Discover and read the best of Twitter Threads about #DFIR
Most recents (6)
I imagine the #sonytruthers playing armchair #DFIR investigators will emerge from wherever they’ve been hiding in order to dispute the #DPRK #indictment. My advice: you were wrong in 2014-2015, and you’d still be wrong today. HT @JohnHultquist int.nyt.com/data/documenth…
Because #attribution is inherently political per @RidT and @BuchananBen, you need more than “hacking” knowledge to assess national policy. Experience w/ #cybersecurity clearly helps, but gov internals, intel agency processes, bureaucracy, trade, diplomacy, LE, are all important.
I think it’s slowly changing, but a failure of #cybersecurity has been to think “soft” areas are much easier than coding, so any leet hacker is inherently qualified to address political science, history, economics, and related topics by virtue of their ability to code in ASM.
In light of the #FIN7 "Combi Security" DOJ indictment, we've released our massive technical post and indicator release: fireeye.com/blog/threat-re…
We reveal new information from @Mandiant IRs about the extent of FIN7's crimes, their innovative techniques, & how to find them today.
We reveal new information from @Mandiant IRs about the extent of FIN7's crimes, their innovative techniques, & how to find them today.
#FIN7 targeted other financial data when they encountered encryption in POS networks. New information today - and certainly helped stack up the charges against Combi Security.
Also @BarryV @stvemillertime first shared SEC filing targeting in March 2017: fireeye.com/blog/threat-re…
Also @BarryV @stvemillertime first shared SEC filing targeting in March 2017: fireeye.com/blog/threat-re…

Crime doesn't pay. Unless you worked for Combi Security, in which case it paid a pretty decent wage for Russian/Ukrainian "pen testers" 😄
Sidenote: @FireEye's red team is hiring but their operations *are* authorized and the only payment card hijinks is over who expenses dinner.
Sidenote: @FireEye's red team is hiring but their operations *are* authorized and the only payment card hijinks is over who expenses dinner.
Remediation strategy in #DFIR is always a fun topic - with many opinions & not always a clear rule book to follow. It's like the English language for every rule there are 5 exceptions. My views have evolved over time - from combo of experience & as monitoring tools have improved
If you catch attacker early in attack lifecycle - this one is pretty easy. Take action immediately before they get a strong foothold. Very few exceptions to this rule. Tipoffs you are early in attack lifecycle. Malware owned by primary user of system or malware in startup folder
Opposite end of spectrum - if attacker has been there for months/years - it will take at the very (and I mean very) least a few days to get bare minimum handle on infected systems & how accessing the environment. Bigger challenge is client ability to take "big" remediation steps
I've been thinking about the recent conspiracy theory of "where is the physical DNC server".
Here is a thread on the "missing" DNC server and my experience/advice from conducting similar investigations.
Here is a thread on the "missing" DNC server and my experience/advice from conducting similar investigations.
First, some background for my comments. Over the last decade, I've personally led investigations at over 100 organizations & taught dozens of classes for both federal law enforcement and the private sector on incident response and digital forensics.
I've never once physically acquired a server or asked someone to physically acquire a server. Literally the first thing you learn in digital forensics is how to take a forensic image (or in laymen's terms a complete copy of a computer).
Reading justice.gov/opa/pr/russian… today reminded me how I got my start in #DFIR in 2008 investigating FIN1. Let's take a walk down memory lane.
FIN1 (in my experience) has had a few major periods of activity (2007-2009, 2011-2012, and 2014-2015) - each with their own distinct set of TTPs. They've significantly improved their capabilities over the years (even though multiple members have been arrested)
FIN1 in the first period had the following TTPs: 1) didn't use backdoors 2) broke in commonly via SQL Injection 3) uploaded new tools by creating temporary tables and exporting the file via BCP 4) deployed a sniffer named sn.exe to identify systems with track data in memory
Use Sysmon to detect attempts to mess with your event log service and stay on top of red team tactics - #dfir, #EventLog 
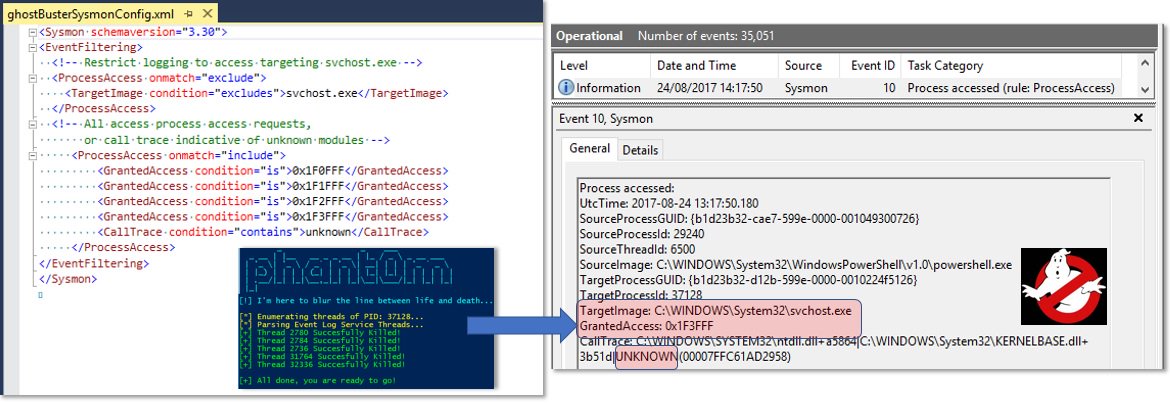
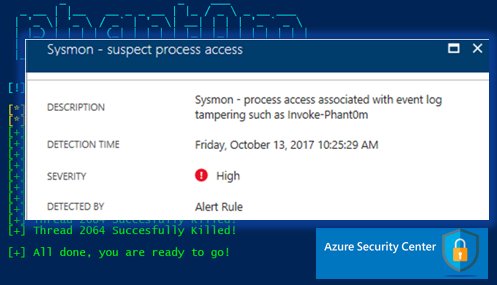
... and #dfir can surface sysmon-based detections for such in-memory attacks in #AzureSecurityCenter - read how at azure.microsoft.com/en-us/blog/det… 
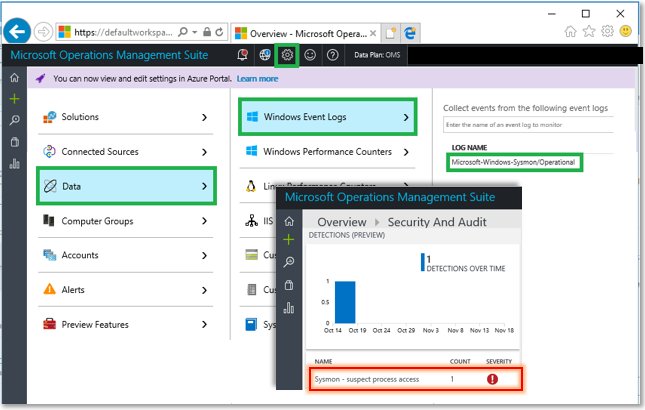
Was asked whether such alerts can be surfaced in the OMS Security & Audit dashboard. 🔥Sure! 🔥Configure Sysmon collection via OMS settings as shown, and see the detection show up in OMS 🎉 !