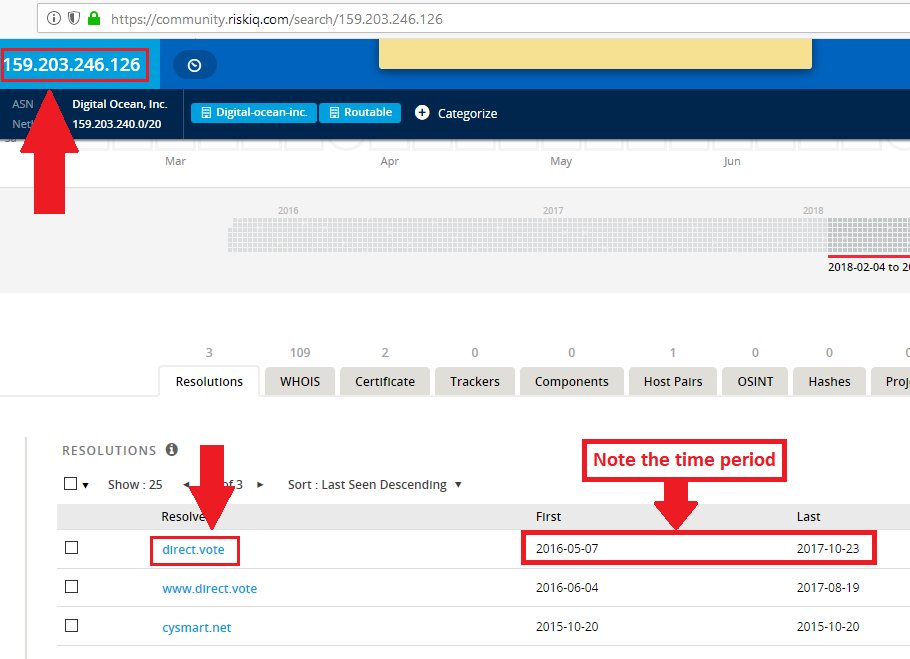
When I found the exposed 154 million US voter database in June 2016, I was able to trace the data to a company named L2 Political.
L2 then traced the leak to a client of theirs. The client claimed hackers had taken down their firewall which then publicly exposed the database.
L2 then traced the leak to a client of theirs. The client claimed hackers had taken down their firewall which then publicly exposed the database.
L2's client did not suggest that *I* was the hacker(s) who had removed their firewall and exposed the database.
If true, this means there is confirmation, from the holder of the data, that a nationwide US voter registry _was_indeed_hacked_ months prior to the 2016 election.
If true, this means there is confirmation, from the holder of the data, that a nationwide US voter registry _was_indeed_hacked_ months prior to the 2016 election.
I can't believe I didn't recall this sooner. Foreign hacking of the US election system was not much of a topic when I originally reported this 154 million voter record leak and the detail of actual confirmation of a US nationwide vote hack became lost in the ether.
To all official investigations into foreign interference in the 2016 election: You need to get L2 Political to name the client that was hacked. At the time of the discovery L2 did not tell me the name of the client and that part is still unknown.
p.s. Cambridge Analytica previously admitted to being a L2 Political client during that time period. L2 *did* tell me that L2 does not have very many nationwide voter registry clients.
Someone(s), please get that client's name from L2 Political.
Someone(s), please get that client's name from L2 Political.
I have emails from L2's CEO proving this.
The reason I'm jumping to the "foreign hacking" possibility instead of assuming it could have been domestic actors is that when the database was discovered (apparently a consequence of the claimed hack) I was able to query one access log. It showed access from a Serbian proxy IP.
Here's an article from the time regarding the discovery: csoonline.com/article/308813…
Please note that this June 2016 find was prior to my employment with @UpGuard. [although my super awesome skillset did transfer over ;)]
Please note that this June 2016 find was prior to my employment with @UpGuard. [although my super awesome skillset did transfer over ;)]
• • •
Missing some Tweet in this thread? You can try to
force a refresh