One important thing about Aadhaar or any centralized system,particularly connected to money, which I have not said so far, is how it completely destroys any security by obscurity which we have enjoyed so far. Take the example of mobile OTP.
Aadhaar uses SMS One Time Password (OTP) to secure Aadhaar transactions. But we have seen how process to update mobile for Aadhaar itself is hopeless destroy-the-aadhaar.blogspot.in/2017/12/regist…
It is hopeless in terms of security as well as frustrations experienced by the user. Some of the security risks can be fixed if UIDAI is more transparent about the process, as we have seen in that article. Some frustrations also may reduced if Aadhaar centres more nearby. But...
But insecurity as well as frustrations caused by requiring flawed technology of biometrics for updating mobile number with Aadhaar cannot be removed. So that's a reason we must #DestroyTheAadhaar, as good lawyers are arguing in court too.
But another aspect is that it is entirely circular. On one hand we claim that OTP provides security authentication factor just in case biometrics are stolen. But on other hand mobile no update can be done just by stolen biometrics. This circularity absolutely kills any security.
But let us suppose you are very lucky. You neither experienced biometrics failure, nor were your biometrics stolen, nor was your Aadhaar OTP mobile number changed by frauds. In that case does mobile OTP secure your Aadhaar transaction?
We might be tempted to answer "Yes" because use mobile OTP to secure banking & other transactions since long time, right? Yes we have used, but that was different situation, before Aadhaar. Now Aadhaar has killed your mobile OTP security for not just Aadhaar but other stuff too.
Sounds absurd? First key point to understand is, that SMS OTP by itself is not at all secure. I would like to write a technical article on that, but I am not sure how technical I should get when most audience didn't understand decimal counting also.
External Tweet loading...
If nothing shows, it may have been deleted
by @Stupidosaur view original on Twitter
So we will not look too deeply at the technical details. We will look at what standards bodies like @usnistgov are saying about using SMS OTP as an authentication/security factor.
This @usnistgov will be our friend in many discussions, whether for Aadhaar, SMS OTPs, or NPCI RuPay encryption and security. Here's a short intro. To explore more of course there is
Wikipedia en.wikipedia.org/wiki/National_…
and their own 'About NIST' page
nist.gov/about-nist
Wikipedia en.wikipedia.org/wiki/National_…
and their own 'About NIST' page
nist.gov/about-nist

It is a non-regulatory body so I guess it just tells you what is a good idea, but doesn't compel you to follow it. Like I say #DestroyTheAadhaar #BanDigitalElections for your own good but I can't force you to do it or to speak for it.
By setting standards & best practices it facilitates smooth interoperability of markets and also let's businesses and consumers have some rational basis to choose whether some product or service is of good standards or not [Will be useful when evaluating NPCI]. It doesn't force u
Now in middle of 2016 NIST released a bombshell document. It published draft version of Digital Identity Guidelines where it proposed to 'deprecate' the use of SMS for OTP. schneier.com/blog/archives/…
That @schneierblog post has a link to the draft but it no longer leads you to the draft version. That link now opens the final version. For draft version you might have to check archive.org and look for a 2016 version of same link.
Since many players in industry rely on SMS OTP (even mighty @google used that only,till few years ago) there was lot of uproar about NIST's draft guidelines. So they set up public feedback mechanism & wrote blog explaining why they want SMS OTP deprecated nist.gov/blogs/i-think-…
Their 2 main reasons in the blog to deprecate SMS OTP:
1) SMS can be sent to a VOIP or IP based recipient so it may not actually authenticate possession of a phone. So you access it by something you know (password to the voip/internet account) not something you have (phone).
1) SMS can be sent to a VOIP or IP based recipient so it may not actually authenticate possession of a phone. So you access it by something you know (password to the voip/internet account) not something you have (phone).
2) But second (and more important IMO) reason is that your SMS can actually be intercepted and read by villains even if it goes to your phone.
So the recent drama where some politician disclosed OTP on phone doesn't matter. It can be stolen without your knowledge.
So the recent drama where some politician disclosed OTP on phone doesn't matter. It can be stolen without your knowledge.

Apart from petty independent cybercriminals greedy for your money these SMS intercepting villains could be even 'respectable' entities like politicians or their minions, corporations particularly telcos and their employees, or even adversary nation states and their cyberarmies.
But as I said, there was lot of commotion in the industry at the idea of 'deprecating' SMS for OTP, so even after they explained what's 'deprecated', they eventually gave more concession. 

So instead of DEPRECATED status, the NIST Digital Identity Guidelines have given RESTRICTED status to SMS OTP. This is not as per their wishes of course but respecting the huge commotion they got in feedback from industry not yet ready to move from SMS pages.nist.gov/800-63-3/sp800…
[No I haven't slept off or forgotten this thread. So far I had only marked the above document as a reference without reading a lot of details in it. So you can read it too, or wait while I read and bring you important excerpts from it relevant to SMS OTP.]
Ok so let's see what the NIST guidelines say on SMS OTP. First of all it's an Out Of Band Authenticator (OOBA) like our old friend who loved Aadhaar but hated biometrics wanted us to use.
External Tweet loading...
If nothing shows, it may have been deleted
by @mitwa1126 view original on Twitter
Out of band authentication is nothing fancy. It needs user to authenticate by 2 channels at least which are not 'same band' of communication. Like you get OTP by out of band channel (SMS) and verify it by internet (main channel). You can read more fancy jargon of NIST if u like: 

They like to tell you more about each authentication process in terms of authenticators (you), verifiers (UIDAI for example) and related devices. Again they talk of out of band authentication. You can read all the yada yada if u want, but see highlighted part. SMS is sent by PSTN 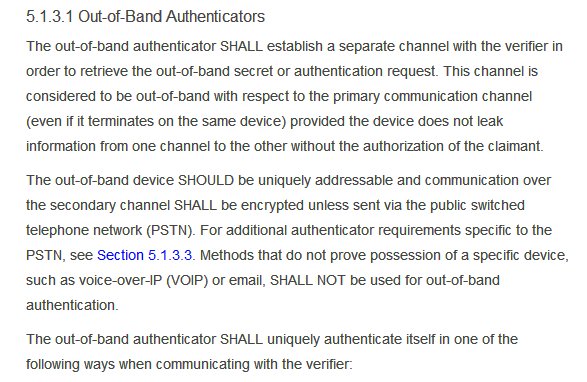
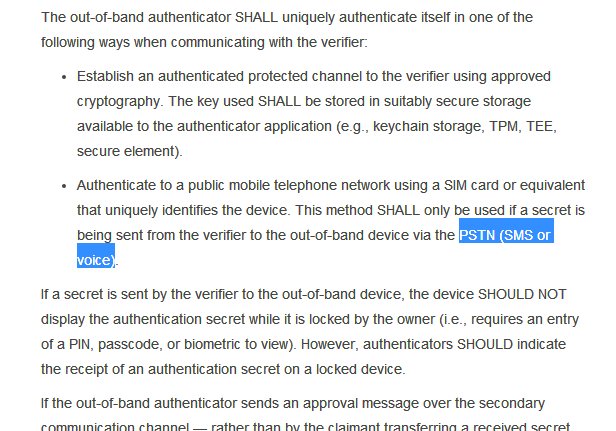


PSTN is nothing but public switched telephone network which includes mobile as well as some forms of landline (there is ISDN too). What you call 'mobile' is just end points of the phone connection carried over air waves instead of wire.
So while they provide you guidelines for using PSTN (SMS or voice OTP) authentication, do they want you to use it? No. It is RESTRICTED category 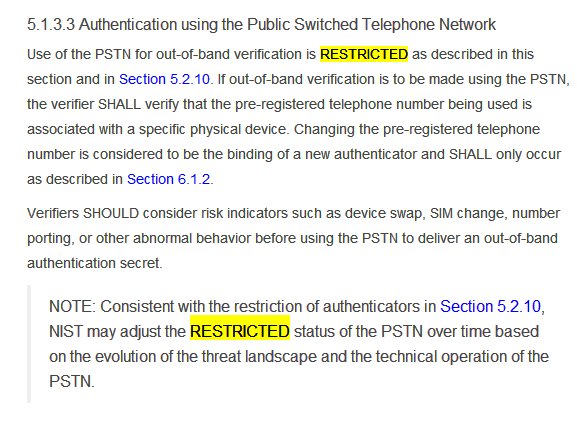

When RESTRICTED authentication factors like SMS OTP are used the implementing organizations must understand and acknowledge the risks and their potential increase over time, have mitigation methods and stop the use if risk to parties unacceptable. Do @CEo_UIDAI or @UIDAI care? 

And NIST correctly points out that 'subscribers', such as residents of India for Aadhaar or bank customers using OTP may not really understand risks involved with SMS OTP and so it asks @UIDAI, banks etc to take some steps if they must impose insecure SMS OTP. 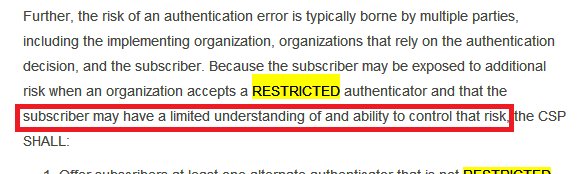

First NIST wants @ceo_uidai @uidai @narendramodi to provide users with an alternative method to SMS OTP. Have they provided? Not really, unless we consider mAadhaar TOTP. But how many have smartphones? Of course even bigger question for India is how many have basic mobile? 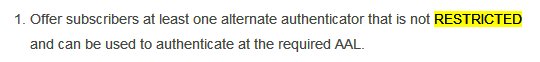

Of course even if u have a smartphone, mAadhaar and its TOTP are a joke as I have explained to @vijayshekhar @rssharma3 @ceo_uidai @nandannilekani and @29_ruchibhatia of @ETNOWlive. So really @UIDAI hasn't provided alternative to SMS as @usnistgov insists
External Tweet loading...
If nothing shows, it may have been deleted
by @Stupidosaur view original on Twitter
Further NIST would like @ceo_uidai (and banks etc) to issue a meaningful notice to Aadhaar users (and bank customers) that SMS OTP is pretty insecure so RESTRICTED by NIST (and of course tell us the alternatives. Banks may have some. @UIDAI has NONE) 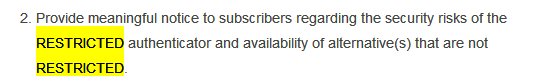

And in addition NIST would like @ceo_uidai to tell us some migration plan from RESTRICTED, insecure SMS OTP. LOL what 'migration plan' when the project is just starting out not even a legacy project and they can't even handle their existing mess? #DestroyTheAadhaar 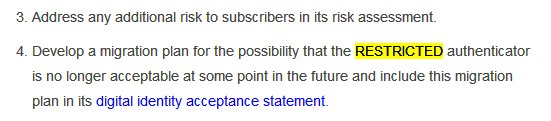

But some Aadhaar apologist may say, isn't biometrics itself another authentication factor other than SMS OTP? Well those guys might like to read what the same NIST document says about biometrics. Many of the same issues we have raised about Aadhaar. #DestroyTheAadhaar 

Because of above reasons NIST supports only limited use of biometrics and puts a lot of additional requirements, most of which #AadhaarFail. You can read screenshots or actual doc. I won't discuss detail cuz biometrics is not topic of this thread. But see first red mark point. 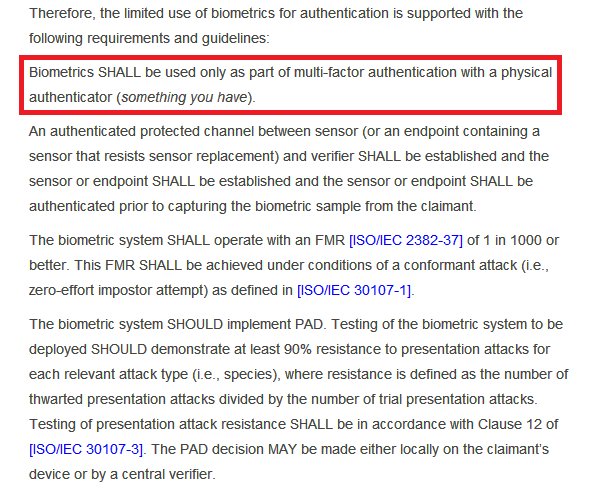

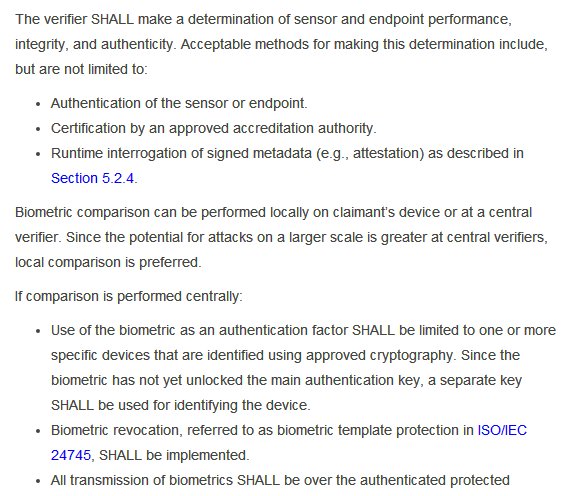
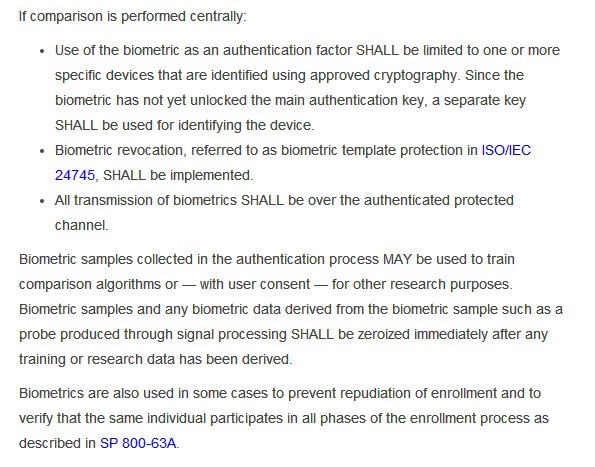




Of course that entire NIST document is interesting and you should read if you have time & interest. I'll link it again pages.nist.gov/800-63-3/sp800…
It also talks of 3-4 Authentication Assurance Levels.I am not sure which one @ceo_uidai @INCIndia @narendramodi intend @UIDAI to achieve
It also talks of 3-4 Authentication Assurance Levels.I am not sure which one @ceo_uidai @INCIndia @narendramodi intend @UIDAI to achieve
But I don't have time to study those AALs and I would be willing to bet @UIDAI fails even lowest level AAL1. But our main topic is SMS OTP not doing PhD in NIST Digital Identity Guidelines. So I'll close this sub-topic & the document after 1 last part...
That NIST document has 2 tables, about Authenticator threats and mitigation methods. I am not saying it's exhaustive list of auth security nor would an exhaustive auth threats list cover all kinds of security threats in digital world, but read it to arm yourself with good ideas. 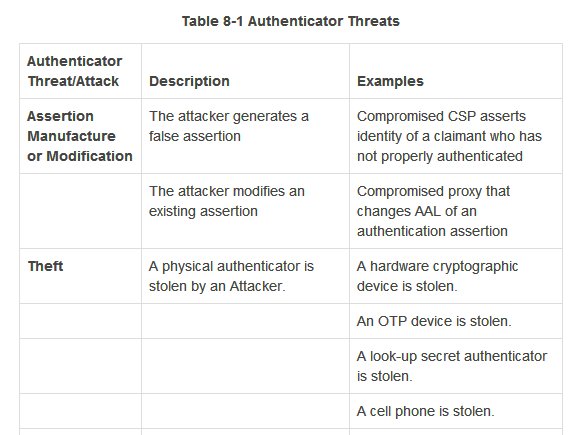
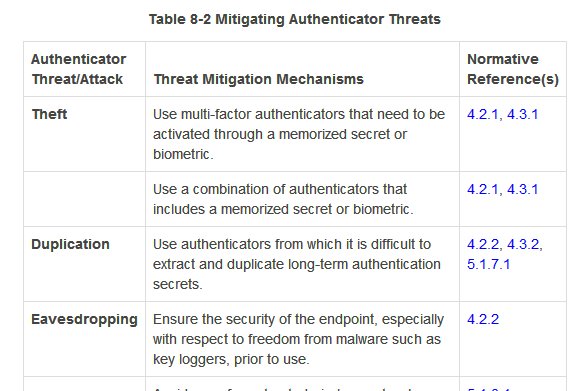


I won't replicate both tables. You can read in the doc. Some of it may be too technical, some of it may not be in your control but is meant for service providers. Use your judgement to ignore all that. But I'll highlight threats to SMS OTP from that, pertaining to our topic: 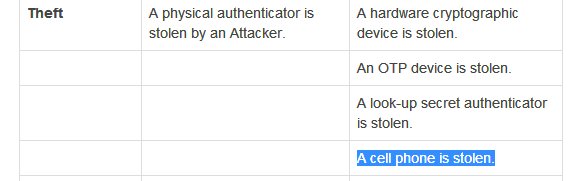
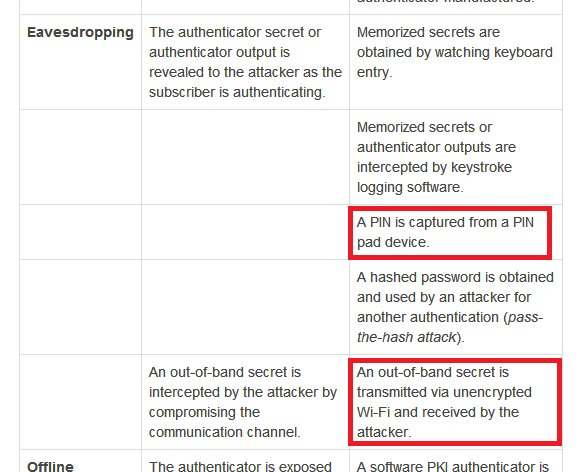
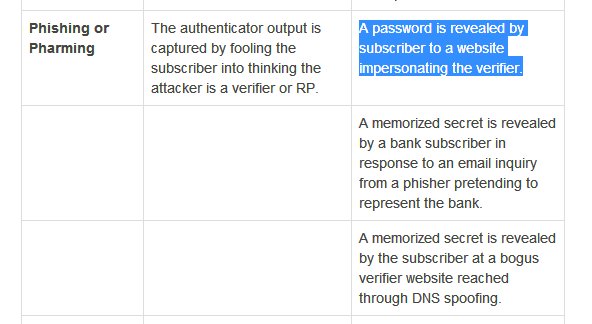
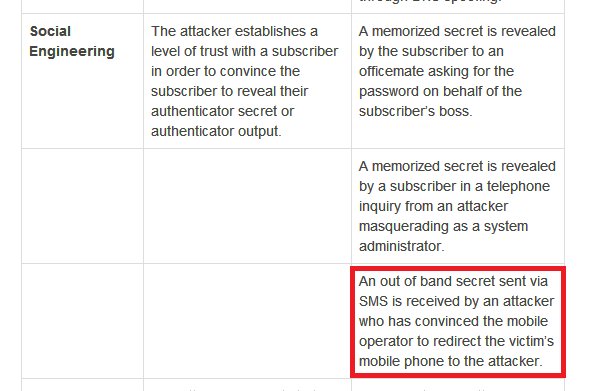




Continued...{my blue and red highlighting mean the same thing. I am just being shoddy) 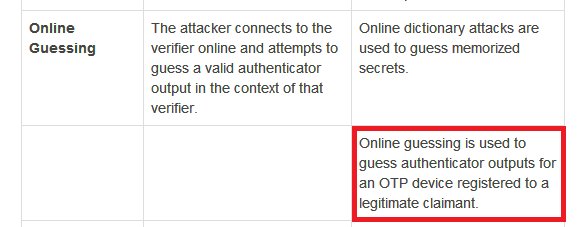
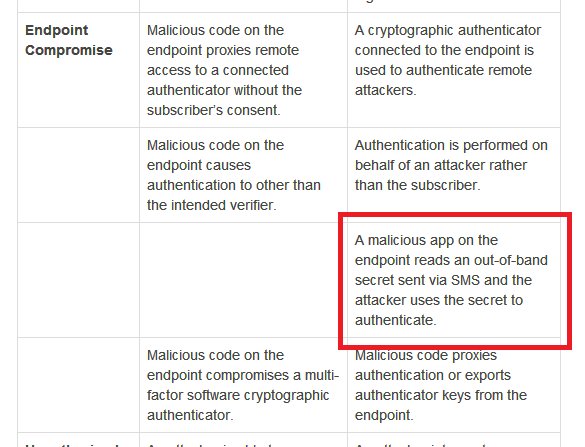
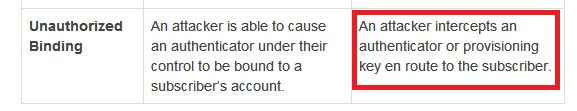



Okay I think last few image tweets may have been too tech heavy for some audiences. But our basic point, which lawyers can also firmly back by an authoritative body like @usnistgov is that SMS OTP security sucks. Every org is meant to discard it at the earliest.
So how can UIDAI which affects whole damn country, start off with such a hopeless security factor, that too as the sole security factor? This is nothing but an ugly setup for a largescale cyberwarfare on the country. All bank accounts gone. All admin haywire. #DestroyTheAadhaar
But wait, NIST document came last year and the threat is old,yet we have been using SMS OTP for many things including banking. So am I not being unnecessarily alarmist? Can we not use SMS OTP for stuff we had been using it for & also for Aadhaar? Nope. Aadhaar made it worse. How?
To understand how Aadhaar worsened SMS OTP security, we need to first understand what really made SMS OTP security work okayish before Aadhaar came even though technologically SMS was always pretty insecure.
Indians are a modern people and have been enthusiastically choosing digital technologies since many years, based on their economic conditions, market reach, convenience, needs and prudence, without any government coercion for Aadhaar or Digital India bullshit agendas of CIA.
Initial security of Indians for the digital services whether email or internet banking, depended on 1 factor of authentication that is password (something you know). Mobiles weren't too common.
While it was always recommended to have two factors of authentication, neither were service providers providing it, nor were users aware or keen to buy/use such additional factors of authentication as display tokens or USB dongles, etc.
As mobiles grew common, they became a two factor authentication (2FA) of choice, both for service providers and consumers. Service providers did not need to build much infra except SMS generating servers & users didn't need to buy anything more if they had even simplest mobile.
So everybody was happy, because hey 2FA for almost free! So if your first factor of authentication was compromised, you were still protected by other factor and cybercriminal couldn't get your account. Using the 2nd factor you could reset and regain control of first factor too.
Just because everyone was happy doesn't mean SMS was secure. Ignorance is bliss!
But first let's try to gauge when Indians started using mobile OTP. This 2008 doc is the earliest RBI doc I found mentioning SMS OTP. If you know it was earlier, do tell. rbi.org.in/Scripts/bs_vie…
But first let's try to gauge when Indians started using mobile OTP. This 2008 doc is the earliest RBI doc I found mentioning SMS OTP. If you know it was earlier, do tell. rbi.org.in/Scripts/bs_vie…

But even two year before that, in 2006, elaborate ways to attack and intercept mobile communications were being discussed. courses.cs.ut.ee/2006/crypto-se… 

One typical methods of attack, over airwaves is shown in the pic. Your mobile [User equipment(UE)/Mobile station(MS)]. Constantly checks signals from all base station towers near it and establishes contact with the one with strongest power. Attacker uses this phenomenon. How? 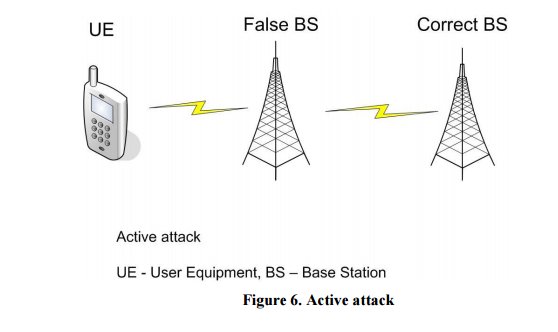

The attacker sends out similar signals as a base station, but with more power than the base station. So lured by this lollipop, your mobile phone happily gets 'kidnapped' by this fake base station created by attacker, leaving the frequency of the actual base station.
So now the attacker pretends to be the base station for your mobile, and talks with it. It will also talk to an actual base station, pretending to be your mobile. So the mobile as well as real base station talk to the fake station of attacker.
So the attacker can listen to both, talk to both, passing on some signals and messages between the two normally, while stopping or changing or at least reading whatever signal it wants. So good luck receiving an OTP ;)
Of course once such kidnap & spoofing done, attacker can do lot of things, like mess with control signals. modify security set up, force the mobile & base station to use a less secure signalling (by pretending that it doesn't know how to use better protocols), try decryption, etc
Now u may wonder if it would need specialists & hackers to spoof a base station to 'kidnap' your mobile as above. Fear not! Comporations are always around to help powerful people do evil for money. Harris Corp & few others offer such devices off the shelf. en.wikipedia.org/wiki/Stingray_…
We can take up Stingray and such devices in more detail later in this thread of another. For now just know that SMS OTP is pretty insecure in a large number of ways. Such man in middle attack is possible,encryption of various mobile protocol signals over air has been broken,
, even the SS7 protocol which is used to communicate between various service provider networks itself doesn't have solid security because initially it was assumed only few big trusted corps will use protocol so security doesn't need woven in it. Relied on 'security by obscurity'.
But now with such wide variety of mobile operators, SS7 protocol has become more common knowledge so other cybercriminals are also beginning to exploit it to drain banks accounts thehackernews.com/2017/05/ss7-vu…
Of course even if there are no cybercriminals, the telco itself could do SS7 attacks. What's stopping any of your current telcos who are anyway evil in many ways, and further under all kinds of pressures from politicians and (((Western Thugs))) and push evilly for Aadhaar too?
Even if the telco itself isn't evil and even if govt doesn't make evil use of telco infra, the SMS doesn't entirely travel on telephone network. It is stored at SMSC (Short message switching center) which may be run by the telco or even third party.
At SMSC your SMS is purely plaintext. No encryption, not even the kind of hackable encryption present on airwaves or the usual network encryption present on wired lines of the network. So any employee with access can see your SMS, no problem.
Beyond that, even a 'clone' of your SIM card can be created, where a few important keys of your SIM can be deciphered and copied into another blank SIM making the network think that it is your SIM. So it will receive or send your SMS and calls. kaspersky.com/blog/sim-card-…
And of course from same article as above, if someone can get hold of a carrier's SIM card database or special lookup tables of SIM card producer, large number of SIMs could be cloned. Good fun for cyberwarfare by foreign powers or their local EVM puppets and lackey mobile cos. 

Oh BTW you are being encouraged to get 4G (fancy name for LTE) or upgrade existing number to 4G for Digital India scam right? They can intercept or black out every call and text. Good luck with OTPs. theregister.co.uk/2016/10/23/eve…
Other than that of course there are social engineering attacks, SIM swap etc. Thief can make a mobile operator issue them a new SIM in place of yours.
We are getting carried away explaining various ways SMS OTP is absolutely insecure. I had said I won't. We can have detailed article/thread on the many ways. But have u really really understood that SMS OTP is ABSOLUTELY insecure if anyone at all tries to steal it? At least fav?
These SMS OTPs were technologically insecure even when RBI under CIA's EVM rigged Aadhaar scam UPA government started recommending it in 2008 (as I judged in quoted tweet). So why did our banking & other OPT based services not face severe cybercrime wave?
External Tweet loading...
If nothing shows, it may have been deleted
by @Stupidosaur view original on Twitter
Well to attack your OTP the attacker must have target, they must know what mobile number you are using for banking or any service they want to attack. Most of Indians were safe not because of fancy tech security of SMS but simply "security by obscurity".
In initial days of mobile, only your relatives, friends and acquaintances knew your mobile number. And if you used it for something or shared it with some other entities, it was only for most critical services like banking and maybe some govt things. Your mobile no. was obscure.
But gradually, mobile penetration as well as digital economy grew, even before Aadhaar, and Indians enthusiastically started participating in it (without government coercion).
So Indians started sharing their mobile number with grocery shop, carpenter, plumber (who now had mobiles!) and also with online stores, food delivery apps, email accounts etc etc. So many more had your data. As thug @NandanNilekani likes to say,India started growing 'data rich'.
That's just shitty euphemism for saying that your data privacy and obscurity was eroding. And India did not have any proper privacy laws so even if these people sold your mobile number & personal details, they faced no consequences. So they did. Surveillance capitalism.
Of course it was mostly 'innocent' like bombarding you with marketing SMS for their own services as well as selling numbers to others who would similarly like to bombard you with marketing.
And of course apart from actual sale, your details also kept getting exposed as these entities got 'hacked'. So data buyers and attackers had much more info about you such as which is your mobile number, and where you use it. Some of the hacks would involve bank details too.
So on one hand your mobile details became more and more available to malicious elements and at the same time more and more malicious elements started learning how to steal OTPs (some of the ways we saw above). So rise in OTP related crimes must be proportional to square of time.
Of course I don't know if one can find stats of cybercrimes due to OTP only but this graph from youthkiawaaz.com/2016/06/cyber-… is quite in line with my thoughts above. Sudden rise after 2008 (RBI doc with SMS OTP in 2008) and increasing non linearly, kinda like square functuion's graph. 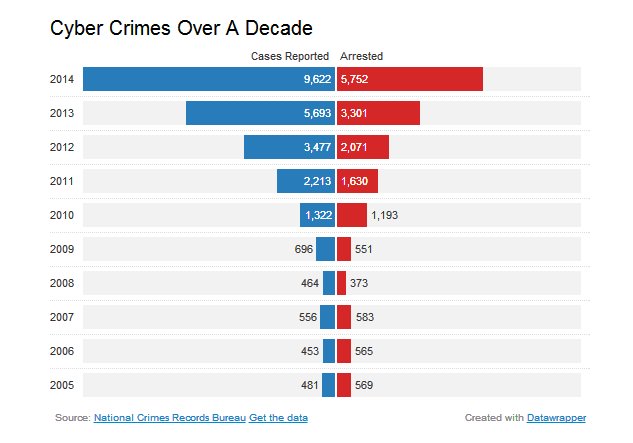

But did it mean that to protect their bank account, Indians should not have participated in mobile & digital economy at all? Not so. It was possible to bring back security by obscurity by keeping separate mobile numbers for different areas with different trust and criticality.
Of course this was more suitable for more well-off people but thankfully they were the ones more likely to participate in digital economy anyway because no evil force from CIA's EVM rigged thug govts. And to help creating such 'silos' even multi-SIM phones became more available.
Security by obscurity through multiple SIMs would be even more secure if you got the different SIMs by different KYC documents. In fact as @sunil_abraham says, in most developed nations you don't need KYC documents for mobile SIM.
But of course (((Western Thugs))) forced us to get SIM by KYC by fake excuses of terror etc which they themselves create, for many gains including getting to surveil us and making India 'data rich' as their puppet Nandu says. #DataIsTheNewOil
These fake terror attacks (including the parliament attack) of course happened under CIA's EVM rigged thug government. #SabMileyHueyHainJi.
So once we realize all these truths, #BanDigitalElections, get our govt back, we can get rid of this KYC for SIM nonsense.
So once we realize all these truths, #BanDigitalElections, get our govt back, we can get rid of this KYC for SIM nonsense.
But of course we have bigger problems at hand than KYC. Security by obscurity only comes from silos. Due to Aadhaar we can no longer have silos for mobiles. They want them all linked. That's how they are setting us up for cyberwar apart from Aadhaar itself being hopeless.
So maintaining silos is not only essential for your privacy and freedom but for your security itself. So when 'biggies' like @buzzindelhi cheer breaking of silos, are they nincompoops or traitorous villains you decide
External Tweet loading...
If nothing shows, it may have been deleted
by @buzzindelhi view original on Twitter
• • •
Missing some Tweet in this thread? You can try to
force a refresh




