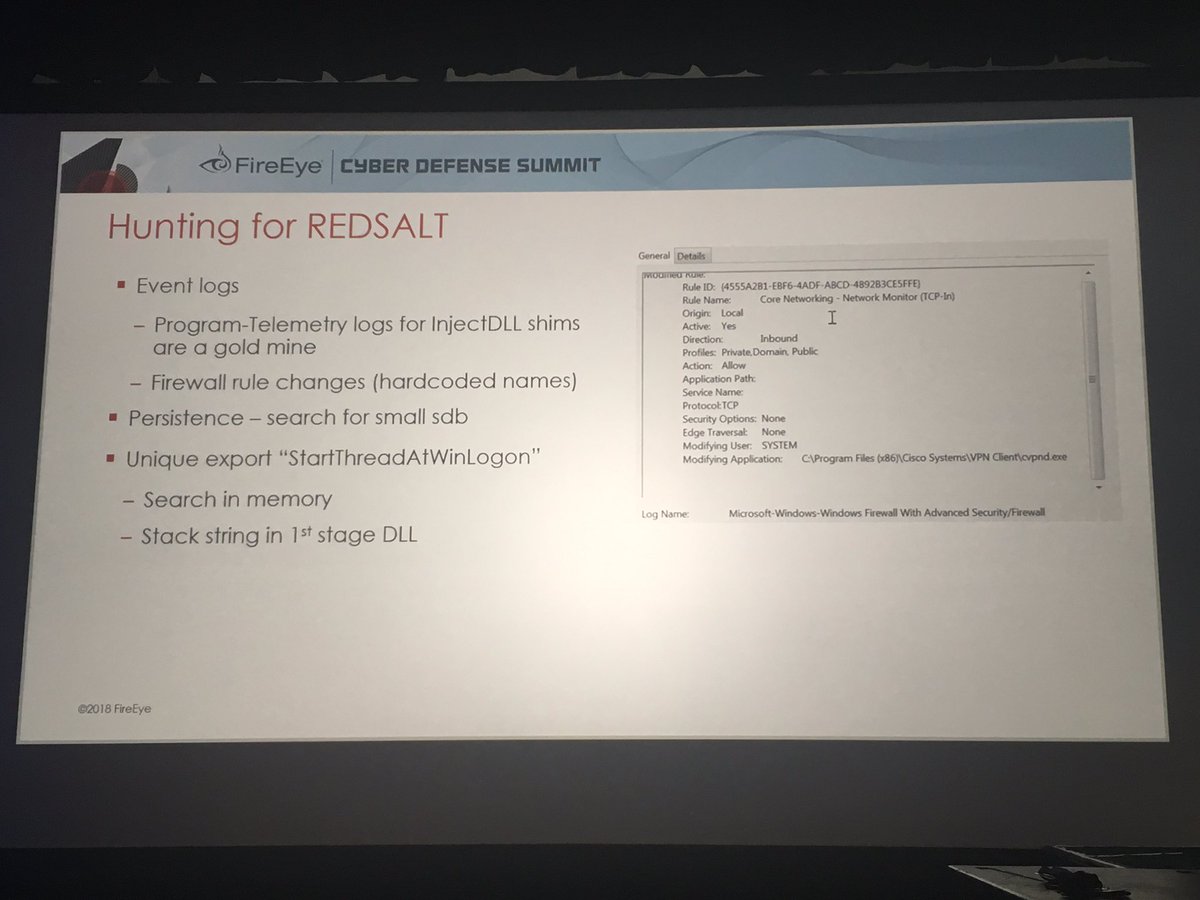
"You've Got Mail"
@danielcabaniel @CyberAmyntas discussing email phishing and mail server attack trends
#FireEyeSummit
@danielcabaniel @CyberAmyntas discussing email phishing and mail server attack trends
#FireEyeSummit
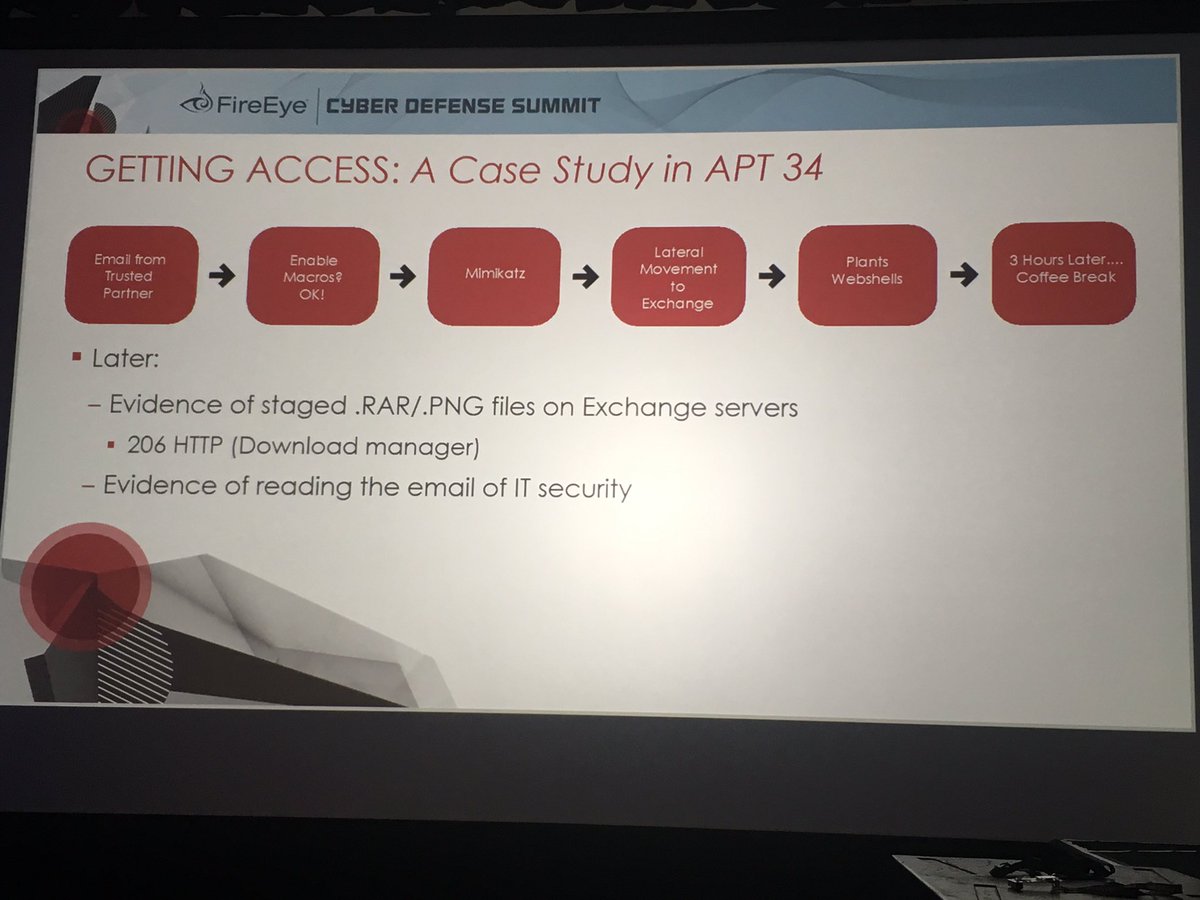
APT34 compromised a trusted partner org - and used that to abuse trust (convinced user to enable macros) and successfully phish victim
Subsequently staged data theft files on the Exchange server as .png files and downloaded from the server.
#FireEyeSummit
Subsequently staged data theft files on the Exchange server as .png files and downloaded from the server.
#FireEyeSummit
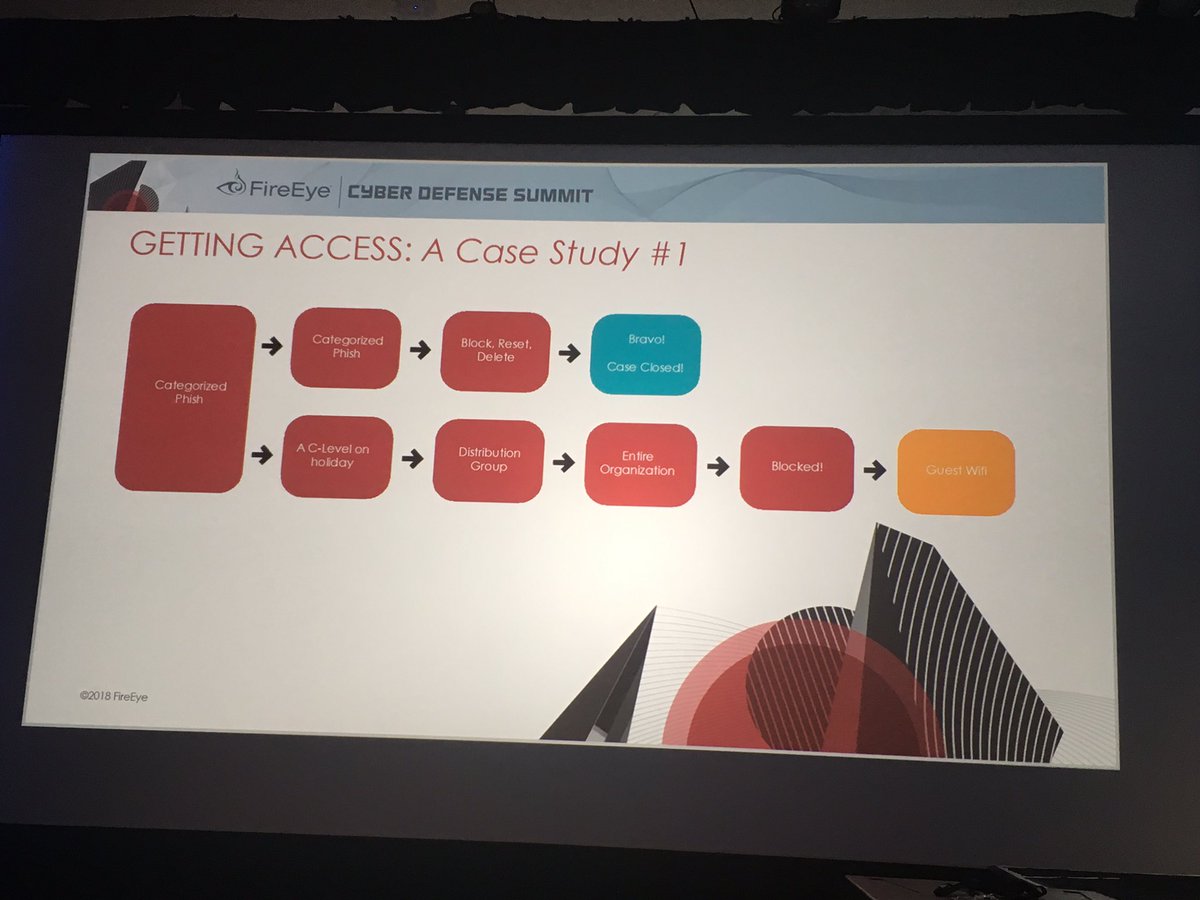
C-level credential phished while on vacation - APT34 used account access to phish entire company. Even though infosec team blocked URL on web proxy - employees switched to guest wi-fi to access the URL.
#FireEyeSummit
#FireEyeSummit
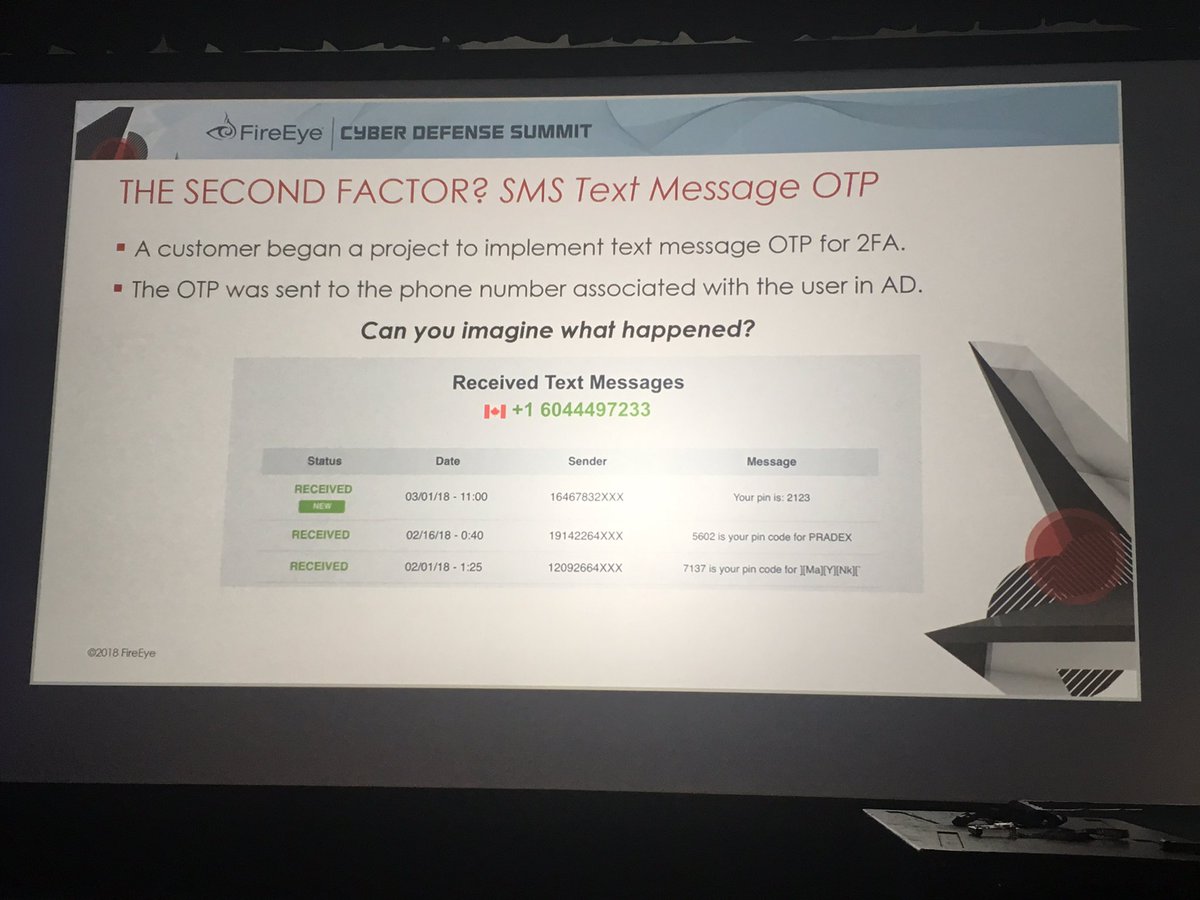
2FA is critical to protect internet facing logins...but it's not effective if attacker can register their own phone number to receive 2FA.
Screenshot is of a Canadian phone number accessing 2FA. Organization didn't have any presence in Canada.
#FireEyeSummit
Screenshot is of a Canadian phone number accessing 2FA. Organization didn't have any presence in Canada.
#FireEyeSummit
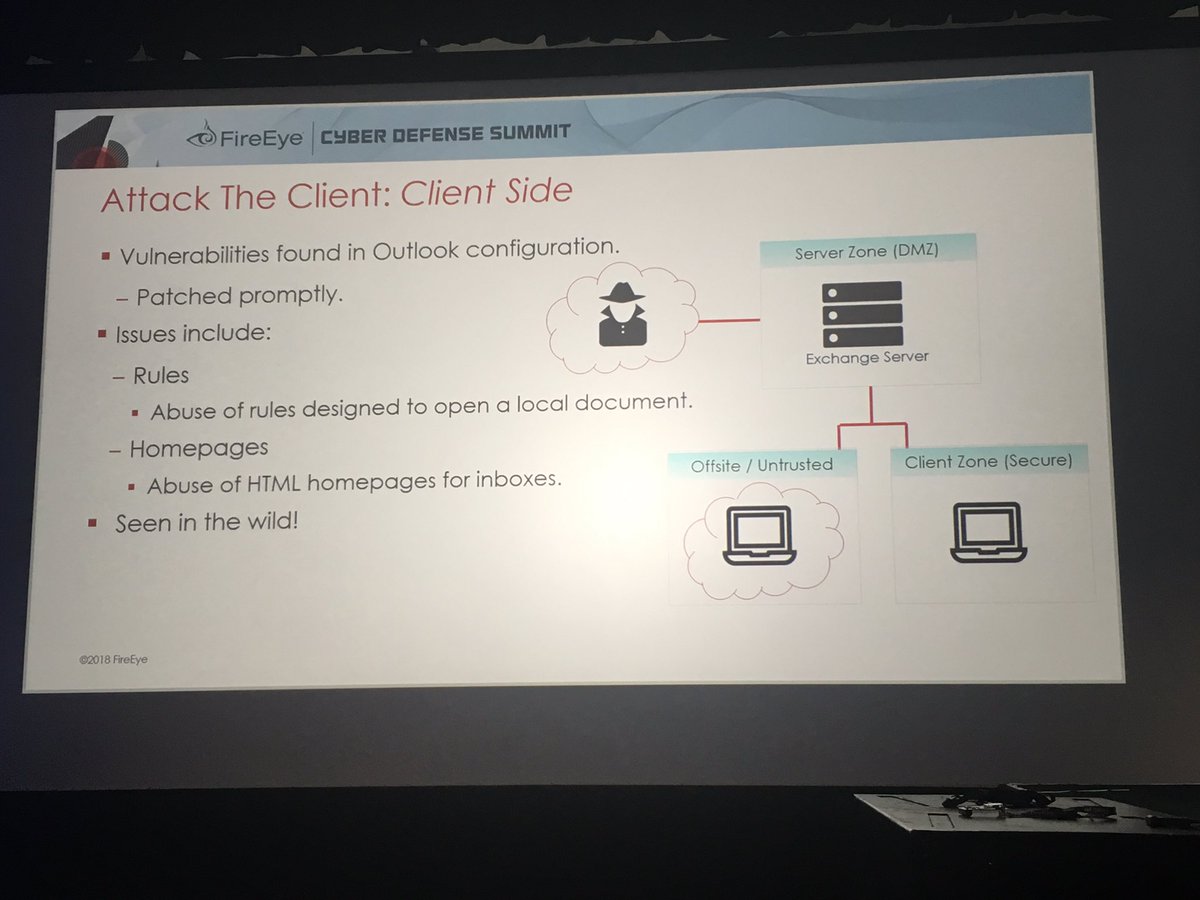
Outlook Ruler/homepage persistence FTW!
"This has been patched but we still see it leveraged b/c most orgs haven't applied patch"
Just by obtaining user email creds you can get code execution on victim machine using something like a COM scriptlet #DailyScriptlet
#FireEyeSummit
"This has been patched but we still see it leveraged b/c most orgs haven't applied patch"
Just by obtaining user email creds you can get code execution on victim machine using something like a COM scriptlet #DailyScriptlet
#FireEyeSummit
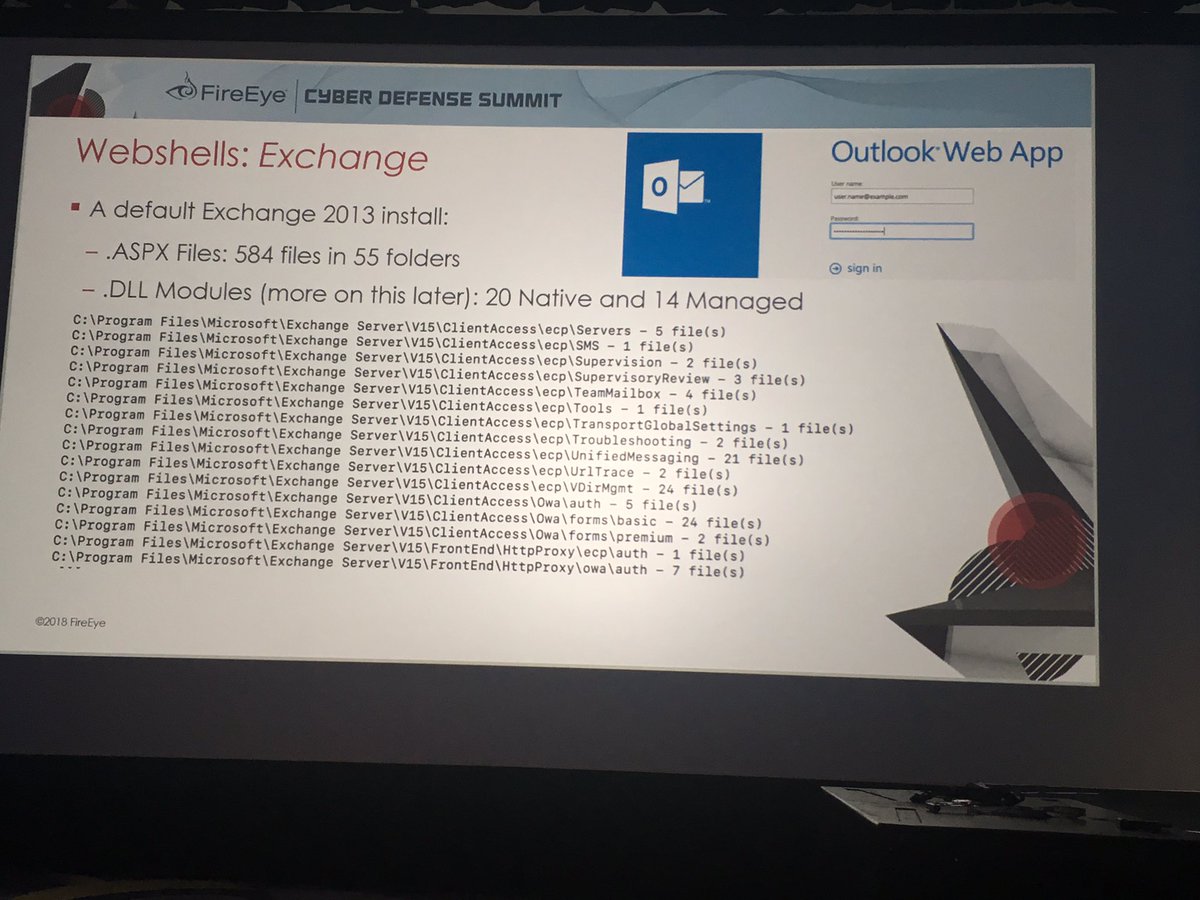
Exchange servers have lots of default web related files - so easy for attacker to blend in a web shell
#FireEyeSummit
#FireEyeSummit
"To encourage the user to open the email - attacker calls a user directly. We've also seen it used to get a users second factor token code" @danielcabaniel
#FireEyeSummit
#FireEyeSummit
This talk had too many knowledge bombs for me to keep up with the live tweeting. You should check out the video when we post it later.
#FireEyeSummit
#FireEyeSummit
• • •
Missing some Tweet in this thread? You can try to
force a refresh