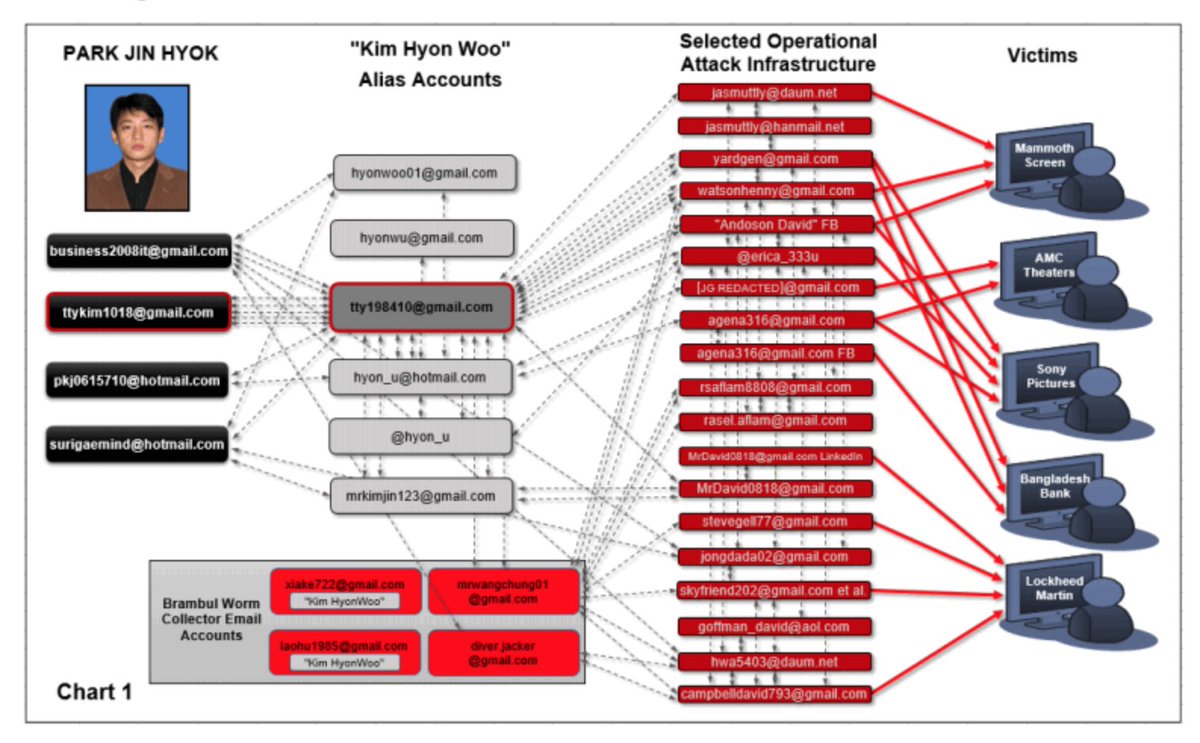
Teaching @sansforensics Threat Intelligence at #SANSFire this week. At first break, I had a chance to talk to students. The number of orgs with threat intelligence "programs" where program requirements are a complete unknown is always astounding to me. 1/n
If you don't know your #CTI requirements, you can't possibly build a good program. You may think you know the "requirements" but at the end of the day, those are determined by stakeholders (e.g. the "customer" aka whoever is in charge of funding the program). 2/n
If you aren't focusing on their concerns, you don't have an intelligence program. At best, you have some analysts wagging the dog with some analysis of potentially irrelevant (to the organization) intelligence information. It's not a professional operation, it's amateur hour. 3/n
If you don't KNOW your requirements, go ask your management what they should be. In my experience, the answer usually starts with a "well, you know..." To which I usually reply "no, please tell me." This can take a while, most people don't really know what they want. 4/n
Once you get good requirements, tailor your collection to those requirements. If you have data feeds that don't help with those requirements, get rid of them. They're a distraction. More data is not better. Enrich data and identify intelligence and collection gaps. 5/n
Then ask for feedback for your intelligence reports. This is just as important as getting requirements in the first place. You may write a report that looks freaking awesome to you, but is worthless to the stakeholder. Acting on feedback eliminates this disconnect. 6/6
• • •
Missing some Tweet in this thread? You can try to
force a refresh