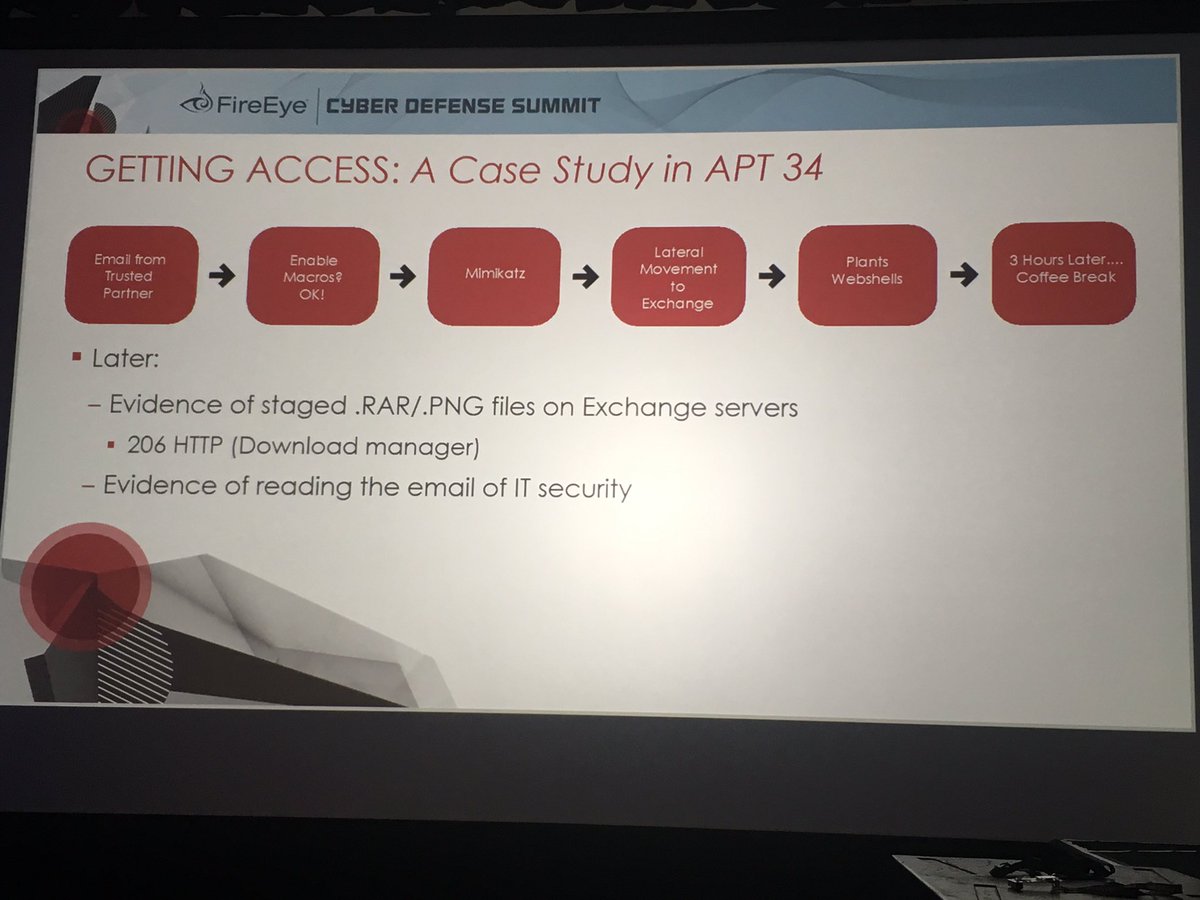
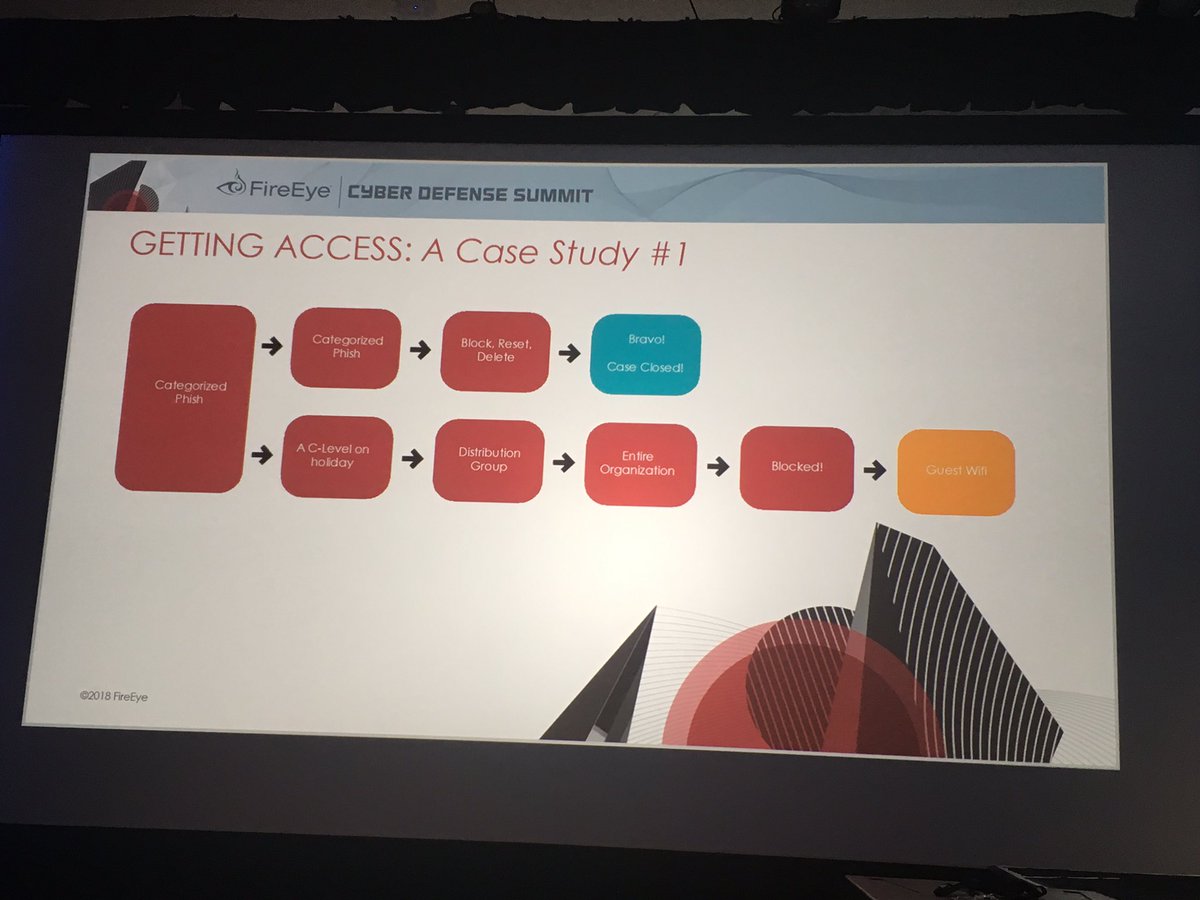
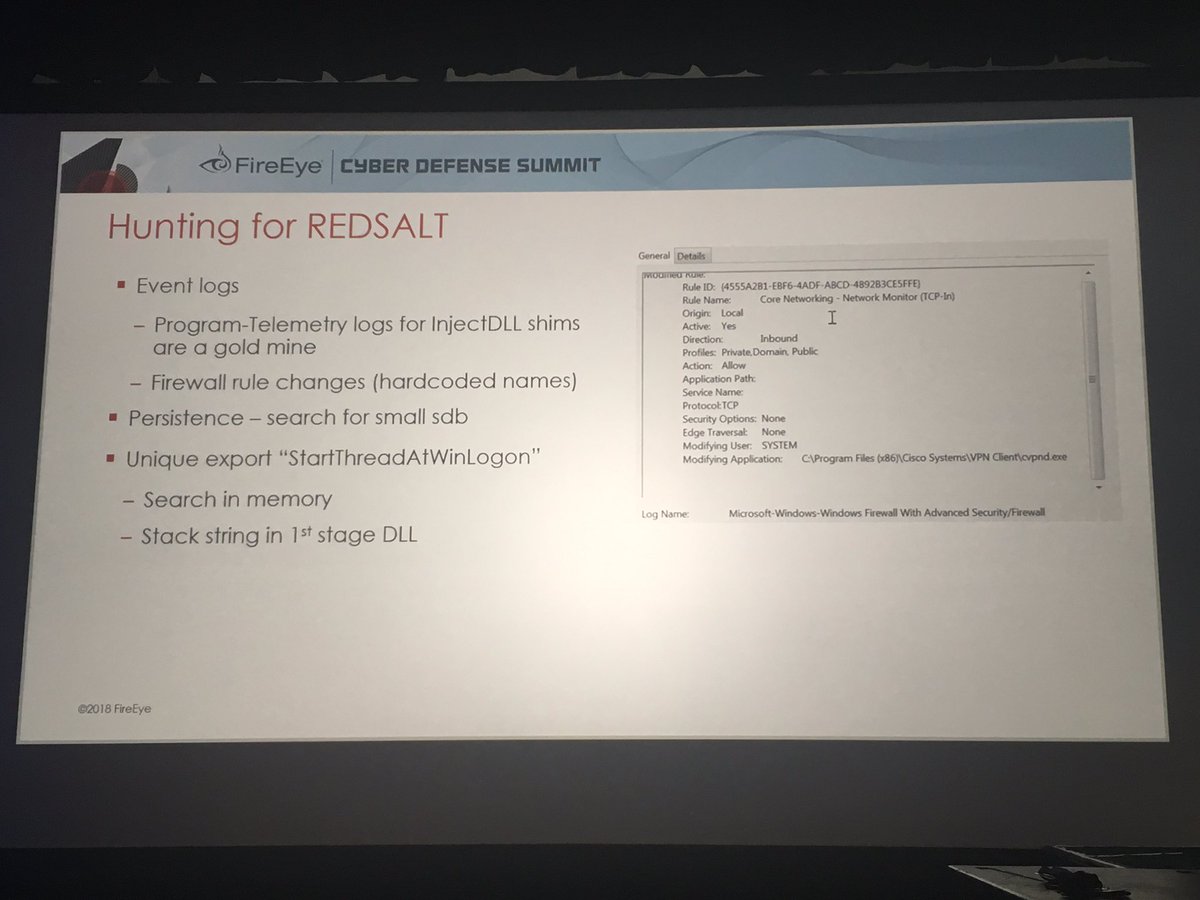
Remediation strategy in #DFIR is always a fun topic - with many opinions & not always a clear rule book to follow. It's like the English language for every rule there are 5 exceptions. My views have evolved over time - from combo of experience & as monitoring tools have improved
If you catch attacker early in attack lifecycle - this one is pretty easy. Take action immediately before they get a strong foothold. Very few exceptions to this rule. Tipoffs you are early in attack lifecycle. Malware owned by primary user of system or malware in startup folder
Opposite end of spectrum - if attacker has been there for months/years - it will take at the very (and I mean very) least a few days to get bare minimum handle on infected systems & how accessing the environment. Bigger challenge is client ability to take "big" remediation steps
Most victims who have to remediate quickly, will do least resilient measures (e.g block IPs/domains, change affected passwords of few accounts, & rebuild a few systems). Biggest risk here is that you've missed a backdoor & inadequate remediation steps allow attacker to "run wild"
Once you've tipped your hand to attacker - you've committed your org to permanent whack-a-mole (for as long as it takes) until you've dealt w/ problem. For great example - check out @ItsReallyNick & @matthewdunwoody's No Easy Breach talk @DerbyCon #APT29
One time on day 1 of a compromise assessment - I found attacker had compressed a few hundred gigs of sensitive data the day before...but had only stolen a few of the split RAR archives. We were in a real pickle. They'd been there for months - and we had no idea scope of intrusion
We got creative & wrote tool that could corrupt password protected RAR archives & also rate limited attacker's C2 where they exfilled data. We watched the attacker steal (very slowly) RAR archives over the next few weeks while we scoped the intrusion & prepared for remediation
We accomplished the goal of protecting the client (and their data) while giving our teams the time and space to remediate. Side note: would love to see face of the Chinese APT operator(s) when they realized they spent a month downloading hundreds of Gigs of corrupted RAR archives
• • •
Missing some Tweet in this thread? You can try to
force a refresh