
Microsoft Threat Intelligence Center - Former Incident Responder @Mandiant & Chief Security Architect @FireEye
How to get URL link on X (Twitter) App

 APT34 compromised a trusted partner org - and used that to abuse trust (convinced user to enable macros) and successfully phish victim
APT34 compromised a trusted partner org - and used that to abuse trust (convinced user to enable macros) and successfully phish victim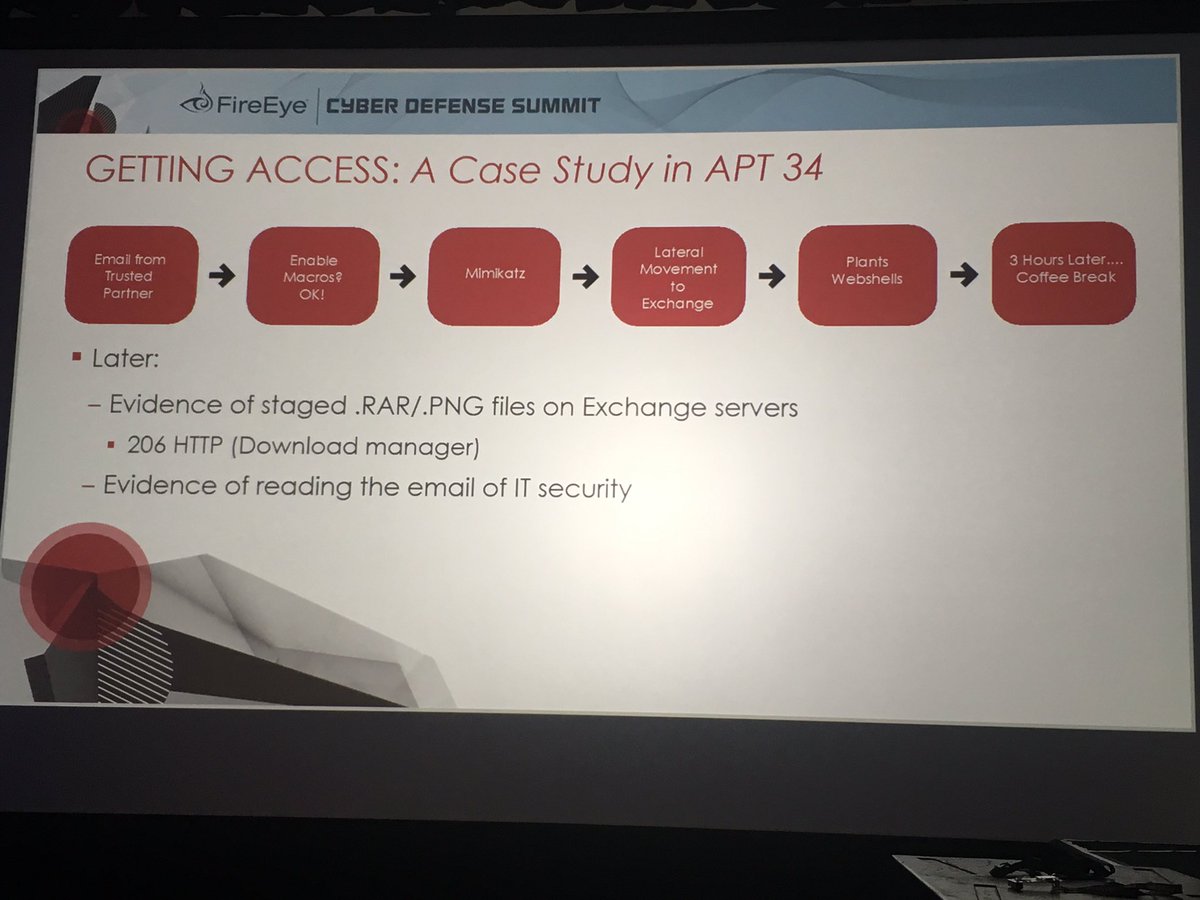

 It's not often that you see ACI Shims used for persistence
It's not often that you see ACI Shims used for persistence 
https://twitter.com/realDonaldTrump/status/1018072081676865536