
Breaker of software | GSE #150 | CTI/DFIR | @ians_security faculty | Bookings: jake at malwarejake dot com | He/him
How to get URL link on X (Twitter) App



https://twitter.com/MalwareJake/status/1038447751636418560First, to use Nuremberg as a reference point, we are equivocating hacking Sony with the Holocaust. I'm not ready to go there. Some people are saying "but if he hacked the power grid, that would be equivalent." Irrelevant, since that's not what happened here. 2/n
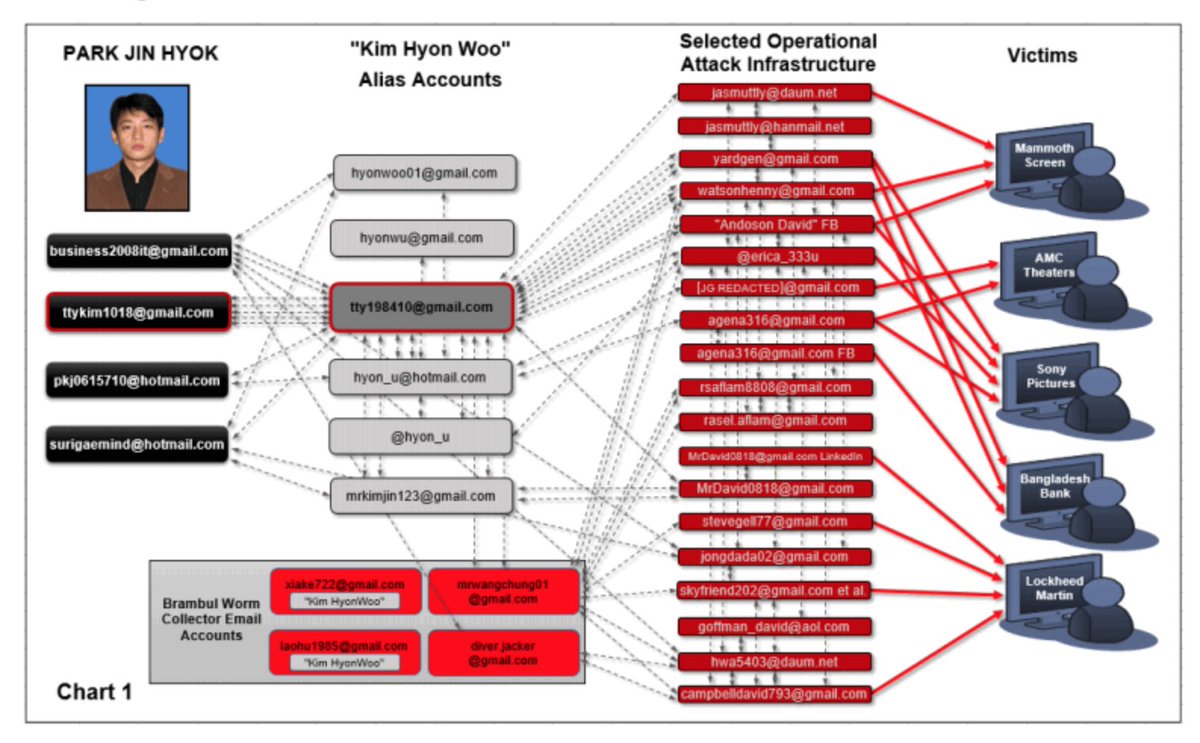
 People living in North Korea don't get a choice when the government comes calling. There are countless stories of atrocities where whole families are imprisoned (or worse) for defying the orders of the government. We know what would have happened if Park refused to hack Sony. 2/n
People living in North Korea don't get a choice when the government comes calling. There are countless stories of atrocities where whole families are imprisoned (or worse) for defying the orders of the government. We know what would have happened if Park refused to hack Sony. 2/n
https://twitter.com/nprpolitics/status/1034479471750008833And before I go further, I'll state that I'm a gun owner and support intelligent gun rights. But when the CDC isn't legally allowed to track gun violence deaths in the same way they track literally all other death, that's dumb and we have a problem. 2/n