
How to get URL link on X (Twitter) App

https://twitter.com/marcan42/status/1047925500318965760If someone said that the implant was found inside a coupler, first I'd check component suppliers for couplers that might fit the bill. And the one displayed is pretty much the smallest one you can find with 'coupler' in the name.
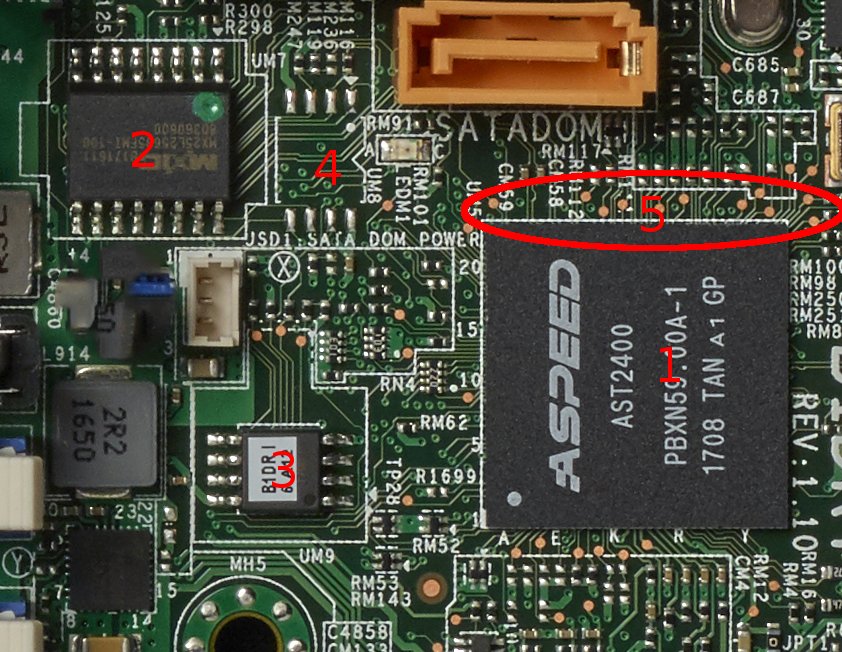
https://twitter.com/qrs/status/1047910169261330432Given a photo of a server motherboard, this was my response after a few minutes. You'll have to take my word i wrote this 4 Sept 2017.


 This is an older lightning port fan that @HackingThings had. No surprise there's a chip in there to speak SDQ to tell the iPhone to supply power
This is an older lightning port fan that @HackingThings had. No surprise there's a chip in there to speak SDQ to tell the iPhone to supply power 