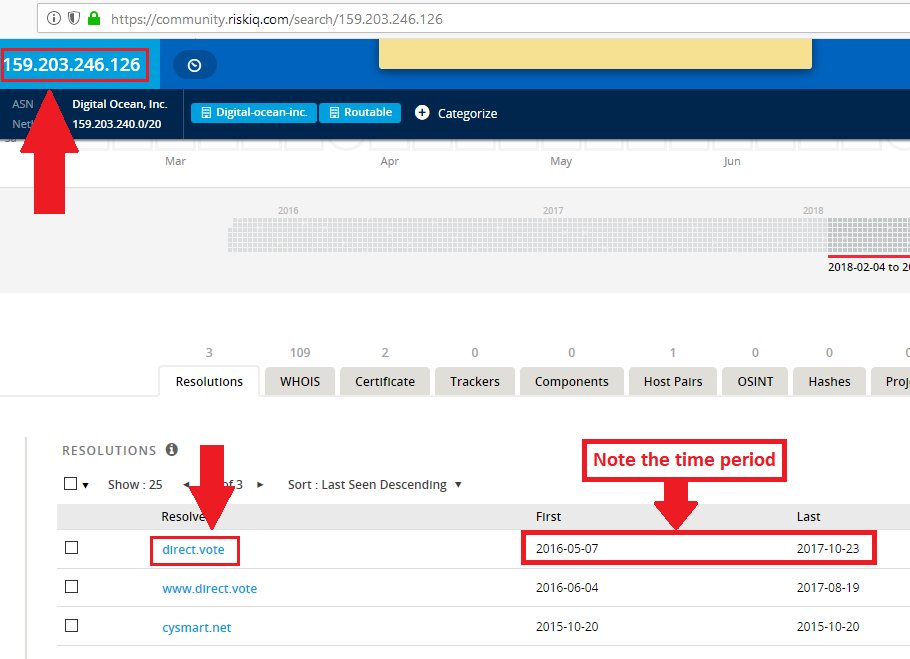
Step 1: Locate odd binary being served to the public internet.
Step 2: Get curious.
Step 3: Fire up a contained, temporary, virtual environment.
Step 4: Run the binary.
[result attached]
Step 5: Forever wonder of what could have been.
Step 2: Get curious.
Step 3: Fire up a contained, temporary, virtual environment.
Step 4: Run the binary.
[result attached]
Step 5: Forever wonder of what could have been.

And of course they are also serving up a script that gives *ultimate* trust to expired keys. THIS IS NOT OK FOR A DOD CONTRACTOR TO HAVE BEEN DOING (among other things). 

But, hey, while you're at it you might as well pipe some stuff straight into bash from the internet, right? #yolo I guess. 

[yes, that's an actual SCL-hosted script pulling in the contents of another SCL-hosted file. I didn't make it up.]
• • •
Missing some Tweet in this thread? You can try to
force a refresh