Thread time! Why can't they just quickly patch #meltdown or #spectre and push out another cpu? Why could it possibly take years? Why don't they use AGILE or x/y/z? Lots of reasons:
(note: my goal is not to criticize chip manufacturers - it's to defend the constraints they have)
(note: my goal is not to criticize chip manufacturers - it's to defend the constraints they have)
Let's start with a standard software product many are familiar with and work off that. First, every time you hit 'build' it's called a 'stepping', costs millions of dollars & takes several months. If you want a profitable product, you may only get 10 chances to press 'build'.
On top of that, half those 'builds' are not 'full layer steppings' meaning you can't change any logic gates, just how they're connected. Even with a full layer stepping you can't shuffle stuff around anywhere like you can with library files and whatnot.
One way to think of it - imagine an ISA that only supports 8 bit jumps/calls. You can only go back or forth +- 128 bytes from your current address. you can't just plug in an extra 256 bytes of code between two existing blocks without lots of rework and significant timing impact
So what's an easy fix on silicon? 1 bit to a couple bytes. Equivalent of inverting a test, changing an immediate value in code, nopping out a bad instruction, or adjusting a branch destination. maybe reordering a simple if/else.
Any more than that, and you impact everything around you. Your extra power draw might heat up another gate that makes a latch work slower and causes every cpu to be speed rated 100mhz slower. The extra space you need might introduce propagation delays that can't be worked around.
So, the easiest possible fix means a couple months to 'build', a few months for you to test your fix, plus regression testing against 50 years of code that your CPU must support. Followed by ramping up high volume manufacturing. Let's say 6 months from fix to on the shelf.
But really, even a small fix means building, testing, fine tuning, building, testing, characterizing, and then releasing. So count on 2-3 steppings and we quickly get to 6 months to a year.
What about a minor new feature? If you'vea already got the architectural and specification stuff done, you need to implement it in HDL, simulate and verify it, and then put it through the build/test/production path. 2 years.
The reality is that new features are risky when you only get a few revisions. LOTS of features exist in silicon for generations before they're fully vetted and 'enabled'. So most features end up being more like 5 years to availability on a product with software supporting it.
But we're still not there. #meltdown and #spectre attack fundamental architecture features that have been built on for decades. We may need to go back to the drawing board. (old intel product lifecycle slide). Everything so far has been in the yellow 'development' phase. 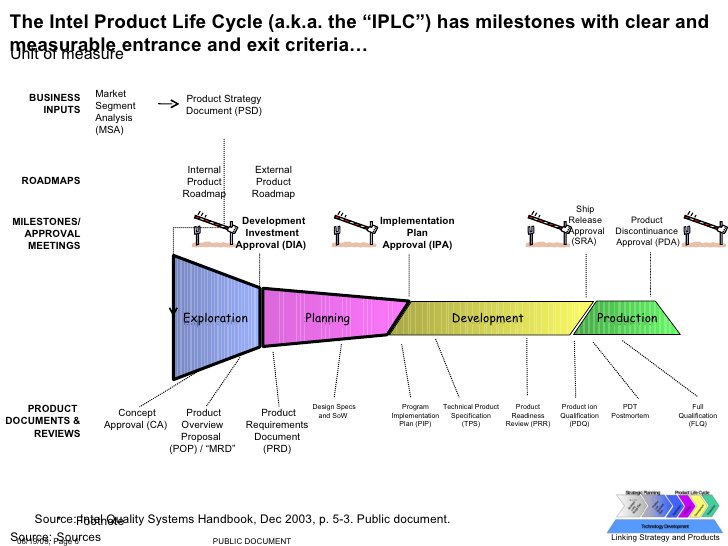

Assuming we don't need too much new research, we amend the architecture, write new specifications, implement the architecture in HDL, fabricate the chip, and go through validation before selling it. Once again, we're talking 4 to 5 years.
Whats it all mean? My guess is there might be a few hardware 'quick fixes' that we could see as soon as this summer (one year after first rumblings). These would probably have a performance impact, but would be a smaller impact than the current software fixes.
Come 2019 and 2020, other products in the pipeline will have more involved fixes that again improve performance over the software and quick fixes.
The solution everyone wants is a full fix with no performance impact. I can't imagine that coming any sooner than 2021.
The solution everyone wants is a full fix with no performance impact. I can't imagine that coming any sooner than 2021.
I left Intel over 5 years ago - I know nothing that isn't public about current or upcoming products. This is all speculation based on general knowledge of CPU and silicon manufacturing. Thanks to @savagejen for asking me questions and encouraging me to post.
• • •
Missing some Tweet in this thread? You can try to
force a refresh