Discover and read the best of Twitter Threads about #spectre
Most recents (11)
From what I understand, the latest #OpenBSD vs #Intel thing went a little bit like that:
- OpenBSD: Can we be a part of this rumored Intel bug embargo?
- Intel: No. Go away.
- OpenBSD: Can we be a part of this rumored Intel bug embargo?
- Intel: No. Go away.
- OpenBSD: dev do their homework, fix FPU bug, publish patch.
- Theo (at @BSDCan): we are worried, we don't have access to info. Please help us.
- Intel: publishes official advisory: intel.com/content/www/us…
- Theo (at @BSDCan): we are worried, we don't have access to info. Please help us.
- Intel: publishes official advisory: intel.com/content/www/us…
Now everybody and their dogs are going crazy over #OpenBSD developpers doing their jobs , correcting stuff and "violating"an embargo... That they were *never* a part of. Because Intel did not want them to receive information!
Quotable Quotes on #SoftwareTesting from this talk by @dakami at the inaugural DEF CON China. 1/?
"The goal of this talk is to connect a series of thoughts that you may never have thought were linked...Anything can be linked." 1:15
@katiezavadski “F---ing Sith Lord,” “Horrific Leakers,” & “Berserkazoid Craziness”: The Mooch Recalls His Brief Shining Fortnight at the Center of US Politics, by @WilliamCohan vanityfair.com/news/2018/02/t… Wish he’d been asked about🇷🇺sanctions, RDIF & if he now supports what he opposed at #WEF17?
This is something, coming from a guy who missed the birth of his child—& had his lawyer demand a paternity test?
Does suing CNN & forcing a journo to resign for accurate reporting have permanent benefits?
Does suing CNN & forcing a journo to resign for accurate reporting have permanent benefits?
World chess body has Swiss bank accounts frozen after (Putin-linked) president is accused of links to ISIS oil deals telegraph.co.uk/news/2018/02/1… After @Kasparov63 failed to have him removed, maybe Team Spectre decided enough was enough—& this was the only way to take back the org?
As per ⬆️, an excellent post by @katiezavadski, examining RDIF & Dmietiev! And a great thread follows. Hope to see Scaramucci, Thiel & Goldman Sachs looped in, just in time for Davos!
@katiezavadski So T-rump, Scaramucci & Mnuchin are going to #WEF2018. What about Schwarzman, Bonderman, Black & or WEF Young Global Leaders Dmietriev & Thiel? Or Milner? Is there an RDIF reunion scheduled?
Also, out of curiousity, any chess tourneys or events scheduled?
Also, out of curiousity, any chess tourneys or events scheduled?

@katiezavadski Wonder if Scaramucci can get another reporter canned for accurately reporting on what he said in public at #WEF, like he did last year? Or were his legal threats to CNN enough to prevent anyone from taking the risk? Are the Mooch & Thiel now press-proof?
The assumption "bug collisions are so common in all software that everyone should assume that for any bug disclosed, it's probably been found by attackers & exploited already" contrasts how scientific research works. Security research is no exception.
Bug & research "collisions" can happen due to lots of low-hanging fruit. It can also occur when researchers pay attention to reach other's work. I've discussed researcher "swarming" for years, & recently on stage at BlackHat this summer.
Bug collision or correlation rates for software that has a lot of bugs (bug dense, say, because of not being well-tested) will generally model higher bug collision rates than in software with low bug density. See slides #23-27 from my RSA talk in 2015.
rsaconference.com/writable/prese…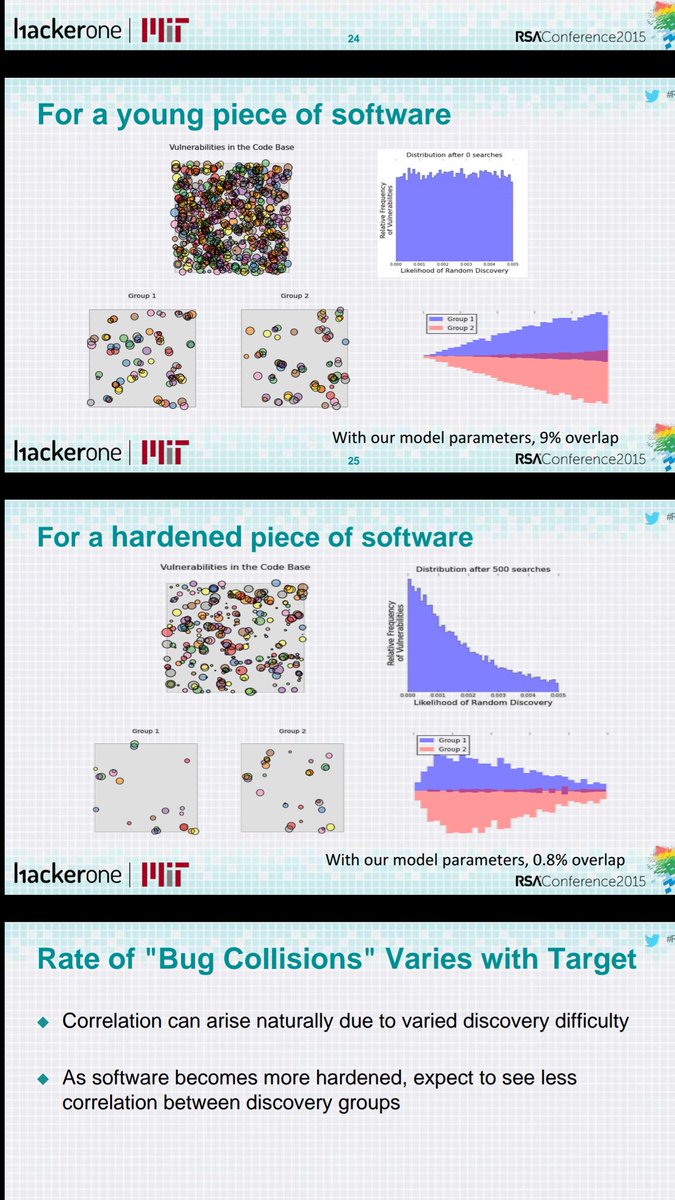
rsaconference.com/writable/prese…

Thread time! Why can't they just quickly patch #meltdown or #spectre and push out another cpu? Why could it possibly take years? Why don't they use AGILE or x/y/z? Lots of reasons:
(note: my goal is not to criticize chip manufacturers - it's to defend the constraints they have)
(note: my goal is not to criticize chip manufacturers - it's to defend the constraints they have)
Let's start with a standard software product many are familiar with and work off that. First, every time you hit 'build' it's called a 'stepping', costs millions of dollars & takes several months. If you want a profitable product, you may only get 10 chances to press 'build'.
On top of that, half those 'builds' are not 'full layer steppings' meaning you can't change any logic gates, just how they're connected. Even with a full layer stepping you can't shuffle stuff around anywhere like you can with library files and whatnot.
Here's my layman's not-totally-accurate-but-gets-the-point-across story about how #meltdown & #spectre type attacks work:
Let's say you go to a library that has a 'special collection' you're not allowed access to, but you want to to read one of the books. 1/10
Let's say you go to a library that has a 'special collection' you're not allowed access to, but you want to to read one of the books. 1/10
You go in and go to the librarian and say "I'd like special book #1, and the Sue Grafton novel that corresponds to the first letter of page 1 of that book." 2/10
The librarian dutifully goes and gets special book #1, looks at page 1, sees 'C', and also grabs 'C is for Corpse', and comes back to the desk, but does not show you the books. 3/10
Here are a few insights on the #Meltdown and #Spectre vulnerabilities based on my recent @RANDCorporation research. /1 rand.org/pubs/research_…
First, this is yet another reminder that vulnerabilities can last a long time (our data showed vulnerabilities lasted 6.9 years before being publicly disclosed) and have a low chance of being discovered (5.7% per year). /2
Explainer on #Spectre & #Meltdown:
When a processor reaches a conditional branch in code (e.g. an 'if' clause), it tries to predict which branch will be taken before it actually knows the result. It executes that branch ahead of time - a feature called "speculative execution".
When a processor reaches a conditional branch in code (e.g. an 'if' clause), it tries to predict which branch will be taken before it actually knows the result. It executes that branch ahead of time - a feature called "speculative execution".
The idea is that if it gets the prediction right (which modern processors are quite good at) it'll already have executed the next bit of code by the time the actually-selected branch is known. If it gets it wrong, execution unwinds back and the correct branch is executed instead.
What makes the processor so good at branch prediction is that it stores details about previous branch operations, in what's called the Branch History Buffer (BHB). If a particular branch instruction took path A before, it'll probably take path A again, rather than path B.
Some of you might be hearing about #Spectre and #Meltdown today, which allow memory from other processes and the kernel itself to be read. They exploit CPU designs.
I'm still doing my reading, but a good place to start if you're technically inclined is spectreattack.com
I'm still doing my reading, but a good place to start if you're technically inclined is spectreattack.com
Spectre involves training the CPU to speculatively run invalid code in the victim's address space, and then using a side-channel (such as cache timings) to infer details about the victim's memory.
It affects at least AMD, Intel and ARM CPUs
The sample exploit reads 10KB/s.
It affects at least AMD, Intel and ARM CPUs
The sample exploit reads 10KB/s.
Spectre also includes sample code for breaking out of the JavaScript sandbox on chrome.
It's very, very clever.
It's very, very clever.
Does anyone call Yuri Milner's squad "SpectLFGzyduz7A
Justification acrobatics won’t cut it; Silicon Valley knew where Milner’s(& his Russian criminal partner’s)💰came from; they just didn’t care
The source of Milner’s💰is not news nor was it a secret. 3 examples gigaom.com/2012/05/08/why… jeffreycarr.blogspot.com/2011/04/why-yu… thenewamerican.com/usnews/politic…
