
How to get URL link on X (Twitter) App





 And of course they are also serving up a script that gives *ultimate* trust to expired keys. THIS IS NOT OK FOR A DOD CONTRACTOR TO HAVE BEEN DOING (among other things).
And of course they are also serving up a script that gives *ultimate* trust to expired keys. THIS IS NOT OK FOR A DOD CONTRACTOR TO HAVE BEEN DOING (among other things). 
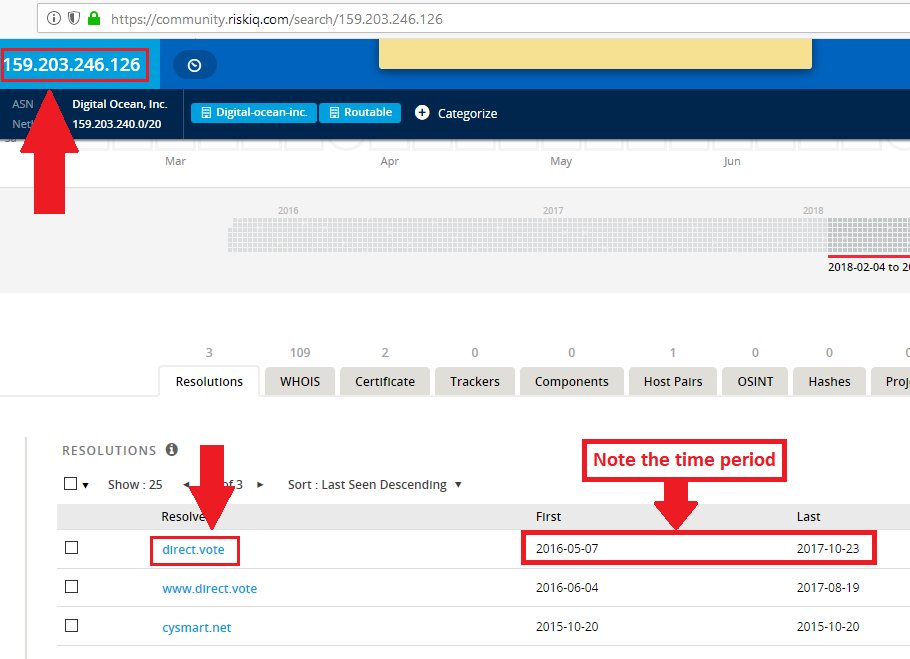


 I'm not saying that there was any funny business conducted regarding influencing any potential voters into thinking that they could actually vote via phone or internet... but that would certainly fit this macabre circus that we're all watching play out.
I'm not saying that there was any funny business conducted regarding influencing any potential voters into thinking that they could actually vote via phone or internet... but that would certainly fit this macabre circus that we're all watching play out.
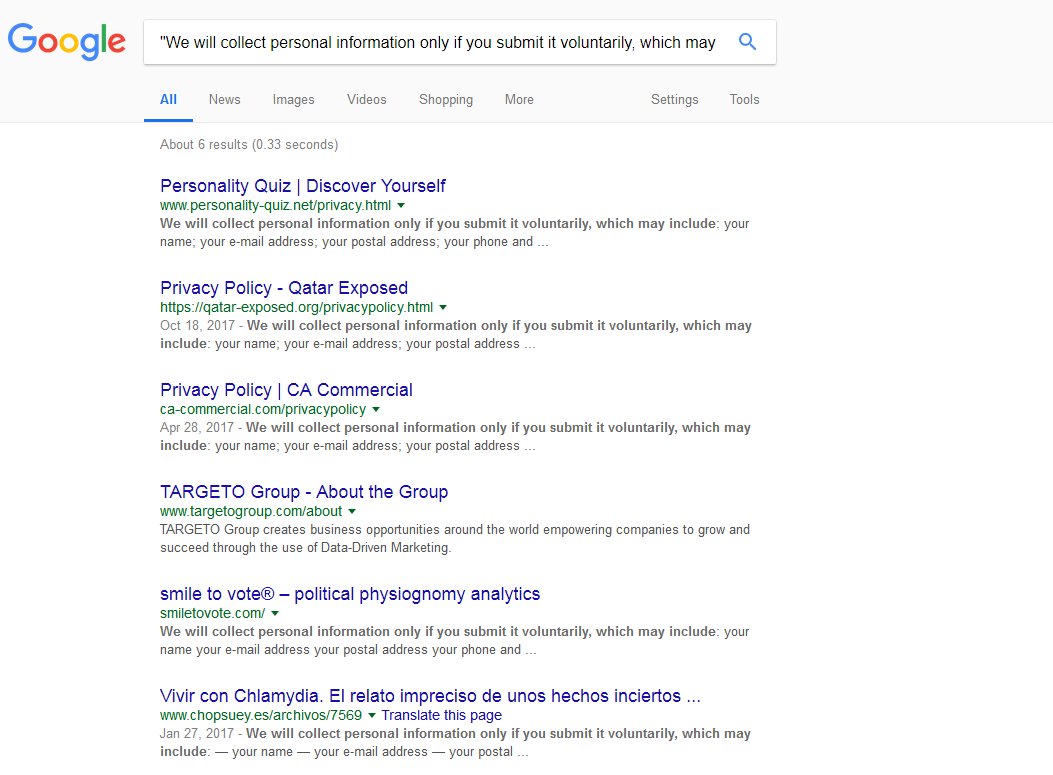
 For what it's worth, this little trick is extremely useful for finding hidden relationships between entities playing shell games.
For what it's worth, this little trick is extremely useful for finding hidden relationships between entities playing shell games.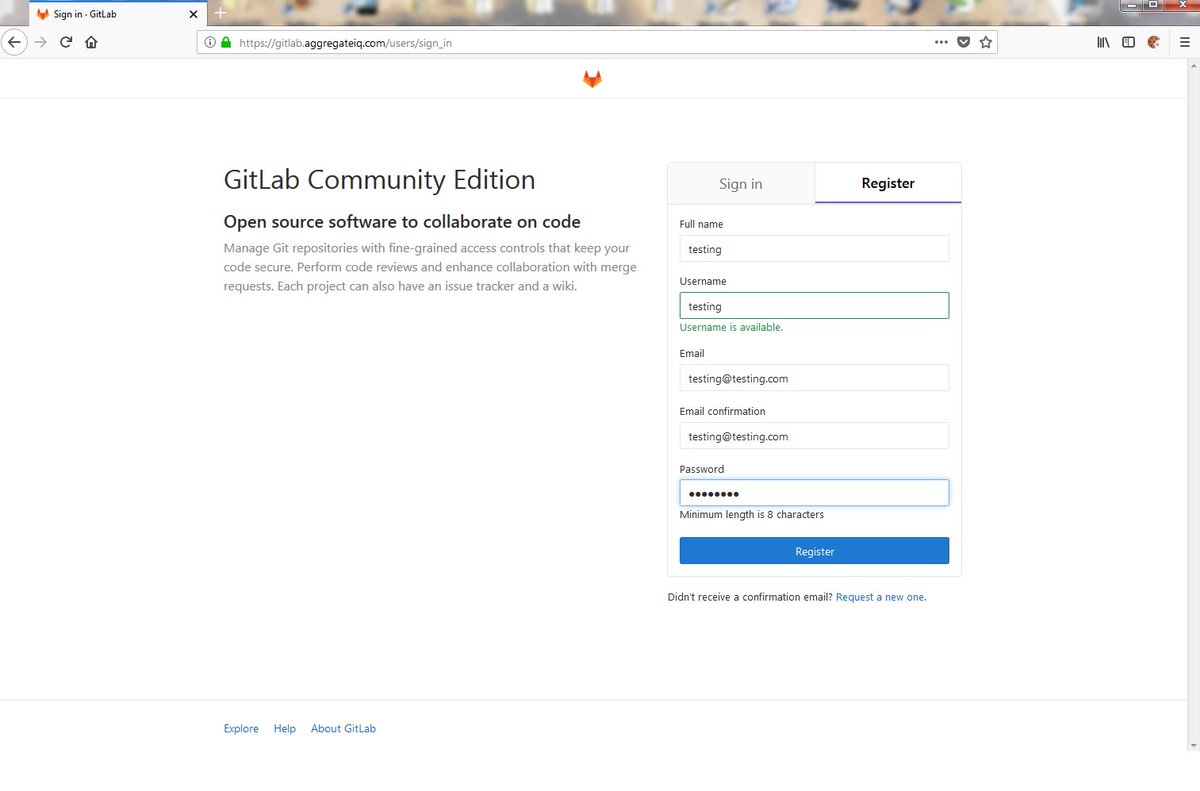
 Data involves Cambridge Analytica, AggregateIQ, WPA Intel, Brexit, Cruz, and more.
Data involves Cambridge Analytica, AggregateIQ, WPA Intel, Brexit, Cruz, and more.