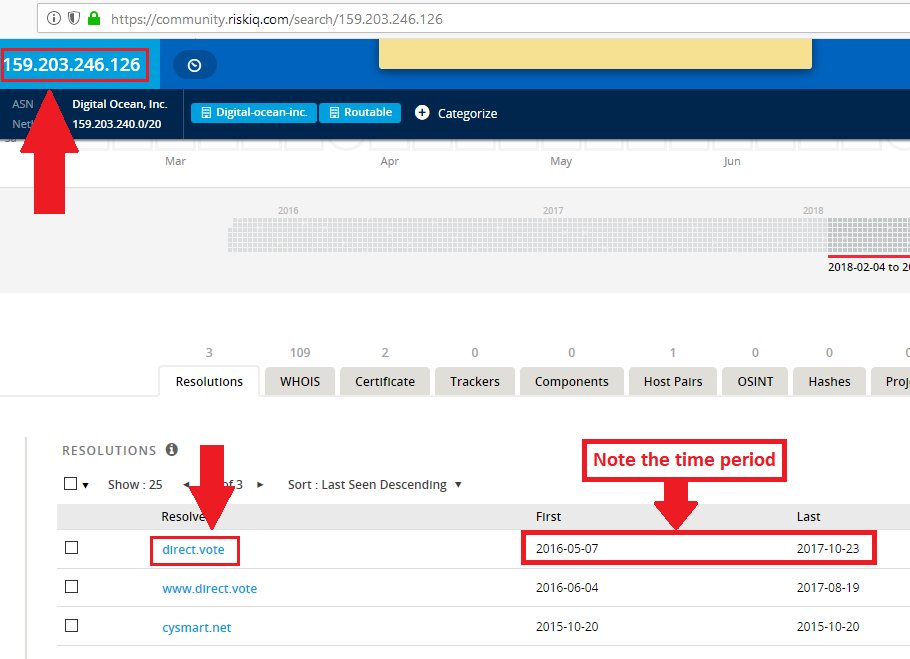
If you want a thread to pull on, consider why the same entity would be behind these listed sites: americanstrawpoll.com/img/
[ web.archive.org/web/2018100119… ]
Why would someone be interested in the data generated by the public interacting with those sites?
#CA #AIQ #SCL #PG #LD #AS #WPA
[ web.archive.org/web/2018100119… ]
Why would someone be interested in the data generated by the public interacting with those sites?
#CA #AIQ #SCL #PG #LD #AS #WPA
And, yeah, the "neverhillary" section is in reference to a previously active site "neverhillary2016.com" (a domain which I have since taken over ownership of after they let it lapse).
Here's a hint, "LoudDoor" is a bigger player than people realize.
• • •
Missing some Tweet in this thread? You can try to
force a refresh